With this IP subnetting and CIDR cheat sheet article, we’ll provide you with all the details and show you how to subnet IP addresses, which are essential for network-related interviews, jobs, and exams.
Understanding how subnetting works may seem difficult initially, but it begins to make sense as you continue. You can quickly create and deploy IP subnets that will give your organization the necessary level of design ease, scalability, management, and security you need.
IP Subnetting Cheat Sheet Infographic PDF
I hope you have downloaded the subnet cheat sheet PDF; let’s first understand a few basic things before diving into subnetting.
What is IP subnetting, and why do we need it?
IP Subnetting splits a network into multiple sub-networks, creating a partition based upon a consecutive block of IPv4 addresses, further represented by an IP address and the subnet mask.
Subnetting is widely used to preserve IP addresses and design scalable and secured networks.
More on this later; let’s first understand IP address and other important concepts related to subnetting.
What is an IP address?
An IP address is a unique identifier for every computer, server, router, and hardware that connects to the network. But, first, let’s understand a few needy greedy things about IP addresses.
- It is a 32-bit binary number representing a specific physical location on the network.
- Three dots separate this 32-bit number, and four blocks we call octets. Each octet represents 8 bits or 1 byte, and when you multiply by 4, it will give 8×4=32 bits.
- IP addresses can be broken down into three categories, namely unicast (used on individual devices), multicast (allows someone to send information to a group of computers), and broadcast (which allows one computer to send information out to everyone). Unicast IP addresses are the most common type and are found on our laptops or other devices to connect to the Internet.
What is a subnet mask?
The subnet mask divides the IP address into the host and network addresses, defining which parts belong to the device and which to the network.
An IP address and a subnet mask provide complete information and numerical identification to any device connecting to the network. Therefore, both types of addresses are always used in conjunction and have a length of 32 bits. These 32 bits are further split into four sections. Each portion is referred to as an Octet and includes 8 bits.
For example:- 192.168.100.1 255.255.255.0
Here, 192.168.100.1 is the IP Address, and 255.255.255.0 is the Subnet Mask.
When you put the IP address and the subnet mask together, you can separate the network and host parts of the address. Here subnet mask is 255.255.255.0, so 192.168.100.0 will become Network Address, and the Host Address will become 0.0.0.1
What is Classless and Classful Ip addressing, and what is the difference?
IPv4 addresses were initially intended to be classful— ranging from Class A to Class E. Also, Unicast IPv4 addresses can be divided into two parts: the network portion and the Host ID portion of the address. Please check the table below.
Classful IP addressing worked within the bounds of the above-defined classes and was an old way of assigning IP addresses and subnets to a network.
As the Internet grew, this restricted assignment of IP addresses became a bottleneck. As a result, a more flexible and practical approach, called Classless IP Addressing, was developed.
What is the difference between Private and Public IP addresses?
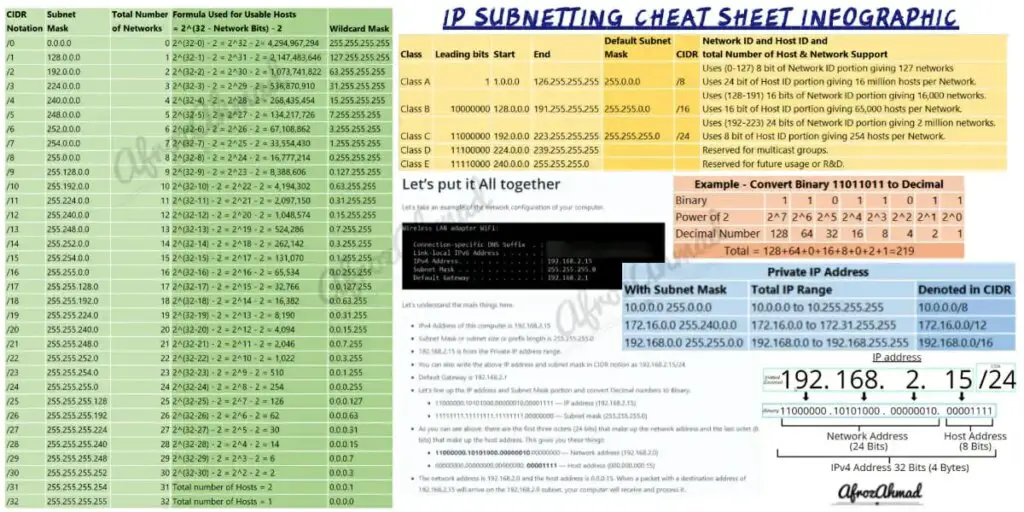
- Private ip addresses, sometimes called Internal ip addresses, are only meant to be used on private networks and should not be routed on the Internet.
- And then there are Public ip addresses that can only be used on the Internet. You can check your public address by simply googling “what is my address.”
- IANA has designated the following three blocks of IP address space for private use.
- You can refer to the below table for reserved private IP addresses.
| Private IP Address with Subnet Mask | Private IP Range | Private IP Range denoted in CIDR |
|---|---|---|
| 10.0.0.0 255.0.0.0 | 10.0.0.0 to 10.255.255.255 | 10.0.0.0/8 |
| 172.16.0.0 255.240.0.0 | 172.16.0.0 to 172.31.255.255 | 172.16.0.0/12 |
| 192.168.0.0 255.255.0.0 | 192.168.0.0 to 192.168.255.255 | 192.168.0.0/16 |
What is CIDR notation, and why do we use it?
IETF created Classless Interdomain Routing or CIDR in 1993 to provide greater granularity than classful routing; the CIDR notation is /XX.
It is also an efficient method for allocating IP subnets without any subnet boundaries, which lowered the rate at which IPv4 addresses were depleted and helped grow the Internet rapidly.
For example: Instead of writing the IP address with a subnet mask, 192.168.100.0 255.255.255.0, we can write 192.168.100.0/24.
What are CIDR Blocks?
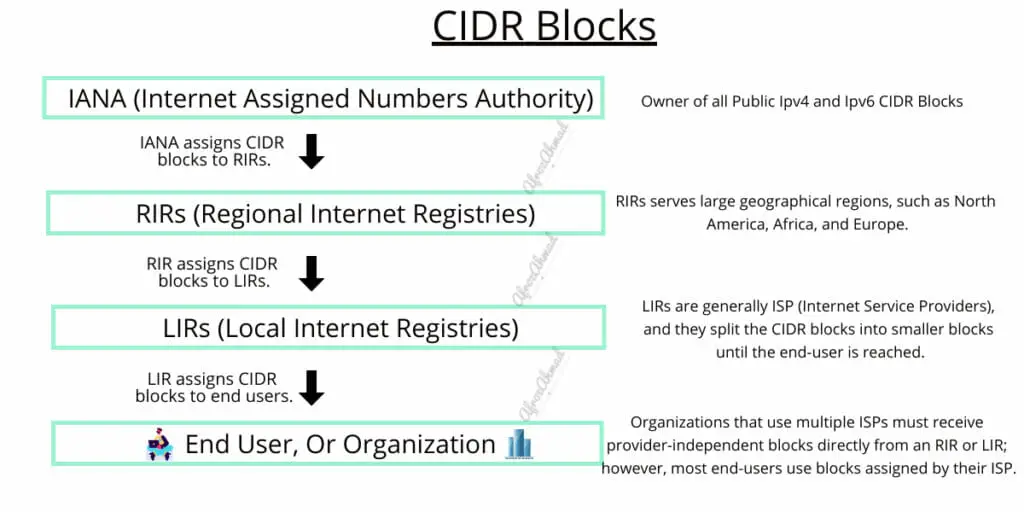
CIDR blocks are made up of addresses with the same prefix and the same amount of bits. And with the help of supernetting, you can combine numerous connecting CIDR blocks into a bigger routing network with a shared network prefix.
The length of the prefix determines the size of the CIDR blocks. Using a shorter prefix, for example, 10.0.0.0/8, more addresses (approx. 16 Million) can be allocated, resulting in a bigger block. On the other hand, a longer prefix, for example, 192.168.100.200/29, represents a smaller block, and you can allocate fewer addresses (6) only.
The Internet Assigned Numbers Authority (IANA) is the first to deal with CIDR blocks. After that, Regional Internet Registries (RIRs) receive huge allocations of IP addresses from IANA. Large geographical regions, such as North America, Africa, and Europe, are served by these large CIDR blocks.
Once an RIR obtains a CIDR block from IANA, it further divides it into smaller pieces to distribute to Local Internet Registries (LIRs). LIRs are generally ISP (Internet Service Providers) and split the CIDR blocks into smaller ones until the end-user is reached. The quantity of unique addresses needed by an end-user determines the size of the block granted to them by LIR.
Organizations that use multiple ISPs must receive provider-independent blocks directly from an RIR or LIR; however, most end-users use blocks assigned by their Internet Service Provider.
What is VLSM, and why do we use it?
When using VLSM, you can divide an IP address space into subnets of different sizes, from 0 to 32 bits. This makes subnets more useful because subnets can have masks of various sizes. CIDR uses VLSMs to create routes.
Quick Tip:- Before choosing a routing protocol, you should always check if the protocol supports VLSM or not. For example, classful routing protocols like RIPv1 and IGRP do not support VLSM.
How to convert Binary to Decimal and Decimal to Binary?
IPv4 addresses are always represented in dotted decimals separated by three dots for humans to understand easily. Further, machines convert these decimal numbers into Binary numbers for further processing. So we must know how to convert Binary to Decimal and vice versa. The binary is always represented in 1 or 0. However, any integer or non-integer number is Decimal, for example, 1,2,100,200, etc.
Example:- Convert Binary 11011011 into Decimal.
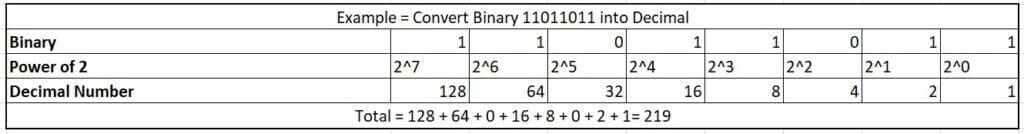
Please refer to the handy table for Binary to Decimal and Decimal to Binary conversion.
Binary1 means the bit is ON | Decimal |
|---|---|
| 0 | 0 |
| 1 | 1 |
| 10 | 2 |
| 11 | 3 |
| 100 | 4 |
| 101 | 5 |
| 110 | 6 |
| 111 | 7 |
| 1000 | 8 |
| 1001 | 9 |
| 1010 | 10 |
| 1011 | 11 |
| 1100 | 12 |
| 1101 | 13 |
| 1110 | 14 |
| 1111 | 15 |
| 10000 | 16 |
| 10001 | 17 |
| 10010 | 18 |
| 10011 | 19 |
| 10100 | 20 |
| 10101 | 21 |
| 10110 | 22 |
| 10111 | 23 |
| 11000 | 24 |
| 11001 | 25 |
| 11010 | 26 |
| 11011 | 27 |
| 11100 | 28 |
| 11101 | 29 |
| 11110 | 30 |
| 11111 | 31 |
| 100000 | 32 |
| 1000000 | 64 |
| 10000000 | 128 |
| 100000000 | 256 |
IP Subnetting Cheat Sheet with CIDR Cheat Sheet
So now we know the basics of IP addressing and subnetting; let’s put it all together in an IP subnetting cheat sheet for quick reference.
The formula for usable IP addresses always deducts two IP addresses because two IPs are always reserved within any subnet. One IP is Network Address, and the second one is Broadcast Address.
| CIDR Notation | Subnet Mask | Total Number of Networks | Formula Used for Usable Hosts= 2^(32 - Network Bits) - 2 | Wildcard Mask |
|---|---|---|---|---|
| /0 | 0.0.0.0 | 0 | 2^(32-0) - 2 = 2^32 - 2= 4,294,967,294 | 255.255.255.255 |
| /1 | 128.0.0.0 | 1 | 2^(32-1) - 2 = 2^31 - 2 = 2,147,483,646 | 127.255.255.255 |
| /2 | 192.0.0.0 | 2 | 2^(32-2) - 2 = 2^30 - 2 = 1,073,741,822 | 63.255.255.255 |
| /3 | 224.0.0.0 | 3 | 2^(32-3) - 2 = 2^29 - 2 = 536,870,910 | 31.255.255.255 |
| /4 | 240.0.0.0 | 4 | 2^(32-4) - 2 = 2^28 - 2 = 268,435,454 | 15.255.255.255 |
| /5 | 248.0.0.0 | 5 | 2^(32-5) - 2 = 2^27 - 2 = 134,217,726 | 7.255.255.255 |
| /6 | 252.0.0.0 | 6 | 2^(32-6) - 2 = 2^26 - 2 = 67,108,862 | 3.255.255.255 |
| /7 | 254.0.0.0 | 7 | 2^(32-7) - 2 = 2^25 - 2 = 33,554,430 | 1.255.255.255 |
| /8 | 255.0.0.0 | 8 | 2^(32-8) - 2 = 2^24 - 2 = 16,777,214 | 0.255.255.255 |
| /9 | 255.128.0.0 | 9 | 2^(32-9) - 2 = 2^23 - 2 = 8,388,606 | 0.127.255.255 |
| /10 | 255.192.0.0 | 10 | 2^(32-10) - 2 = 2^22 - 2 = 4,194,302 | 0.63.255.255 |
| /11 | 255.224.0.0 | 11 | 2^(32-11) - 2 = 2^21 - 2 = 2,097,150 | 0.31.255.255 |
| /12 | 255.240.0.0 | 12 | 2^(32-12) - 2 = 2^20 - 2 = 1,048,574 | 0.15.255.255 |
| /13 | 255.248.0.0 | 13 | 2^(32-13) - 2 = 2^19 - 2 = 524,286 | 0.7.255.255 |
| /14 | 255.252.0.0 | 14 | 2^(32-14) - 2 = 2^18 - 2 = 262,142 | 0.3.255.255 |
| /15 | 255.254.0.0 | 15 | 2^(32-15) - 2 = 2^17 - 2 = 131,070 | 0.1.255.255 |
| /16 | 255.255.0.0 | 16 | 2^(32-16) - 2 = 2^16 - 2 = 65,534 | 0.0.255.255 |
| /17 | 255.255.128.0 | 17 | 2^(32-17) - 2 = 2^15 - 2 = 32,766 | 0.0.127.255 |
| /18 | 255.255.192.0 | 18 | 2^(32-18) - 2 = 2^14 - 2 = 16,382 | 0.0.63.255 |
| /19 | 255.255.224.0 | 19 | 2^(32-19) - 2 = 2^13 - 2 = 8,190 | 0.0.31.255 |
| /20 | 255.255.240.0 | 20 | 2^(32-20) - 2 = 2^12 - 2 = 4,094 | 0.0.15.255 |
| /21 | 255.255.248.0 | 21 | 2^(32-21) - 2 = 2^11 - 2 = 2,046 | 0.0.7.255 |
| /22 | 255.255.252.0 | 22 | 2^(32-22) - 2 = 2^10 - 2 = 1,022 | 0.0.3.255 |
| /23 | 255.255.254.0 | 23 | 2^(32-23) - 2 = 2^9 - 2 = 510 | 0.0.1.255 |
| /24 | 255.255.255.0 | 24 | 2^(32-24) - 2 = 2^8 - 2 = 254 | 0.0.0.255 |
| /25 | 255.255.255.128 | 25 | 2^(32-25) - 2 = 2^7 - 2 = 126 | 0.0.0.127 |
| /26 | 255.255.255.192 | 26 | 2^(32-26) - 2 = 2^6 - 2 = 62 | 0.0.0.63 |
| /27 | 255.255.255.224 | 27 | 2^(32-27) - 2 = 2^5 - 2 = 30 | 0.0.0.31 |
| /28 | 255.255.255.240 | 28 | 2^(32-28) - 2 = 2^4 - 2 = 14 | 0.0.0.15 |
| /29 | 255.255.255.248 | 29 | 2^(32-29) - 2 = 2^3 - 2 = 6 | 0.0.0.7 |
| /30 | 255.255.255.252 | 30 | 2^(32-30) - 2 = 2^2 - 2 = 2 | 0.0.0.3 |
| /31 | 255.255.255.254 | 31 | Total number of Hosts = 2 | 0.0.0.1 |
| /32 | 255.255.255.255 | 32 | Total number of Hosts = 1 | 0.0.0.0 |
Let’s put it All together
Let’s take an example of the network configuration of your computer.
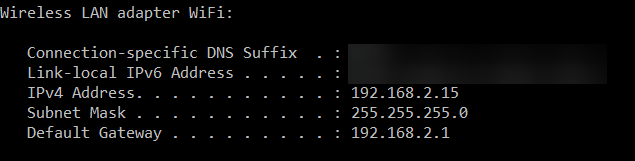
Let’s understand the main things here.
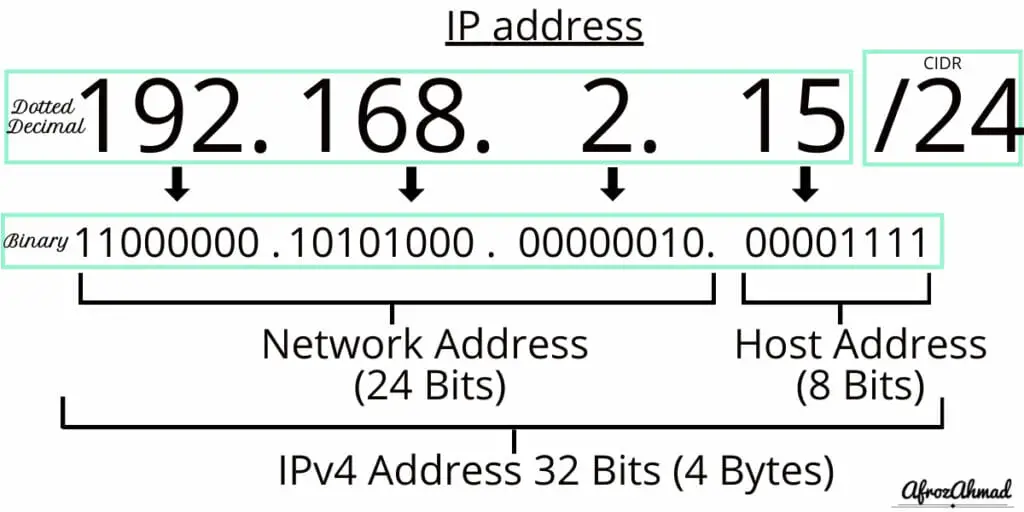
- The IPv4 address of this computer is 192.168.2.15
- The Subnet Mask or subnet size or prefix length is 255.255.255.0
- 192.168.2.15 is from the Private IP address range.
- You can also write the above IP address and subnet mask in the CIDR notation as 192.168.2.15/24
- The default Gateway (which is usually your home wifi router) is 192.168.2.1
- Let’s line up the IP address and Subnet Mask portion and convert Decimal numbers to Binary.
- 11000000.10101000.00000010.00001111 = IP address (192.168.2.15)
- 11111111.11111111.11111111.00000000 = Subnet mask (255.255.255.0)
- As you can see above, the first three octets (24 bits) make up the network address, and the last octet (8 bits) makes up the host address. This gives you these things:
- 11000000.10101000.00000010.00000000 = Network address (192.168.2.0)
- 00000000.00000000.00000000.00001111 = Host address (000.000.000.15)
- The network address is 192.168.2.0, and the host address is 0.0.0.15.
- When a packet with a destination address of 192.168.2.15 arrives on the 192.168.2.0 subnet, your computer will receive and process it.
Conclusion
In conclusion, IP Subnetting Cheat Sheet is a reference guide to subnetting. It includes an introduction to IP addressing, subnetting, IP subnets, classful/classless addressing, CIDR, and Binary to Decimal conversion table.
I hope you have found this article useful! Please share it with others who you think might benefit from it. Let me know your thoughts in the comments below.
- NETGEAR Nighthawk (RAX54S) WiFi 6 Router Review - August 24, 2024
- TP-Link AX1800 Archer AX21 WiFi 6 Router Review - August 24, 2024
- How to Connect Nanit to Hotel WiFi? - August 12, 2024