⚠️ Legacy Technology Notice: This article covers legacy Cisco transparent bridging with IRB using deprecated bridge-group commands from classic IOS. These commands do not work on modern IOS-XE or IOS-XR platforms. This content is preserved for historical reference and exam study purposes. For production networks in 2025, see the Modern Alternatives section below.
Understanding Layer 2 Bridging Over WAN
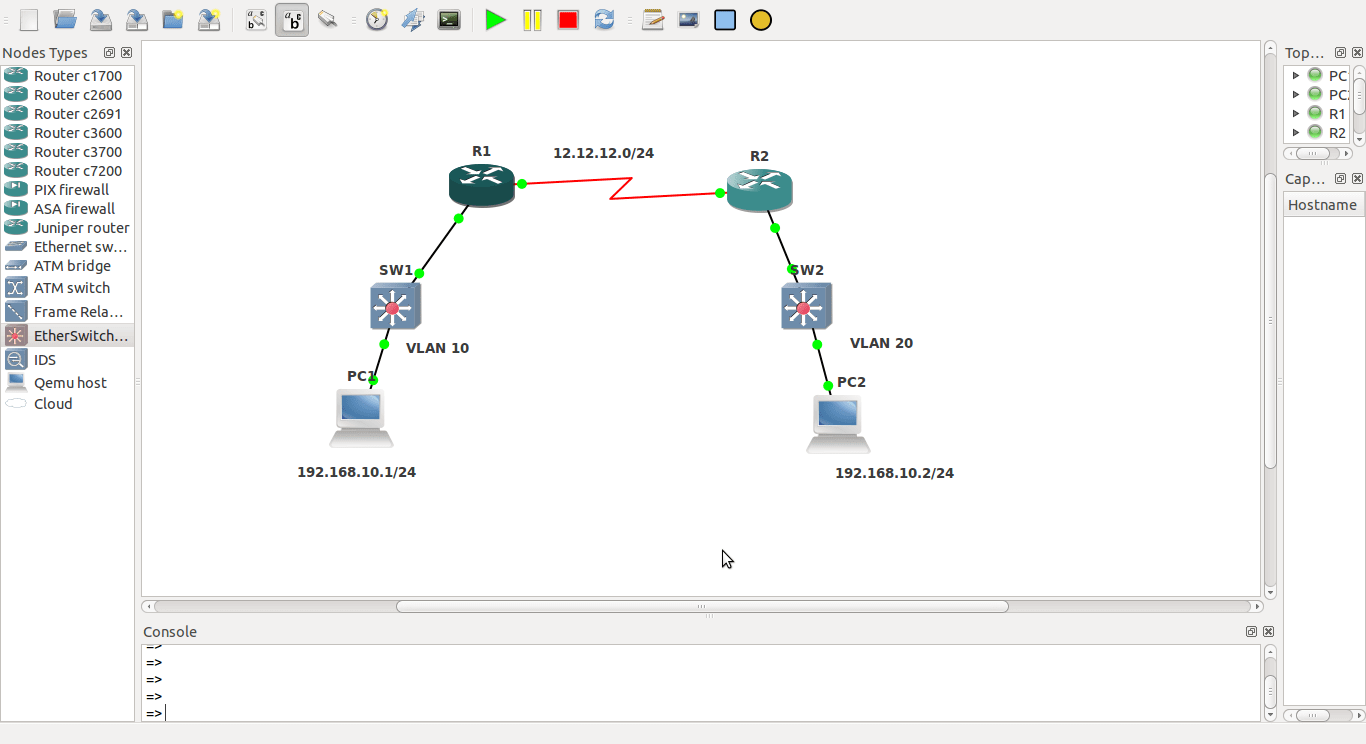
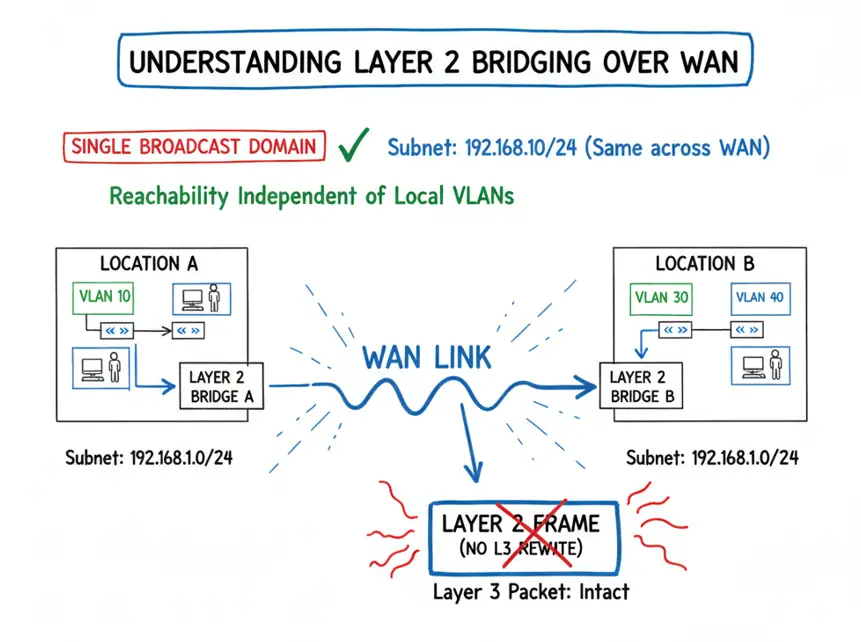
Bridging is straightforward in concept: we are NOT rewriting the Layer 3 packet, simply forwarding the Layer 3 information in a Layer 2 frame intact from one end to the other. This creates a single broadcast domain spanning multiple physical locations.
Today we’re discussing bridging the same subnet over WAN links. In this example, I’ve placed the subnet in different VLANs just to demonstrate that reachability doesn’t depend on the local VLANs used in the LAN environment.
Here I’ve assigned 192.168.10.1/24 to PC-1 in VLAN 10, while on the other side PC-2 has IP address 192.168.10.2/24 in VLAN 20.
Legacy IRB Configuration (Classic IOS Only)
We’re using IRB (Integrated Routing and Bridging) for this setup. IRB means we can bridge and route at the same time on the same interface.
⚠️ Important: The commands below work only on classic Cisco IOS 12.x/15.x. They are not supported on IOS-XE (Catalyst 9000 series, ASR 1000, Catalyst 8000V) or IOS-XR (ASR 9000, NCS 5500, 8000 series).
On Router-1 and Router-2:
bridge irb
bridge 1 protocol ieee
bridge 1 route ip
Then we assign appropriate interfaces into “bridge-group 1” on R1 and R2.
R1(config)#int fa0/0
R1(config-if)#bridge-group 1
R1(config-if)#int s0/0
R1(config-if)#bridge-group 1
R1(config-if)#end
R2(config)#int fa0/0
R2(config-if)#bridge-group 1
R2(config-if)#int s0/0
R2(config-if)#bridge-group 1
R2(config-if)#end
Then we create a Virtual BVI (Bridge Virtual Interface) on R1 and R2 to communicate with the routed Serial interface and assign the IP range used as default gateway for PC-1 and PC-2.
R1(config)#int bvi 1
R1(config-if)#ip add 192.168.10.254 255.255.255.0
R1(config-if)#end
R1#
R2(config)#int bvi 1
R2(config-if)#ip add 192.168.10.253 255.255.255.0
R2(config-if)#end
R2#
Other relevant configs are straightforward with no fancy configurations.
PC-1#sh ip route
Default gateway is 192.168.10.254
PC-2#sh ip route
Default gateway is 192.168.10.253
PC-1#sh run int fa0/0
interface FastEthernet0/0
ip address 192.168.10.1 255.255.255.0
no ip route-cache
duplex auto
speed auto
end
PC-2#sh run int fa0/0
interface FastEthernet0/0
ip address 192.168.10.2 255.255.255.0
no ip route-cache
duplex auto
speed auto
end
Verification Commands
Wait for MAC address learning to complete, then issue the command “show bridge 1 verbose” on R1 and R2. This is a very helpful command in bridging scenarios.
R1#sh bridge 1 verbose
Total of 300 station blocks, 297 free
Codes: P – permanent, S – self
BG Hash Address Action Interface VC Age RX count TX count
1 00/0 c201.080a.0000 forward Serial0/0 – 2 11 9
1 00/1 c205.080a.0000 forward Serial0/0 – 1 13 10
1 00/2 c204.080a.0000 forward FastEthernet0/0 – 1 26 18
Flood ports (BG 1) RX count TX count
FastEthernet0/0 3 3
Serial0/0 3 3
The configuration looks healthy so far. Let’s check the other side R2.
R1#sh arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.10.1 8 c204.080a.0000 ARPA BVI1
Internet 192.168.10.254 – c200.080a.0000 ARPA BVI1
R2#sh bridge 1 verbose
Total of 300 station blocks, 297 free
Codes: P – permanent, S – self
BG Hash Address Action Interface VC Age RX count TX count
1 00/0 c200.080a.0000 forward Serial0/0 – 4 5 4
1 00/1 c205.080a.0000 forward FastEthernet0/0 – 3 19 14
1 00/2 c204.080a.0000 forward Serial0/0 – 3 20 15
Flood ports (BG 1) RX count TX count
FastEthernet0/0 3 3
Serial0/0 3 3
R2#sh arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.10.2 9 c205.080a.0000 ARPA BVI1
Internet 192.168.10.253 – c201.080a.0000 ARPA BVI1
Here we can see MAC addresses being learned from both FastEthernet 0/0 and Serial 0/0. Let’s run our final verification command from PC-1, crossing the WAN links through R1 and R2 to reach PC-2.
PC-1#ping 192.168.10.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/15/32 ms
PC-2#trace 192.168.10.1
Type escape sequence to abort.
Tracing the route to 192.168.10.1
1 192.168.10.1 44 msec * 20 msec
Indeed we are successful in bridging LAN over the WAN.
⚠️ Critical Security and Design Warnings
Before implementing any Layer 2 extension over WAN, understand these significant risks:
Broadcast Storm Risks: A broadcast storm at one site will propagate through WAN links, potentially crippling all connected sites simultaneously. Unlike local LANs, recovery is complex when multiple geographically distributed locations are affected.
Spanning Tree Vulnerabilities: STP failures, misconfigurations, or unidirectional link issues can create loops spanning multiple sites, causing network-wide outages. Troubleshooting is significantly more difficult across WAN links.
Security Exposure: Extending Layer 2 domains across WANs increases attack surface. Attackers exploiting Layer 2 vulnerabilities at one location can impact all sites in the bridged domain.
Lack of Segmentation: All sites share the same broadcast domain, eliminating network segmentation benefits and making compliance with security frameworks more challenging.
Best Practice: Modern network design strongly favors Layer 3 connectivity between sites with Layer 2 extension used only when absolutely necessary for specific applications (VM mobility, disaster recovery).
Modern Alternatives for L2 WAN Extension (2025)
For production networks today, use these technologies instead of legacy transparent bridging:
1. VXLAN with EVPN (Industry Standard)
What it is: VXLAN (Virtual Extensible LAN) encapsulates Layer 2 frames in UDP/IP packets, while EVPN (Ethernet VPN) provides the BGP-based control plane for MAC address learning and distribution.
Key Benefits:
- Supports up to 16 million network segments (vs 4,096 VLANs)
- Multi-vendor interoperability (Cisco, Arista, Juniper, Dell, HPE)
- Massive scalability for data center and cloud environments
- Built-in multi-tenancy and segmentation
- Leverages IP routing features (ECMP, fast reroute) for resilience
- Seamless VM/container mobility across sites
When to use: Large-scale data center interconnects, cloud-native environments, multi-vendor networks, service provider networks.
Platforms: Cisco Nexus 9000, Catalyst 9000 (IOS-XE), ASR 9000 (IOS-XR), and most modern datacenter switches.
2. Cisco OTV (Overlay Transport Virtualization)
What it is: Cisco-proprietary technology that encapsulates Ethernet frames into IP packets for Layer 2 extension across data centers.
Key Benefits:
- Simpler configuration compared to VXLAN EVPN
- Built-in loop avoidance (no STP spanning sites)
- Native multihoming support
- MAC address distribution via IS-IS control plane
- Works over any IP network (MPLS, Internet, private WAN)
- Rapid deployment for Cisco-centric environments
When to use: Enterprise data center interconnect, disaster recovery scenarios, active/active data center architectures with Cisco infrastructure.
Limitation: Cisco-only solution; not suitable for multi-vendor environments.
3. MPLS-based L2VPN (Service Provider)
What it is: VPLS (Virtual Private LAN Service) or E-LAN services provided by carriers over MPLS networks.
When to use: When purchasing managed Layer 2 connectivity from service providers, legacy MPLS environments.
Modern IOS-XE/XR Bridge-Domain Configuration
If you need IRB functionality on modern platforms, use bridge-domain instead of the legacy bridge-group commands:
Modern IOS-XE Example (Catalyst 8000V, 9000 series):
interface GigabitEthernet0/0/1
no ip address
bridge-domain 10
interface GigabitEthernet0/0/2
no ip address
bridge-domain 10
interface BVI10
ip address 192.168.10.254 255.255.255.0
This provides the same Layer 2 bridging with Layer 3 routing functionality as the legacy IRB configuration, but uses modern, supported commands.
Historical Context: When Was This Used?
The transparent bridging and legacy IRB configuration shown in this article was commonly deployed in:
1990s – Early 2000s: Frame Relay, ATM, and leased-line WAN networks where Layer 2 extension was necessary but modern alternatives didn’t exist.
Pre-MPLS Era: Before MPLS L2VPN services became standard, transparent bridging was one of the few options for extending LANs across WANs.
Classic IOS Peak: IOS 12.x and early 15.x releases supported these commands extensively on routers like the 2800, 3800, and 7200 series.
Transition Period (2010-2015): Gradual migration to VPLS, OTV, and eventually VXLAN as data center fabrics evolved.
Today (2025): Legacy IRB with bridge-group commands is relevant primarily for:
- Maintaining legacy networks still running classic IOS
- Certification exam study (CCIE, CCNP legacy tracks)
- Understanding historical network design evolution
- Educational purposes in academic environments
Summary
We successfully demonstrated bridging LAN over WAN using legacy Cisco IRB configuration. While this configuration worked perfectly in the classic IOS era, modern networks should use VXLAN with EVPN or Cisco OTV for Layer 2 extension requirements.
The concepts learned here remain valuable for understanding Layer 2/Layer 3 integration, but the specific commands are no longer supported on current platforms. Always consult current Cisco documentation for your specific platform when implementing production configurations.
Key Takeaways:
- Legacy
bridge-groupcommands are deprecated on IOS-XE/XR - Modern platforms use
bridge-domainfor similar functionality - L2 WAN extension has significant security and operational risks
- VXLAN/EVPN and OTV are the recommended modern alternatives
- This configuration has historical and educational value
Happy learning about network evolution! 🌉
- Managing Overlapping Private IPs in Multi-Client Site-to-Site VPNs: Best Practices? - November 7, 2025
- Epson EpiqVision Flex CO-W01 Projector Review - February 21, 2025
- How to Log in to Your Netgear Router - January 17, 2025

Excellent weblog here! Also your website a lot up very fast! What host are you the use of? Can I am getting your affiliate link to your host? I want my website loaded up as fast as yours lol
Try to use excerpts and let me know..