Showdown: IKEv1 vs IKEv2
Internet Key Exchange (IKE) is a protocol used to set up a secured communication channel between two networks. To establish a secured channel, the two communicating parties need to create a Security Association (SA) between each other through the use of Internet Protocol Security (IPsec). This blog post will compare head to head between IKEv1 vs IKEv2 and provide some key insights. IKEv1 was one of the first standards for internet key exchange, a standard that had remained mostly unchanged for almost 12 years, the year 1995 when IETF first introduced IKE or IKEv1 through RFC 2407, RFC 2408, and RFC 2409. And then, in 2010, by RFC 5996, IKEv2 was first published. IKEv2, the newest version of this protocol, offered several improvements that make it much more secure and easier to implement than previous versions.
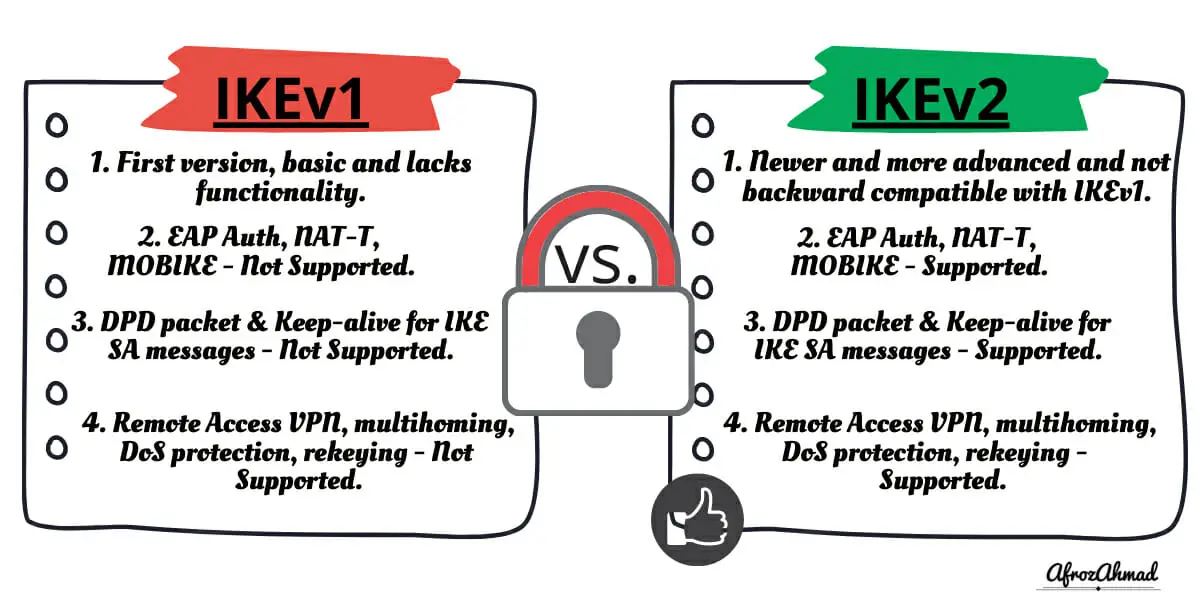
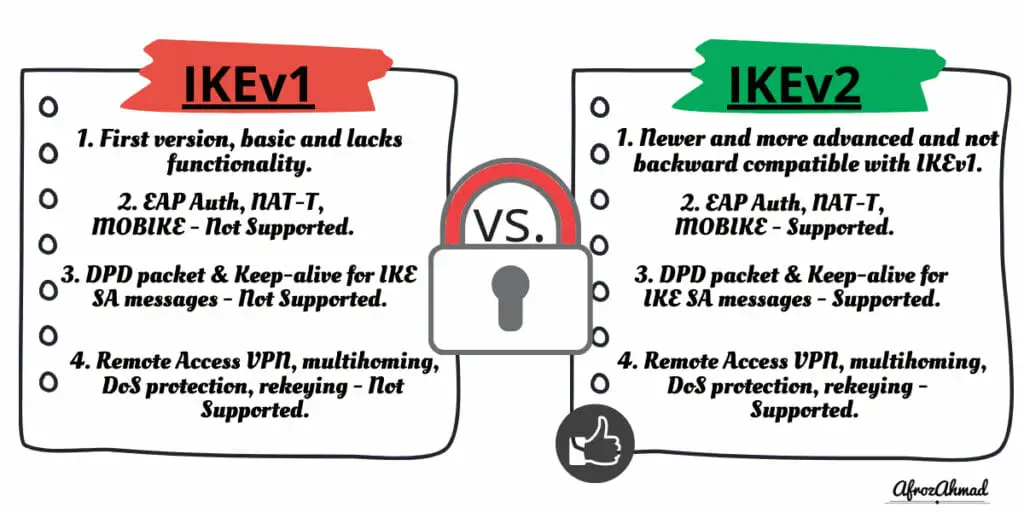
Key differences between IKEv1 vs IKEv2
| Key Area | IKEv1 or Internet Key Exchange Version 1 | IKEv2 or Internet Key Exchange Version 2 |
|---|---|---|
| History | IKEv1 is predecessor of IKEv2 and is the first child of IKE (Internet Key Exchange) family. | IKEv2 is newer version of IKE and is more advanced. |
| Bandwidth Consumption | Consumes MORE bandwidth than IKEv2. | Consumes LESS bandwidth than IKEv1. IKEv2 consumes less bandwidth by reducing the number of Security Associations required per VPN tunnel. |
| EAP Authentication | NOT supported | IKEv2 supports EAP authentication. |
| MOBIKE (Mobility and Multi-homing Protocol) support | NOT supported. | IKEv2 supports MOBIKE. MOBIKE enables the usage of IKEv2 on mobile platforms such as smartphones and by users with multi-homed deployments. |
| NAT traversal (NAT-T) - It is required when a router or a firewall along the way does NAT (Network Address Translation). | NOT supported as a built-in feature and Defined as an extension if needed. | Native support. |
| Detect if a VPN tunnel is still alive. | Not supported. | Supported. |
| Messages to establish a VPN tunnel. | IKEv1 uses 9 (Main Mode) or 6 messages (in Aggressive mode). | IKEv2 uses FEWER and four messages. IKEv2 creates an IKE SA and two IPSec SAs in two exchanges (four messages). |
| Dead Peer Detection or DPD packet & Keep-alive for IKE SA messages | Not supported by default and can be defined as an extension if required. | Enabled by default. |
| Reliability | Less reliable. | - IKEv2 is more reliable since all message types are Request/Response. - IKE SA (Security Associations) can be deleted by defined procedures. - A message can be retransmitted by a defined procedure. - MOBIKE enables a user to roam seamlessly and change network connections from wired to wireless without disconnecting VPN sessions. |
| Asymmetric authentication (can use a different authentication method) | NOT supported. | Supported. |
| Backward Compatibility | Not required as IKEv1 is the first protocol in the IKE family. | IKEv2 is not backward compatible with IKEv1. |
| Authentication methods | Four Methods. - Pre-Shared Key (PSK) - Digital Signature (RSA-Sig) - Public Key Encryption - Revised Mode of Public-key Encryption | 2 methods. - Pre-Shared Key (PSK) - Digital Signature (RSA-Sig) |
| Remote Access VPN | NOT supported by default. If required then can be Supported by vendor-specific implementations: - Mode config - XAUTH | Supported by default: - Extensible Authentication Protocol (EAP) - User authentication over EAP is associated with IKE's authentication. - Configuration payload (CP) |
| Multi-homing | Not supported. | Supported by MOBIKE (Mobility and Multi-homing Protocol). |
| Mobile Clients | Not supported. | Supported by MOBIKE (Mobility and Multi-homing Protocol). |
| DoS protections | Not supported. | Some level of DoS protection is supported, for example - Anti-replay function. - 'Cookies' for mitigating flooding attacks. - Lots of vulnerabilities in IKEv1 were fixed by IKEv2. |
| Rekeying | Not supported. | Supported. |
| Multi-hosting | Not supported. | Supported. The use of multiple IDs on a single IP address and port pair makes it possible to support multi-hosting in IKEv2. |
| Lifetime for IKE SAs | In IKEv1, mutual agreement between peers is necessary. | NOTHING has been negotiated. Each peer has the ability to delete SAs at any time via the exchange of DELETE payloads. |
IKEv1 vs IKEv2
Conclusion
In conclusion, both IKEv1 vs IKEv2 offer VPN capability and security features. However, IKEv1 is an old version of IPSec that is insecure, outdated, and vulnerable to man-in-the-middle attacks. The new version of IPsec, IKEv2, is much more secure and provides better security for companies and organizations.
If you liked this post, please share it to reach out to other people who might be searching for the same topic.
- Epson EpiqVision Flex CO-W01 Projector Review - February 21, 2025
- How to Log in to Your Netgear Router - January 17, 2025
- Gaimoo GM200 Mini Projector Review - January 12, 2025