Wi-Fi Security Protocols: WEP vs WPA vs WPA2 vs WPA3
Outdated Wi-Fi security? Learn why WPA2 or WPA3 are essential upgrades for protecting your network.


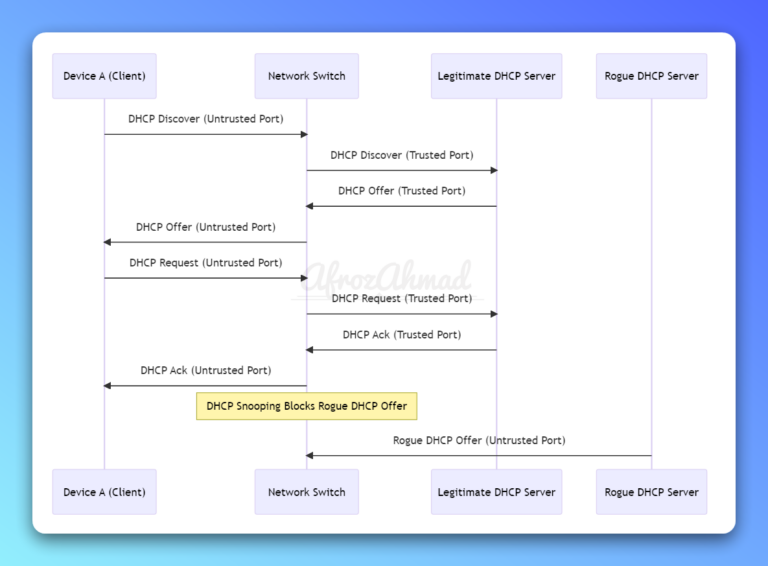
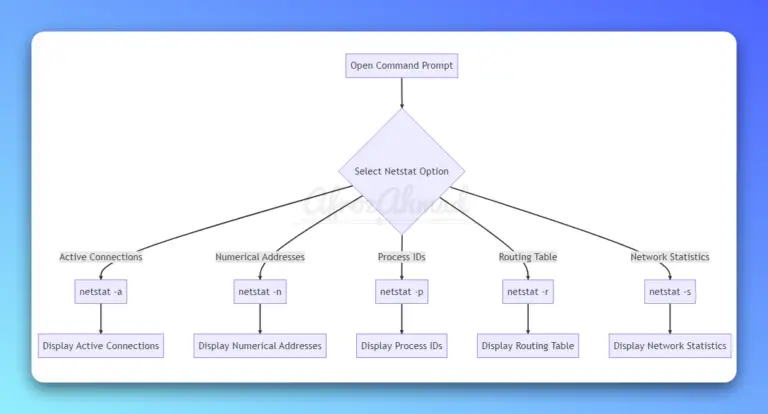
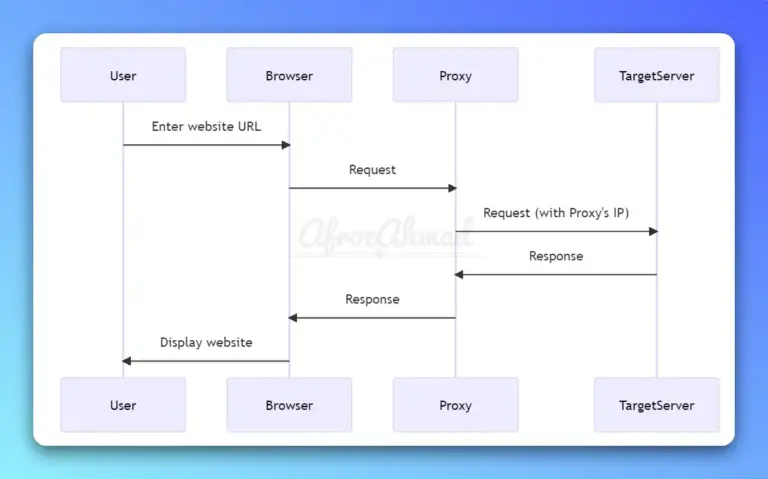
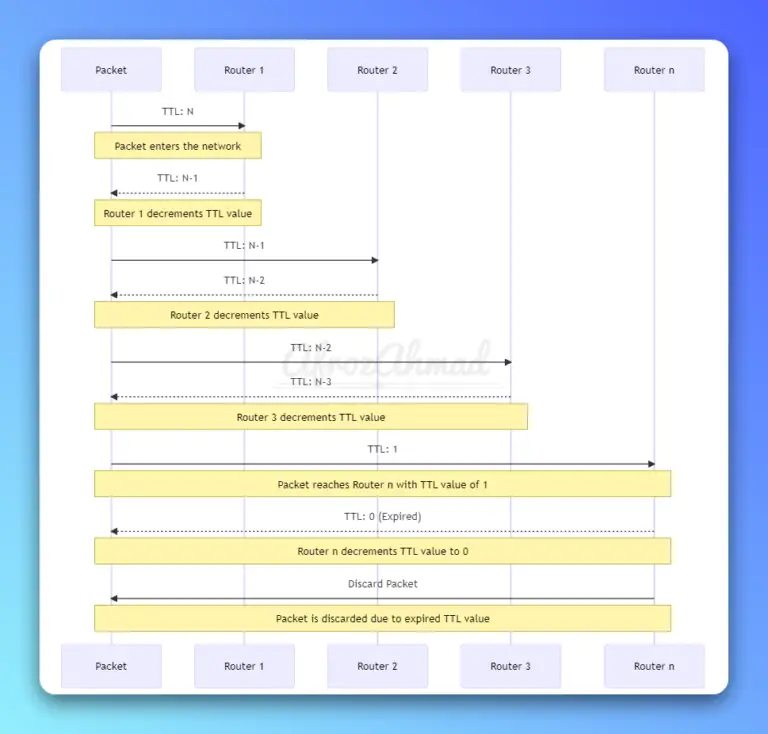
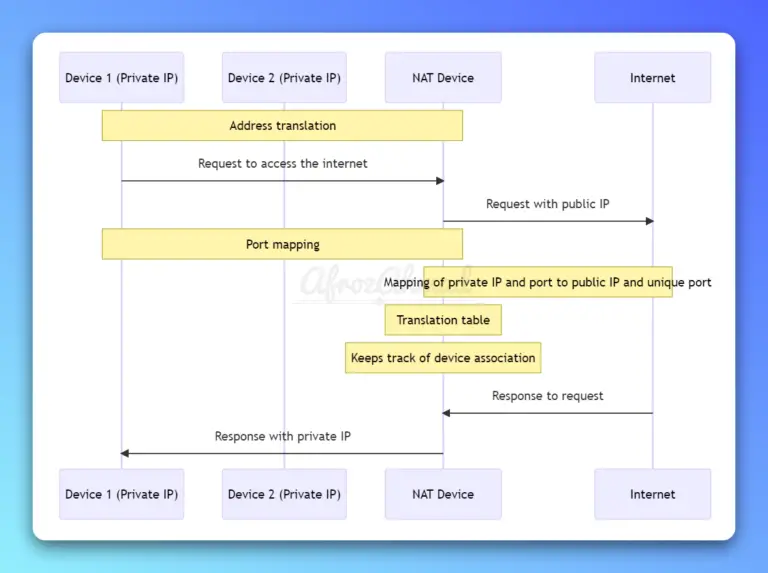
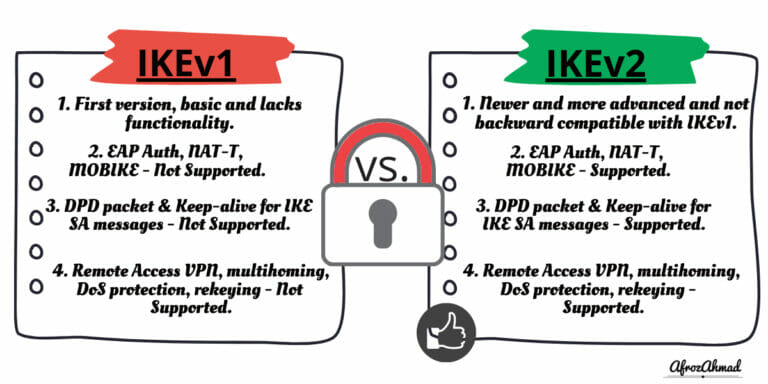
In this tutorial i will show you how to install Backtrack 5 R3 in Vmware workstation 8, it is recently released by offensive security team and it is used by penetration testers world wide. Installation is easy just follow given simple steps. Requirements 1…