
In this comprehensive guide, we will cover 100 common BGP interview questions and answers to help you prepare for a technical interview or exam.
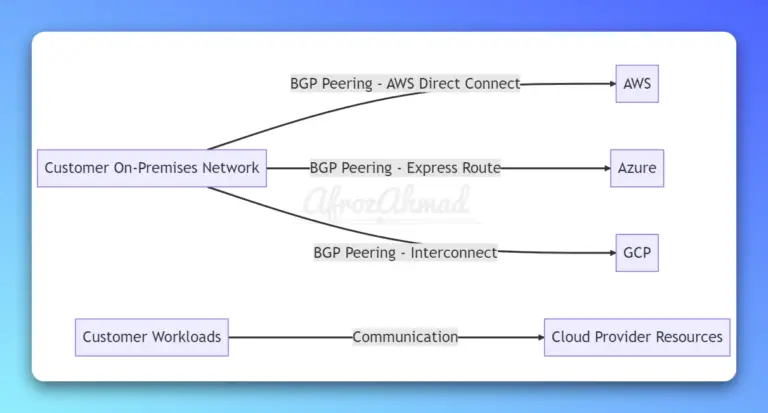
Discover how to use BGP in cloud Networking, covering interconnecting cloud networks to customers' on-premise network, connecting regions, internet routing, route aggregation, and ensuring high availability.
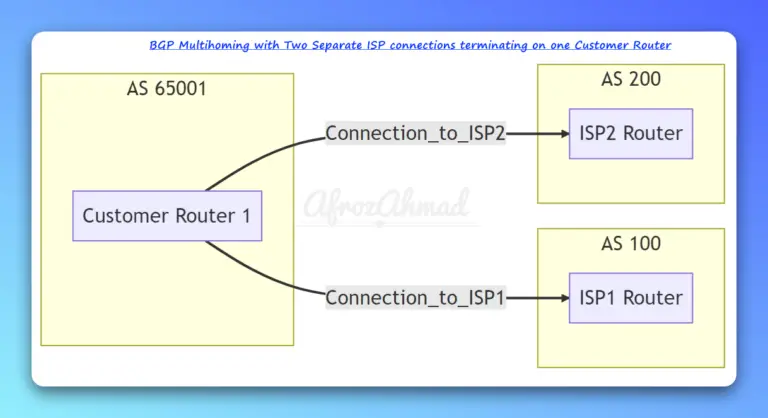
In this article, we'll discuss configuring Cisco BGP multihoming with two ISPs, along with the benefits, challenges, and best practices. We'll also provide Cisco configurations and verification commands for your reference.
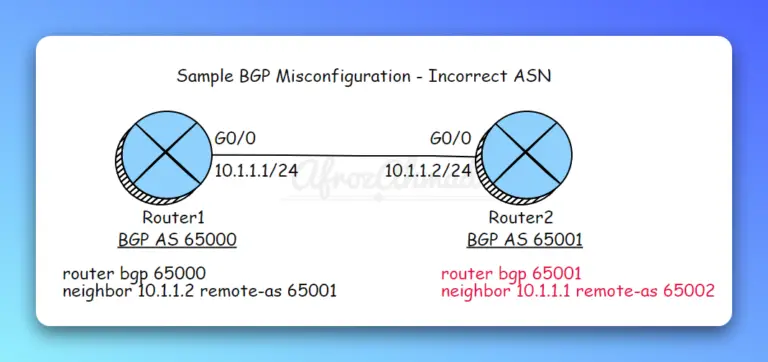
In this article, we'll go over 5 common BGP misconfigurations, exploring their impacts and addressing how to fix them.

In this article, we will discuss 14 BGP Security best practices. These best practices will help ensure that your network is protected from potential attacks and breaches.

In this comprehensive guide, we will cover everything you need to know about BGP regular expressions, or "regex," and how to use them effectively in your network.
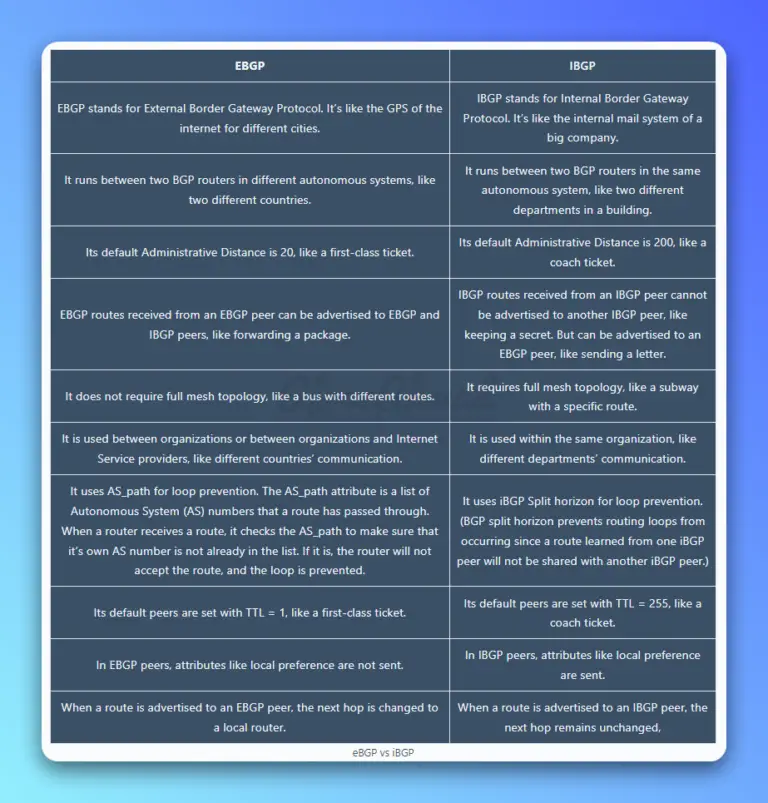
EBGP and IBGP are like your two best friends — one gets you out of the house and lets you explore the world (eBGP), while the other helps keep things running smoothly inside (iBGP). Today, we'll dive into the exciting topic of eBGP vs iBGP.
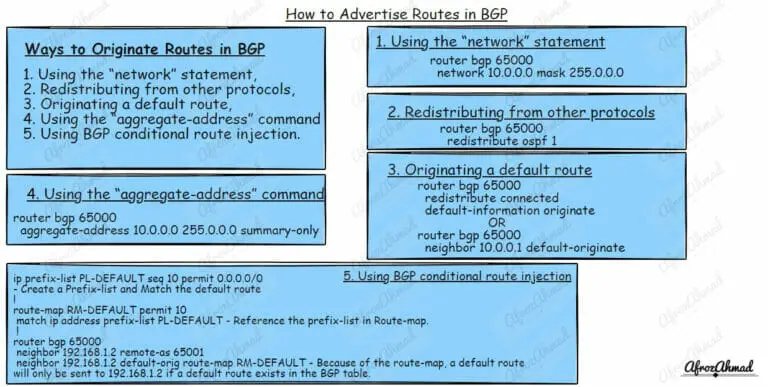
Master the art of BGP route advertisements and control your network like a pro. Learn how to advertise routes in BGP with our practical guide.
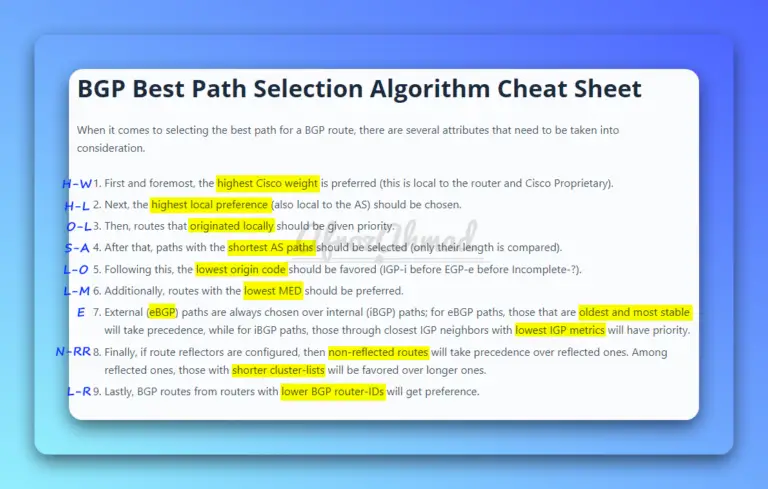
In this article, we'll take an in-depth look at BGP path attributes, the best path selection process, and its cheat sheet.
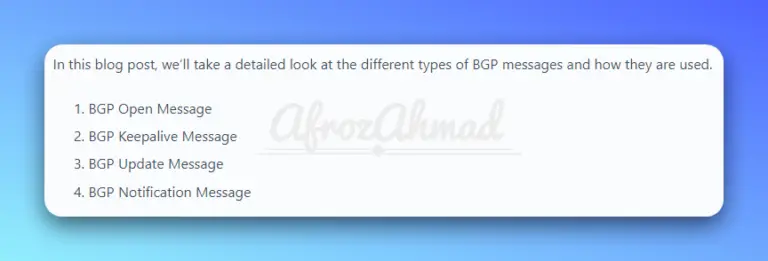
In this blog post, we'll take a detailed look at the different types of BGP messages and how they are used.










