Managing private IP addresses across many client networks is a common headache for service providers. When you set up secure connections, like site-to-site VPNs, to gather data from multiple companies, you quickly run into a big problem: what if two clients use the same private IP addresses? This isn’t just a hypothetical issue; it’s a real-world challenge that can disrupt services, complicate network management, and slow down client onboarding. Let’s explore why this happens and look at practical ways to keep everything running smoothly.
Step-by-Step Guide: Best Practices for Overlapping Private IPs in Multi-Client VPNs
Dealing with overlapping IP addresses across many client VPNs requires careful planning. Here’s a detailed look at strategies and best practices for service providers.
The Core Challenge: IP Collisions
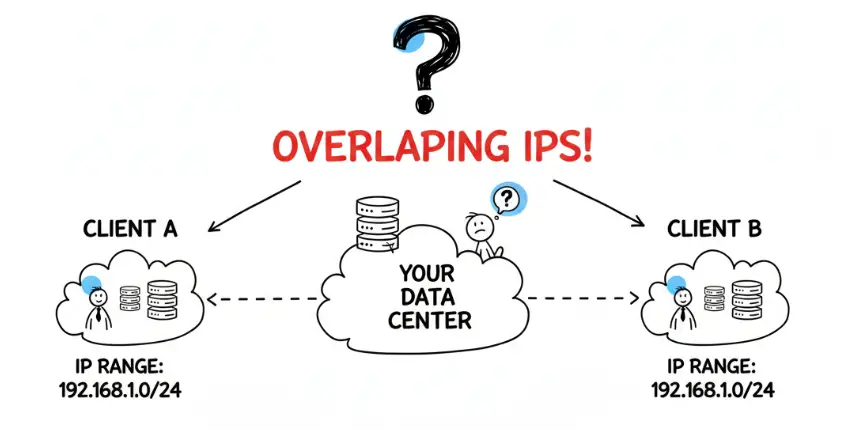
Private IP address ranges, such as 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16, are very popular. Many organizations use these default settings for their internal networks.
When you connect to multiple clients, and they all use the same or overlapping private IP ranges, your central network faces a conflict. It won’t know which client’s 192.168.1.10 it should send data to.
This problem grows significantly as you add more clients. The chance of an IP address collision increases with every new VPN tunnel you establish.
Solution 1: Client-Side Network Address Translation (NAT)
This approach asks your client to translate their private IP addresses into a unique, non-overlapping range before the traffic enters your VPN tunnel.
For example, a client with devices at 192.168.1.0/24 might NAT these addresses to a specific range like 10.X.Y.0/24 that you assign to them. Your network then sees only the unique 10.X.Y.Z range.
Pros: This method places the complexity on the client’s network. Your central network remains simpler, as it doesn’t need to manage complex NAT rules for incoming client traffic.
It can reduce your team’s workload related to NAT configuration and tracking. Your side of the VPN connection is cleaner and easier to manage.
Cons: This often fails in real-world scenarios. Many smaller clients lack the network engineering staff or expertise to correctly configure and maintain NAT.
If clients have hundreds of devices or frequent IP changes, managing NAT rules becomes a huge burden for them. This can delay onboarding and create ongoing support challenges.
Clients might not own public IP addresses to use for this NAT. Even if they use a private range for NAT, ensuring uniqueness across all clients can still be a coordination challenge.
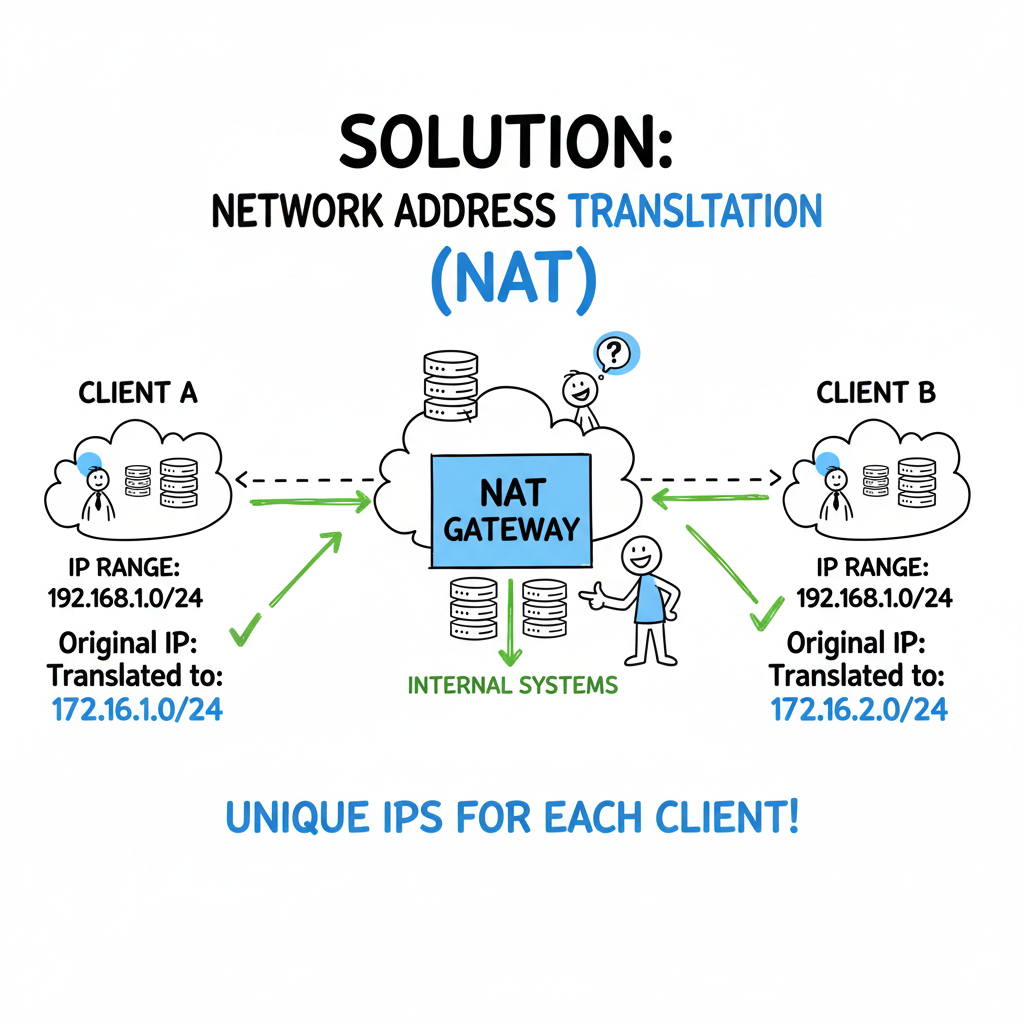
Solution 2: Provider-Side Network Address Translation (NAT)
In this common method, you implement the NAT on your side of the VPN tunnel. Your firewall or router translates the client’s original private IPs into a unique address space you control.
You create specific NAT rules for each client. For instance, Client A’s 192.168.1.0/24 could be mapped to 10.10.1.0/24 on your network, while Client B’s same 192.168.1.0/24 is mapped to 10.10.2.0/24.
Pros: This approach significantly simplifies the process for your clients. It makes onboarding faster and requires less technical effort from them, which improves customer satisfaction.
You have full control over the NAT configurations. This allows for centralized management and ensures consistency across all client connections.
Cons: This method creates substantial technical and administrative overhead for your team. You need a robust system to track every client’s original IPs and their NAT-translated counterparts.
Scaling becomes a major challenge. As you add more clients and target many individual devices, your NAT tables can become very large and complex, increasing the risk of errors.
Not all firewall vendors implement NAT for VPNs in the same way. Some, like Cisco ASA (and newer FPR models), offer strong support for matching NAT rules to specific VPN tunnels. Others, like certain Palo Alto firewall versions, might require more advanced techniques or face limitations in achieving the desired segmentation with NAT and VPNs. Always test thoroughly.
Variant: Using the Carrier-Grade NAT (CGN) Range (100.64.0.0/10)
Instead of using standard private IP ranges (like 10.x.x.x) for your provider-side NAT translations, you can utilize the 100.64.0.0/10 address space. This range is specifically reserved by IETF RFC 6598 for Carrier-Grade NAT or large-scale NAT implementations by Internet Service Providers.
This is a valid and intended use of this IP space for large-scale NAT scenarios. It provides a dedicated block of private IPs to map client networks to.
Pros: The 100.64.0.0/10 range is large and specifically designed for multi-tenant NAT. It is highly unlikely to conflict with any client’s internal private IP addresses, which are usually from the 10.x.x.x, 172.16.x.x, or 192.168.x.x ranges.
Using this dedicated range helps maintain clean separation and avoids accidental overlaps within your own internal network’s translated IP space.
Cons: While using CGN range solves the overlap problem for the translation space, it still involves the same administrative and technical overhead as other provider-side NAT methods. You still need to manage and document all the NAT mappings.
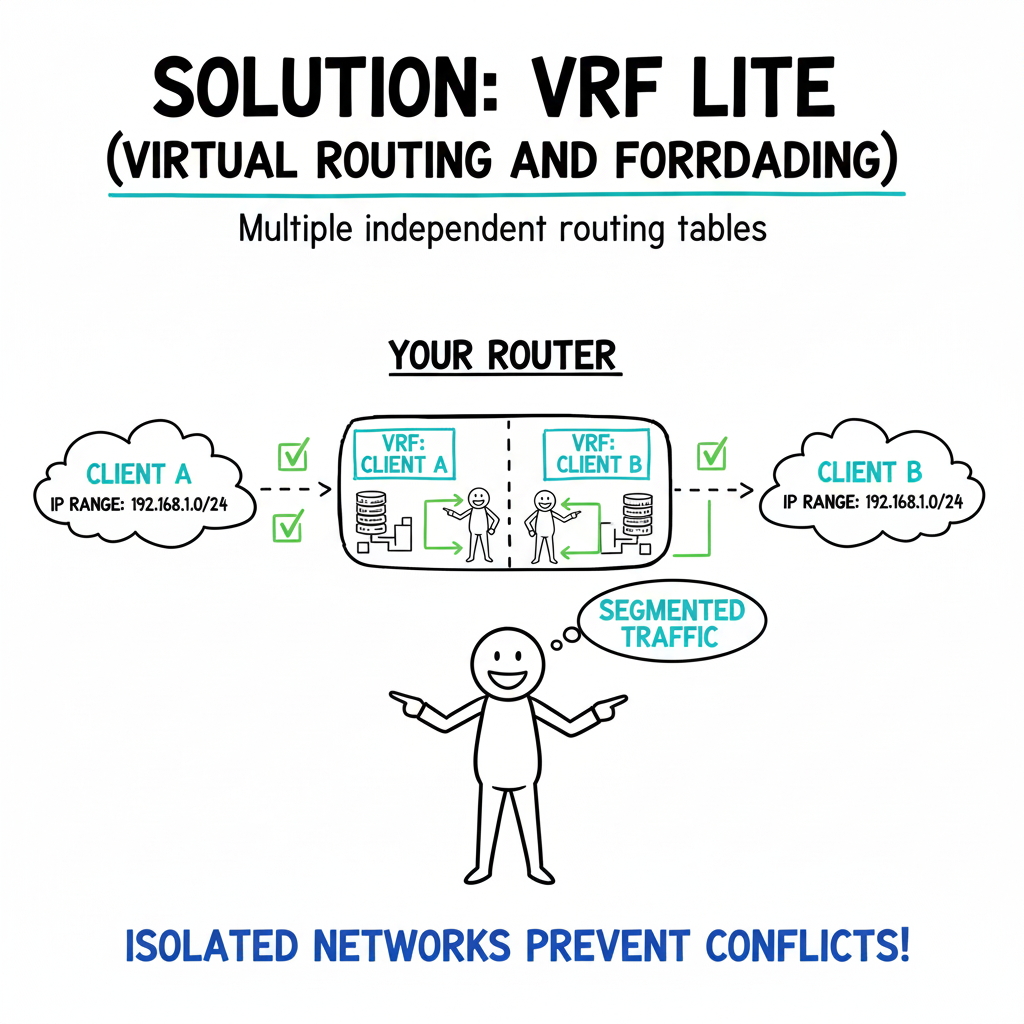
Solution 3: Virtual Routing and Forwarding (VRF)
Virtual Routing and Forwarding (VRF) is an advanced networking feature that allows a single router or firewall to host multiple independent routing tables. Each VRF acts like a completely separate router.
You can assign each client’s VPN tunnel to its own VRF. This means Client A’s VPN traffic and its routing entries are kept entirely separate from Client B’s, even if both clients use the exact same overlapping IP addresses.
Pros: VRF provides true network segmentation. It natively handles overlapping IP addresses because each client’s network effectively exists in its own isolated routing domain.
It eliminates the need for complex NAT rules for overlapping IPs, simplifying troubleshooting and potentially improving performance for routed traffic. It offers a cleaner and more scalable architecture for multi-tenant environments.
Cons: Implementing VRF requires network devices that support it, typically enterprise-grade routers or firewalls. It adds complexity to the initial network design and configuration.
Your internal applications might need to know which VRF to use when initiating connections to a client. This often involves specific routing policies or source interface bindings.
Solution 4: Advanced SD-WAN Solutions
Modern Software-Defined Wide Area Network (SD-WAN) platforms are increasingly designed with multi-tenancy and overlapping IP scenarios in mind. They can offer built-in features to address this challenge.
Some SD-WAN solutions provide centralized policy management that can automatically handle NAT or VRF-like segmentation for each client’s connection. They can create virtual segments that abstract away the underlying IP conflicts.
Pros: SD-WAN can offer highly automated and centralized management of client connections, including solutions for IP overlap. This reduces manual configuration and human error.
Many SD-WAN solutions integrate features like VPN, firewalling, and intelligent traffic routing, providing a comprehensive platform. They can simplify overall network operations and scaling.
Cons: SD-WAN solutions can be costly, involving new hardware, software licenses, and subscription fees. There might be vendor lock-in, and migrating to a new platform requires significant effort.
While they simplify management once deployed, the initial design and integration of an SD-WAN solution can be complex.
Other Important Considerations and Best Practices
Robust IP Address Management (IPAM) System: Regardless of the chosen method, an IPAM solution is critical. It helps you track all allocated IPs, NAT pools, and client networks to prevent conflicts and ensure efficient usage.
Standardize Configurations: Develop standard templates and processes for setting up new client VPNs and associated NAT or VRF configurations. This reduces errors and speeds up onboarding.
Thorough Firewall Compatibility Testing: Always test your chosen method on your specific firewall hardware and software versions. Vendor implementations of NAT and VPNs can vary significantly.
Comprehensive Monitoring and Alerting: Implement monitoring for VPN tunnel status, NAT table utilization, and VRF health. Quick alerts help you identify and resolve issues before they impact services.
Clear Client Communication: Clearly define expectations and requirements with your clients, especially if they are responsible for any part of the configuration (e.g., client-side NAT). Provide detailed guides.
Future-Proofing with IPv6: While not an immediate solution for overlapping IPv4, encourage clients to adopt IPv6 where possible. IPv6 offers a vast address space that eliminates the problem of private IP overlap entirely. This is a long-term strategy for network evolution.
Conclusion
Addressing overlapping private IP addresses in multi-client site-to-site VPNs is a core challenge for service providers. While client-side NAT can simplify your network, it often creates too much burden for clients. Provider-side NAT, potentially using the 100.64.0.0/10 range, is effective but demands careful management and documentation. For larger, more complex environments, VRF and advanced SD-WAN solutions offer cleaner, more scalable architectures. The best approach depends on your specific scale, client capabilities, existing infrastructure, and operational resources. Always prioritize strong IPAM, thorough testing, and clear communication to ensure success.
- Telecom Network Infrastructure: Complete Guide to Components & Design - January 6, 2026
- TP-Link TL-SG108E vs Netgear GS308E: Budget Smart Switches - January 5, 2026
- MikroTik CRS305-1G-4S+ Review: The Ultimate Budget SFP+ Switch Guide - December 25, 2025



Overlapping ips are a headache with vpns. for simple access without ip conflicts, sometimes a free web proxy is just easier for browsing.