Virtual Router Redundancy Protocol (VRRP) is a First Hop Redundancy Protocol (FHRP) that provides automatic default gateway backup for hosts on a local network. By creating a single virtual router from a group of physical routers, VRRP ensures that user traffic can continue to flow even if their primary gateway router fails.
The modern version of the protocol, VRRPv3, is an open standard defined in RFC 5798, which supports both IPv4 and IPv6. This RFC makes the previous version, VRRPv2 (RFC 3768), obsolete. In this guide, we’ll focus on configuring VRRPv3 on Cisco devices to build a resilient and fault-tolerant network.
You can also check out our deep dive on the similarities and differences between VRRP, HSRP, and GLBP.
VRRP Quick Start: Basic Cisco IOS XE Configuration
For those who need a fast solution, here is a minimal working configuration for a primary (Master) and backup router in a VRRP group. This example assumes you want Router 1 to be the primary gateway.
Router 1 (Primary/Master) Configuration
interface GigabitEthernet0/0/0
description Link to LAN
ip address 192.168.1.2 255.255.255.0
vrrp 10 ip 192.168.1.1
vrrp 10 priority 110
vrrp 10 preempt
Router 2 (Backup) Configuration
interface GigabitEthernet0/0/0
description Link to LAN
ip address 192.168.1.3 255.255.255.0
vrrp 10 ip 192.168.1.1
! Priority is default 100, which is lower than R1
To verify, use the command show vrrp brief on both routers. Router 1 should show its state as “Master,” and Router 2 should show its state as “Backup.”
Understanding Key VRRP Concepts
To configure VRRP effectively, it’s important to understand its core components and behaviors.
VRRP Roles: Master and Backup
In a VRRP group, routers participate in an election to determine their roles. The router with the highest priority is elected as the **Master Router**. This router is responsible for forwarding packets sent to the virtual IP address. All other routers in the group become **Backup Routers**, which monitor the state of the Master and are ready to take over if it fails.
Virtual IP and MAC Addresses (IPv4 & IPv6)
The Master router owns the virtual IP address and responds to ARP or Neighbor Discovery requests for it. VRRP uses a standardized virtual MAC address format:
- IPv4: The virtual MAC address is
0000.5e00.01XX, whereXXis the VRRP group number in hexadecimal. VRRP advertisements are sent to the multicast address224.0.0.18using IP protocol 112. - IPv6: The virtual MAC address is
0000.5e00.02XX, whereXXis the VRRP group number. Advertisements are sent to the multicast addressFF02::12.
VRRP Priority and Preemption
Priority determines which router becomes the master. The priority value can be set from 1 to 254, with a default of 100. The router with the highest priority wins the election. If two routers have the same priority, the one with the higher primary IP address on its VRRP interface becomes the master.
Preemption is enabled by default in VRRP. This means if a router with a higher priority comes online, it will automatically take over the master role from a lower-priority router. You can disable this behavior with the no vrrp preempt command if you prefer the failover to be less disruptive and manually controlled.
VRRP Timers and Advertisements
The Master router sends VRRP advertisements to the Backup routers to signal that it is still active. By default, these are sent every 1 second. If the Backup routers don’t hear from the Master within a calculated period (the Master Down Interval), one of them will assume the Master role.
While the VRRP standard’s default timer is 1 second, many vendors, including Cisco, offer vendor-specific extensions for sub-second (millisecond) timers. Using these can provide faster failover but may impact interoperability with devices from other vendors. Always test sub-second timer configurations in a lab environment before deploying in production.
How to Configure VRRP on Cisco Devices (Detailed Steps)
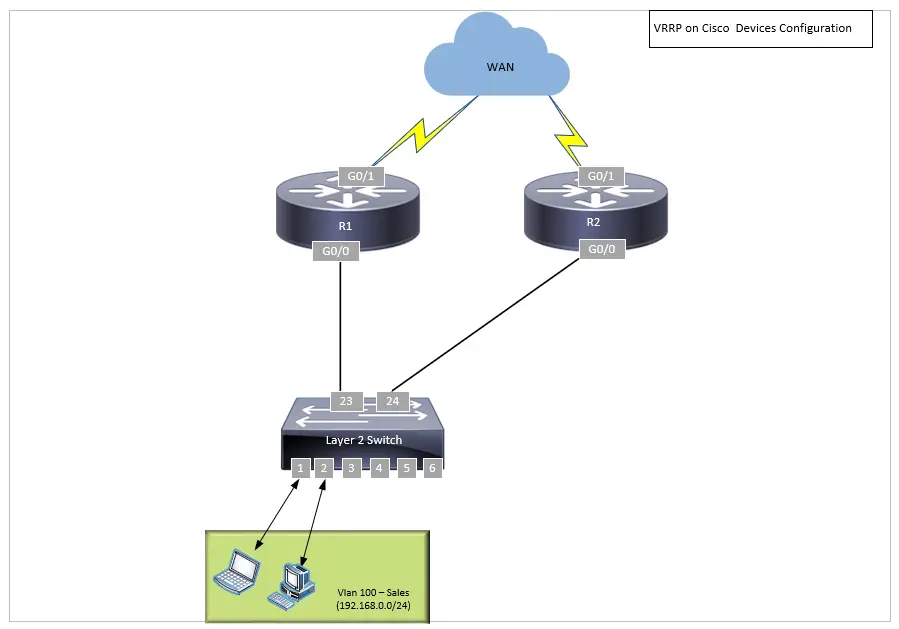
Let’s look at a more detailed configuration example that demonstrates load sharing across two subnets using two VRRP groups. The VRID (Virtual Router Identifier) can range from 1 to 255. While the protocol supports up to 255 groups, the practical per-interface limit can vary by platform; modern Cisco IOS XE devices often support dozens to hundreds of groups per interface.
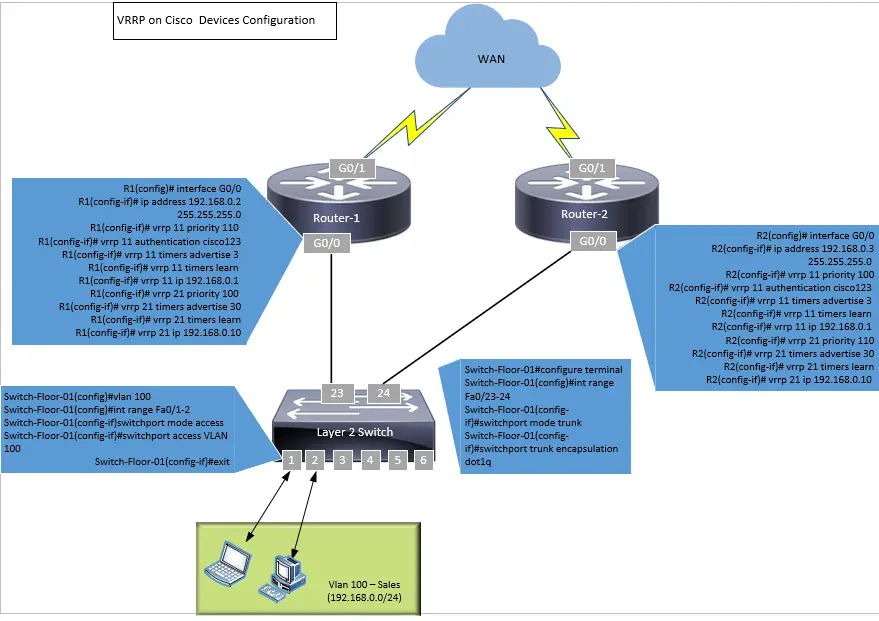
Example: IPv4 VRRP Configuration
Router 1 Configuration
! R1 is Master for VLAN 10 (192.168.0.1) and Backup for VLAN 20 (192.168.0.10)
R1(config)# interface GigabitEthernet0/0
R1(config-if)# ip address 192.168.0.2 255.255.255.0
! --- VRRP Group 11 ---
R1(config-if)# vrrp 11 priority 110
R1(config-if)# vrrp 11 preempt
R1(config-if)# vrrp 11 ip 192.168.0.1
! --- VRRP Group 21 ---
R1(config-if)# vrrp 21 priority 100
R1(config-if)# vrrp 21 ip 192.168.0.10
Router 2 Configuration
! R2 is Backup for VLAN 10 (192.168.0.1) and Master for VLAN 20 (192.168.0.10)
R2(config)# interface GigabitEthernet0/0
R2(config-if)# ip address 192.168.0.3 255.255.255.0
! --- VRRP Group 11 ---
R2(config-if)# vrrp 11 priority 100
R2(config-if)# vrrp 11 ip 192.168.0.1
! --- VRRP Group 21 ---
R2(config-if)# vrrp 21 priority 110
R2(config-if)# vrrp 21 preempt
R2(config-if)# vrrp 21 ip 192.168.0.10
Example: IPv6 VRRP Configuration
Configuring VRRPv3 for IPv6 is very similar. You must first enable IPv6 routing and then define the virtual IPv6 address for the group.
Router 1 IPv6 Configuration
! Enable IPv6 routing globally
R1(config)# ipv6 unicast-routing
! Configure the interface
R1(config)# interface GigabitEthernet0/0
R1(config-if)# ipv6 address 2001:DB8:0:1::2/64
R1(config-if)# vrrp 15 address-family ipv6
R1(config-if-vrrp)# priority 110
R1(config-if-vrrp)# address 2001:DB8:0:1::1
Enhancing Redundancy with VRRP Object Tracking
What happens if the master router’s LAN interface is up, but its connection to the WAN fails? VRRP alone won’t detect this, and traffic will be black-holed. Object tracking solves this problem. You can configure VRRP to monitor an object, like the line protocol of an uplink interface or an IP route, and dynamically decrease its priority if that object goes down.
This allows a backup router with a healthy WAN connection to take over the master role, ensuring traffic can still reach its destination.
Object Tracking Configuration Example
R1 Object Tracking WAN interface
! 1. Create a track object to monitor the WAN interface's line protocol
R1(config)# track 11 interface GigabitEthernet0/1 line-protocol
! 2. Apply the track object to the VRRP group
R1(config)# interface GigabitEthernet0/0
R1(config-if)# vrrp 11 track 11 decrement 20
Securing VRRPv3
Unlike older versions, VRRPv3 (RFC 5798) removed in-protocol authentication. The reliance on simple text or MD5 authentication was considered insufficient. Instead, security for VRRPv3 messages should be provided by other mechanisms.
- IPsec Authentication Header (AH): The recommended method is to use IPsec in transport mode with the Authentication Header (AH) protocol. This provides robust, per-packet authentication and integrity for VRRP advertisements between trusted routers.
- Infrastructure ACLs (iACLs): You can apply access control lists to your router interfaces to permit VRRP traffic (IP protocol 112) only from the known IP addresses of other legitimate VRRP routers in the group. This prevents unauthorized devices from participating in the VRRP election.
Verification and Troubleshooting Commands
Once configured, you need to verify VRRP is operating as expected. These commands are essential for verification and troubleshooting.
show vrrp brief: The best first command. Displays a summary of all VRRP groups, their virtual IP, state (Master/Backup/Init), and priority.show vrrp: Provides detailed information for each VRRP group, including timers, preemption status, master router IP, and virtual MAC address.show track: Crucial for troubleshooting object tracking. Shows the status of all tracked objects (Up/Down) and which clients are using them.debug vrrp all: Use with caution in a production network. This command shows real-time VRRP events, state changes, and errors, which is invaluable for diagnosing complex issues.
Test Your Knowledge
Ready to see what you’ve learned? Take our short quiz to solidify your understanding of VRRP.
Conclusion
In this post, we’ve updated our understanding of VRRP to focus on the current VRRPv3 standard. We covered the core concepts, provided detailed configuration examples for both IPv4 and IPv6, and explored advanced features like object tracking and modern security practices. With this knowledge, you can confidently implement a robust first-hop redundancy solution on your Cisco network.
I hope you found this guide helpful. Thank you for reading, and please share it with others who may be looking for up-to-date information on VRRP configuration.
Frequently Asked Questions About VRRP
Is VRRP a Layer 2 or Layer 3 protocol?
VRRP is a Layer 3 protocol. It provides redundancy for the IP gateway address, which is a Layer 3 function. It uses its own IP protocol (112) and sends packets to a Layer 3 multicast address to communicate.
How does the VRRP protocol work?
A group of routers running VRRP elect a single ‘Master’ router based on priority. This Master router handles all traffic sent to a shared ‘virtual’ IP address. The other ‘Backup’ routers monitor the Master. If the Master router fails, the highest-priority Backup router transitions to become the new Master, taking over the virtual IP and ensuring traffic continues to flow with minimal interruption.
Is VRRP a Cisco proprietary protocol?
No, VRRP is not Cisco proprietary. It is an open standard defined by the IETF in RFC 5798. This allows for interoperability between networking equipment from different vendors, although some features like millisecond timers may be vendor-specific extensions.
What is the difference between VRRPv2 and VRRPv3?
The main difference is that VRRPv3 (RFC 5798) adds support for IPv6, whereas VRRPv2 (RFC 3768) only supports IPv4. VRRPv3 also removed the built-in authentication mechanism, recommending the use of IPsec for security instead.
- Telecom Network Infrastructure: Complete Guide to Components & Design - January 6, 2026
- TP-Link TL-SG108E vs Netgear GS308E: Budget Smart Switches - January 5, 2026
- MikroTik CRS305-1G-4S+ Review: The Ultimate Budget SFP+ Switch Guide - December 25, 2025