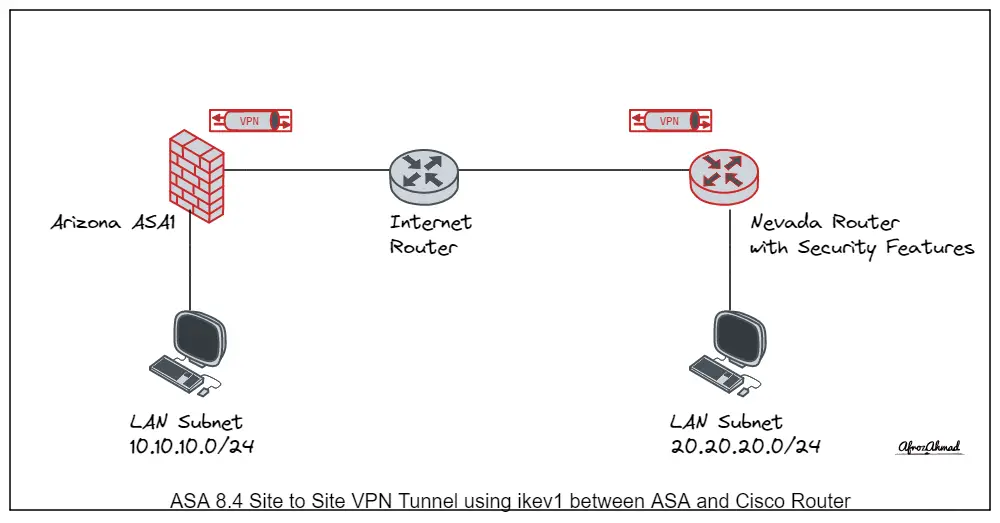
We will be working on the above-mentioned topology on GNS3. Our goal is to make a VPN S2S tunnel between Arizona ASA1 running code 8.4 and Nevada router, and finally, we will allow our LAN subnets of both locations to move across the VPN S2S tunnel. Ip addressing is mentioned in the diagram.
Verify the configuration
Before starting with the S2S configuration, let us verify the configuration of ASA:-
ASA1# sh run int g0
interface GigabitEthernet0
nameif inside
security-level 100
ip address 10.10.10.1 255.255.255.0
ASA1# sh run int g1
interface GigabitEthernet1
nameif outside
security-level 0
ip address 12.12.12.1 255.255.255.0
For the Lab purpose, I have allowed everything related to ip; we must not do this in the production network.
ASA1# sh run access-list
access-list outside_in extended permit ip any any
access-list inside_in extended permit ip any any
access-list interesting-traffic extended permit ip 10.10.10.0 255.255.255.0 20.20.20.0 255.255.255.0
ASA1# sh run access-group
access-group inside_in in interface inside
access-group inside_in out interface inside
access-group outside_in in interface outside
access-group outside_in out interface outside
Now we will start on the ASA1 configuring VPN S2S tunnel using IKEV1, I will highlight every step as we move forward.
Configuring ISAKMP Policies for IKEv1 Connections:-
Step 1 Enter IPsec IKEv1 policy configuration mode. For example:
ASA1(config)# crypto ikev1 policy 1
ASA1(config-ikev1-policy)#
Step 2 Set the authentication method. The following example configures a preshared key:
ASA1(config-ikev1-policy)# authentication pre-share
ASA1(config-ikev1-policy)#
Step 3 Set the encryption method. The following example configures 3DES:
ASA1(config-ikev1-policy)# encryption 3des
ASA1(config-ikev1-policy)#
Step 4 Set the HMAC method. The following example configures MD5:
ASA1(config-ikev1-policy)# hash md5
ASA1(config-ikev1-policy)#
Step 5 Set the Diffie-Hellman group. The following example configures Group 2:
ASA1(config-ikev1-policy)# group 2
ASA1(config-ikev1-policy)#
Step 6 Set the encryption key lifetime. The following example configures 43,200 seconds (12 hours):
ASA1(config-ikev1-policy)# lifetime 43200
ASA1(config-ikev1-policy)#
Step 7 Enable IKEv1 on the interface named outside:
ASA1(config)# crypto ikev1 enable outside
ASA1(config)#write memory
Creating an IKEv1 Transform Set:-
An IKEv1 transform set combines an encryption method and an authentication method.
During the IPsec security association negotiation with ISAKMP,
the peers agree to use a particular transform set to protect a particular data flow.
The transform set must be the same for both peers.
Step 1 In global configuration mode, enter the crypto ipsec ikev1 transform-set command.
The following example configures a transform set with the name CRYPTO_SET, esp-3des encryption, and esp-md5-hmac authentication.
The syntax is as follows:-
crypto ipsec ikev1 transform-set transform-set-name encryption-method authentication-method
ASA1(config)# crypto ipsec transform-set CRYPTO_SET esp-3des esp-md5-hmac
ASA1(config)#
Configuring an ACL to match both sides LAN traffic:-
Step 1 Enter the access-list extended command. The following example configures an
ACL named interesting-traffic that lets traffic from IP addresses in the 10.10.10.0/24 network travel to the 20.20.20.0/24 network.
The syntax is access-list listname extended permit ip source-ipaddress source-netmask destination-ipaddress destination-netmask.
ASA1(config)# access-list interesting-traffic extended permit ip 10.10.10.0 255.255.255.0 20.20.20.0 255.255.255.0
Defining a Tunnel Group:-
A tunnel group is a set of records that contain tunnel connection policies.
You configure a tunnel group to identify AAA servers, specify connection parameters, and define a default group policy. The ASA stores tunnel groups internally.
Note:-To use VPNs, including tunnel groups, the ASA must be in single-routed mode. The commands to configure tunnel-group parameters do not appear in any other mode.
Step 1 To set the connection type to IPsec LAN-to-LAN, enter the tunnel-group command.
The syntax is tunnel-group name type [type-name], where name is the name you assign to the tunnel group, and type is the type of tunnel.
The tunnel types as you enter them in the CLI are:
• remote-access (IPsec, SSL, and clientless SSL remote access)
• ipsec-l2l (IPsec LAN to LAN)
In the following example, the name of the tunnel group is the IP address of the LAN-to-LAN peer, 34.34.34.1
ASA1(config)# tunnel-group 34.34.34.1 type ipsec-l2l
ASA1(config)#
Step 2 To set the authentication method to the preshared key, enter the ipsec-attributes mode and then enter the pre-shared-key command to create the preshared key. You must use the same preshared key on both ASAs for this LAN-to-LAN connection.
The key is an alphanumeric string of 1-128 characters.
In the following example, the IKEv1 preshared key is cisco:
ASA1(config)# tunnel-group 34.34.34.1 ipsec-attributes
ASA1(config-tunnel-ipsec)# pre-shared-key cisco
Creating a Crypto Map and Applying It To an Interface:-
Step 1 To assign an access list to a crypto map entry, enter the crypto map match address command.
The syntax is crypto map map-name seq-num match address aclname. In the following example, the map name is IPSEC, the sequence number is 1,
and the access list name is interesting-traffic.
ASA1(config)# crypto map IPSEC 1 match address interesting-traffic
ASA1(config)#
Step 2 To identify the peer (s) for the IPsec connection, enter the crypto map set peer command.
The syntax is crypto map map-name seq-num set peer {ip_address1 | ASA11}[… ip_address10 | ASA110]. In the following example the peer name is 34.34.34.1
ASA1(config)# crypto map IPSEC 1 set peer 34.34.34.1
ASA1(config)#
Step 3 To specify an IKEv1 transform set for a crypto map entry, enter the crypto map ikev1 set transform-set command.
The syntax is crypto map map-name seq-num ikev1 set transform-set transform-set-name.
In the following example, the transform set name is CRYPTO_SET
ASA1(config)# crypto map IPSEC 1 set ikev1 transform-set CRYPTO_SET
ASA1(config)#crypto map IPSEC interface outside
Nevada Router configuration:-
The remote router configuration is straightforward. However, we must need to match encryption, group, and hash parameters on both sides to make the tunnel work.
Nevada#sh run | s crypto
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
lifetime 43200
crypto isakmp key cisco address 12.12.12.1
crypto ipsec transform-set CRYPTO esp-3des esp-md5-hmac
crypto map IPSEC 1 ipsec-isakmp
set peer 12.12.12.1
set transform-set CRYPTO
match address 101
crypto map IPSEC
Nevada#sh run | i access-list
access-list 101 permit ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255
Then we must apply the crypto map to the outside interface facing the internet on the Nevada router.
Nevada#sh run int fa0/1
ip address 34.34.34.1 255.255.255.0
duplex auto
speed auto
crypto map IPSEC
end
After configuring everything on both remote sides, we must initiate traffic from Arizona LAN to Nevada LAN and see whether we are succeeding or not. Let us do that right now.
NevadaLAN#ping 10.10.10.2 re 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 10.10.10.2, timeout is 2 seconds:
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 32/69/104 ms
ArizonaLAN#ping 20.20.20.2 re 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 20.20.20.2, timeout is 2 seconds:
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 40/65/108 ms
Now we verify our tunnel configuration with a few show commands.
ASA1# sh crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 34.34.34.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
ASA1#
Nevada#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
12.12.12.1 34.34.34.1 QM_IDLE 1003 0 ACTIVE
IPv6 Crypto ISAKMP SA
Nevada#
Indeed our tunnel is up and working as we are able to ping both LANs over the internet cloud.
Let’s now verify the Encapsulation and Decapsulation on the tunnel on ASA1.
ASA1# sh crypto ipsec sa
interface: outside
Crypto map tag: IPSEC, seq num: 1, local addr: 12.12.12.1
access-list interesting-traffic extended permit ip 10.10.10.0 255.255.255.0 20.20.20.0 255.255.255.0
local ident (addr/mask/prot/port): (10.10.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (20.20.20.0/255.255.255.0/0/0)
current_peer: 34.34.34.1
#pkts encaps: 29, #pkts encrypt: 29, #pkts digest: 29
#pkts decaps: 29, #pkts decrypt: 29, #pkts verify: 29
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 29, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 12.12.12.1/0, remote crypto endpt.: 34.34.34.1/0
path mtu 1500, ipsec overhead 58, media mtu 1500
current outbound spi: 05297D11
current inbound spi : 3081A935
inbound esp sas:
spi: 0x3081A935 (813803829)
transform: esp-3des esp-md5-hmac no compression
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 12288, crypto-map: IPSEC
sa timing: remaining key lifetime (kB/sec): (4373997/3442)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x3FFFFFFF
outbound esp sas:
spi: 0x05297D11 (86605073)
transform: esp-3des esp-md5-hmac no compression
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 12288, crypto-map: IPSEC
sa timing: remaining key lifetime (kB/sec): (4373997/3442)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Note:- To troubleshoot the routing issue, if we do not see encapsulation at our end, then the routing issue should be at our end, and if we do not see decapsulation, then the routing issue should be at the remote end. Also, we have various debug tools to help with the VPN S2S tunnel issue.
ASA1# debug crypto condition peer 34.34.34.1
ASA1# debug crypto ipsec
ASA1# debug crypto ikev1
To clear the tunnel, we can use.
ASA1# clear crypto isakmp sa
ASA1# Jan 24 12:11:32 [IKEv1]Group = 34.34.34.1, IP = 34.34.34.1, Session is being torn down. Reason: Administrator Reset
ASA1#
Conclusion
I hope you liked the article; please let me know if you want anything to add.
- Epson EpiqVision Flex CO-W01 Projector Review - February 21, 2025
- How to Log in to Your Netgear Router - January 17, 2025
- Gaimoo GM200 Mini Projector Review - January 12, 2025




I’m not sure where you’re getting your info, but good topic. I needs to spend some time learning more or understanding more. Thanks for wonderful info I was looking for this information for my mission.
This design is incredible! You obviously know how to keep
a reader amused. Between your wit and your videos, I was almost moved to start my own
blog (well, almost…HaHa!) Fantastic job. I really enjoyed what you had to say,
and more than that, how you presented it.
Too cool!
It’s hard to find educated people in this particular subject, but you sound like you know what you’re talking about! Thanks
I like what you guys tend to be up too. This type of clever work and coverage! Keep up the great works guys I’ve included you guys to my personal blogroll.
We’re a group of volunteers and opening a new scheme in our community. Your site provided us with valuable info to work on. You’ve done a formidable job and our whole community will be thankful to you.
Hi, Neat post. There is an issue along with your web site in internet explorer, could check this? IE still is the marketplace chief and a good component of other people will leave out your fantastic writing due to this problem.