OSPF /32 Issue in MPLS VPN Scenario: A Modern Troubleshooting and Automation Perspective
===========================
Recently, while collaborating with a colleague on an MPLS Layer 3 VPN deployment, we encountered a deceptively simple issue that caused considerable head-scratching. It turned out to be a classic OSPF loopback advertisement quirk, a reminder that even seasoned engineers can overlook fundamental protocol behaviors. The scenario was a great learning experience, one I believe is still highly relevant today, especially with the increasing complexity of network automation and validation.
Our lab setup replicated a common enterprise WAN scenario:
R1(CE)—-R3(PE)—R4(P)—–R5(PE)—-R2(CE)
In this topology:
- EIGRP was configured between the Customer Edge (CE) routers (R1, R2) and their respective Provider Edge (PE) routers (R3, R5). (Note: While EIGRP was used here for demonstration, modern MPLS L3VPN deployments typically favor BGP or OSPF for CE-PE routing due to enhanced interoperability and scalability across multi-vendor environments.)
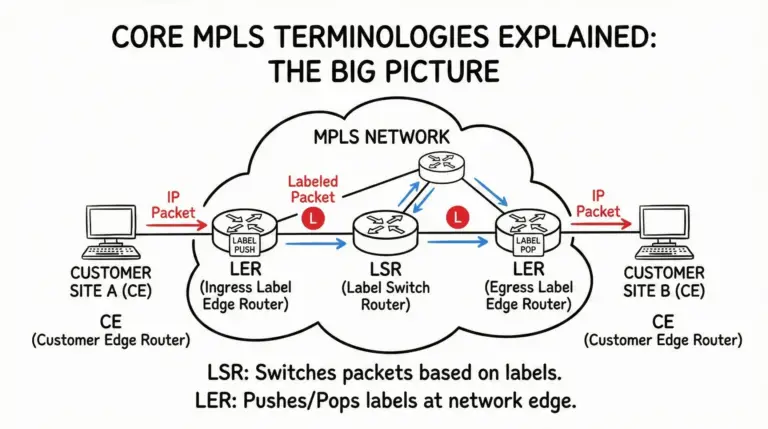
- OSPF was our chosen Interior Gateway Protocol (IGP) running across the MPLS backbone (between R3, R4, and R5). R4, the Provider (P) router, was not running BGP, as expected in a typical P-router role.
- We defined a VRF named “RED” with a Route Distinguisher (RD) of
100:1. Route Targets (RTs) for import and export were also set to100:1on both PE routers (R3 and R5). - Loopback interfaces were assigned IP addresses based on their device ID, e.g.,
1.1.1.1/24for R1,2.2.2.2/24for R2, and similarly for the P/PE routers. - BGP was correctly configured for VPNv4 and IPv4 address families, ensuring proper route exchange between the PE routers.
Everything appeared to be configured correctly and with high accuracy. The loopback routes were being advertised, and we could see them in the BGP VPNv4 tables and VRF routing tables on the PE routers. However, when we attempted to ping end-to-end between the CE routers, the pings consistently failed.
The Challenge: When Basic Connectivity Fails
We embarked on a comprehensive troubleshooting effort, systematically checking all layers of the MPLS VPN forwarding path. This involved a series of manual verifications, which, while still crucial, are increasingly being augmented by automated tools in modern NetDevOps workflows:
- BGP VPNv4 Routes: We verified that all VPNv4 routes were correctly received and marked as “best” at both PE routers.
R3# show ip bgp vpnv4 all
- VRF Routing Table: We confirmed that the routes for the remote CE network were properly installed in the VRF routing table.
R3# show ip route vrf RED
- MPLS Label Information Base (LIB) and Forwarding Information Base (LFIB): We inspected the MPLS tables to ensure labels were correctly assigned and forwarded.
R3# show ip mpls ldp bindings
R5# show ip mpls forwarding-table
- Cisco Express Forwarding (CEF) Table: Even the CEF tables, which dictate the actual forwarding decisions, looked correct.
R3# show ip cef
R3# show ip cef vrf RED 1.1.1.1 detail
Despite all these checks appearing normal, the ping continued to fail. This indicated a subtle but critical misconfiguration or protocol behavior that our standard “show” commands weren’t immediately highlighting at a granular level.
Uncovering the OSPF /32 Loopback Issue
After nearly two hours of deep-diving, we finally pinpointed the problem. The core issue lay in how OSPF was advertising the loopback interfaces on the PE routers:
I had configured the loopback interface on R3 with a /24 mask, intending for it to be advertised as a network segment:
R3# show run interface loopback 0
interface Loopback0
ip address 3.3.3.3 255.255.255.0
!
router ospf 1
log-adjacency-changes
network 3.3.3.0 0.0.0.255 area 0
However, when checking the routing table on the second PE router (R5), the 3.3.3.3 network from R3 was being advertised as a /32 host route, rather than the intended /24 network:
R5# show ip route
# ... (snip) ...
Gateway of last resort is not set
3.0.0.0/32 is subnetted, 1 subnets
O 3.3.3.3 [110/3] via 192.168.35.3, 00:03:55, FastEthernet1/0
This OSPF behavior is crucial: by default, OSPF treats loopback interfaces as host routes (/32) regardless of the configured subnet mask. This is true for many network operating systems, including modern Cisco IOS-XE (e.g., 17.12), Juniper Junos (e.g., 23.4), and Arista EOS (e.g., 4.31). While the IP address was reachable, the unexpected /32 advertisement prevented MPLS from correctly forwarding traffic for the broader /24 subnet or, more critically, caused mismatches in how BGP expected to resolve the next-hop for VPNv4 routes if it depended on the broader subnet.
Consequently, the MPLS forwarding table on R5 also reflected this /32 advertisement:
R5# show mpls forwarding-table
Local Outgoing Prefix Bytes tag Outgoing Next Hop
tag tag or VC or Tunnel Id switched interface
16 16 3.3.3.3/32 0 Fa1/0 192.168.35.3
# ... (other entries) ...
The Resolution: Correcting OSPF Loopback Advertisement
Recalling my OSPF studies, I remembered this specific behavior and its solutions:
1. Configure OSPF Network Type: The most robust solution for ensuring OSPF advertises the intended subnet for loopback interfaces is to explicitly define the OSPF network type on the loopback interface as “point-to-point.” This tells OSPF to treat the interface as if it were a point-to-point link, forcing it to advertise the actual subnet mask configured.
R3(config-if)# interface Loopback0
R3(config-if)# ip ospf network point-to-point
2. Use a /32 Mask for Loopback Interfaces: A simpler alternative, often used for PE/P router loopbacks that primarily serve as router IDs and BGP next-hops, is to simply configure them with a /32 mask from the outset. This aligns with OSPF’s default behavior and eliminates the discrepancy.
R3(config-if)# interface Loopback0
R3(config-if)# ip address 3.3.3.3 255.255.255.255
By implementing either of these changes on R3’s loopback, the OSPF advertisement on R5 correctly reflected the intended routing, MPLS forwarding tables updated, and our end-to-end ping immediately succeeded.
Modern Context and Best Practices for MPLS L3VPN
While the fundamental OSPF behavior remains constant, modern MPLS L3VPN deployments and network operations have evolved significantly: This evolution has led to more efficient routing techniques and greater scalability in large networks. To fully grasp these advancements, it’s crucial to revisit the foundational MPLS concepts explained in industry literature. Understanding these principles allows network engineers to optimize their configurations and enhance overall performance.
- Protocol Choice for CE-PE: As mentioned, BGP or OSPF are preferred over EIGRP for CE-PE routing to ensure multi-vendor compatibility, scalability, and better support for advanced features like BGP communities and policy control.
- Advanced Overlay Technologies: Beyond traditional MPLS VPN, many enterprises are now leveraging technologies like EVPN/VXLAN for data center interconnects and even for hybrid WAN environments, often combined with Segment Routing for traffic engineering and simplified control planes.
- Consistent Configuration: The importance of correctly defining VRFs, RDs, and RTs across all PE routers cannot be overstated. In multi-vendor environments (e.g., Cisco IOS-XE, Juniper Junos, Arista EOS, Nokia SR OS), strict adherence to RFCs and consistent configurations are paramount.
Leveraging Automation for MPLS VPN Verification and Troubleshooting
The experience highlights that even seemingly minor misconfigurations can have major impacts. In today’s complex network landscape, manual verification of every detail across dozens or hundreds of devices is impractical and error-prone. This is where network automation shines:
- Configuration Auditing: Tools like Ansible, Nornir, or custom Python scripts leveraging libraries such as Netmiko, NAPALM, or Scrapli can be used to automatically audit device configurations for best practices, such as ensuring loopback interfaces in OSPF are always configured with
/32masks or explicitly set toip ospf network point-to-point. - Automated State Verification: Instead of manually executing “show” commands, automation frameworks can collect operational state (BGP tables, VRF routes, MPLS forwarding entries, CEF information) programmatically via NETCONF/RESTCONF APIs or enhanced CLI scraping. This data can then be parsed, validated against expected states, and integrated into dashboards or alerting systems.
- Infrastructure as Code (IaC) and GitOps: By managing network configurations as code in a version control system like Git, and using CI/CD pipelines, engineers can ensure that proposed changes are validated (e.g., through linting or dry runs) before deployment. Post-deployment, automated tests can confirm the desired operational state, preventing issues like our OSPF /32 problem before they impact services.
- Intent-Based Networking and Observability: Modern network architectures are moving towards Intent-Based Networking, where network behavior is defined at a high level, and the system translates this intent into configurations. Coupled with robust observability frameworks using streaming telemetry (e.g., via gNMI/gRPC), engineers gain real-time insight into network health and can proactively detect deviations from the intended state.
Conclusion
This MPLS VPN scenario reinforced a timeless troubleshooting lesson: always check the simple things first before diving into complex rabbit holes. Even experienced engineers can overlook fundamental protocol behaviors. However, the true lesson for me was also the recognition that while manual diligence is essential, modern network automation tools and methodologies are critical for preventing, detecting, and resolving such issues at scale. By embedding automated configuration compliance, continuous validation, and robust observability into our NetDevOps pipelines, we can build more resilient, predictable, and compliant MPLS VPN infrastructures.
Stay vigilant, and keep automating!
- Telecom Network Infrastructure: Complete Guide to Components & Design - January 6, 2026
- TP-Link TL-SG108E vs Netgear GS308E: Budget Smart Switches - January 5, 2026
- MikroTik CRS305-1G-4S+ Review: The Ultimate Budget SFP+ Switch Guide - December 25, 2025


its really a good point to consider in MPLS -VPN
Yes offcourse , as we usually forget our basics and always try to rush in complex things,this
is one of the trailer 🙂