- What is DHCP Snooping?
- Why is DHCP Snooping Necessary?
- What are Rogue DHCP Servers?
- How DHCP Snooping Works and How it helps in Mitigating Rogue DHCP Servers
- DHCP Snooping Cisco Configuration
- DHCP Snooping Binding Database: Enhancing Network Security with Dynamic ARP Inspection
- Traffic Dropped by DHCP Snooping and Violation Syslog Messages
- Potential Limitations and Challenges
- Best Practices for DHCP Snooping
- Combining DHCP snooping with other security technologies – DAI, IP Source Guard, Port Security
- Conclusion
- FAQs
Dynamic Host Configuration Protocol (DHCP) is an essential protocol for managing IP address assignments in computer networks. However, with the increasing dependence on networks for communication and data transfer, it’s vital to ensure that the networks are secure and resistant to attacks. One such technique for enhancing network security is DHCP Snooping. In this article, we will delve into DHCP Snooping, discussing its necessity, benefits, and how it works to mitigate risks posed by rogue DHCP servers.
We will also cover DHCP snooping Cisco configuration, the DHCP Snooping Binding Database, and how it can be combined with other security technologies for a more robust network security posture. Furthermore, we will address potential limitations, challenges, and best practices associated with DHCP Snooping implementation. Let’s dive in.
What is DHCP Snooping?
DHCP Snooping is an advanced security feature implemented on Layer 2 or 3 network switches. It aims to protect your network from unauthorized or rogue DHCP servers.
Why is DHCP Snooping Necessary?
Dynamic Host Configuration Protocol (DHCP) servers are important for network infrastructure, as they assign IP addresses to devices like computers, laptops, printers, etc. However, unauthorized rogue DHCP servers can pose a significant risk to the security and stability of your network.
DHCP Snooping is necessary to protect your network from these rogue servers and man-in-the-middle attacks. It operates on Layer 2, filtering traffic coming from DHCP clients and ensuring that only authorized DHCP servers can access your network.
Benefits of Implementing DHCP Snooping
Implementing DHCP snooping offers several advantages:
- Mitigating rogue DHCP servers
- Preventing IP address spoofing and man in the middle attack
- Enhancing overall network security
What are Rogue DHCP Servers?
A rogue DHCP server is an unauthorized DHCP server connected to a network, which offers IP address configurations and other network parameters to devices in the network.
These rogue servers are often set up by attackers to perform man-in-the-middle attacks, redirecting network traffic to malicious websites or eavesdropping on network communications. They can cause significant security risks and network disruptions as they provide incorrect or malicious network configurations to unsuspecting clients.
How DHCP Snooping Works and How it helps in Mitigating Rogue DHCP Servers
DHCP snooping is a security feature implemented on Layer 2/3 switches that helps detect and mitigate rogue DHCP servers in a network. It works by monitoring and filtering DHCP messages, ensuring that only authorized DHCP servers can provide network configurations to clients. DHCP snooping achieves this by categorizing switch ports as either trusted or untrusted.
- Trusted ports: These ports are manually configured and connected to authorized DHCP servers or other trusted devices, like routers and switches. Trusted ports allow both client-to-server and server-to-client DHCP messages, such as DHCPDISCOVER, DHCPOFFER, DHCPREQUEST, and DHCPACK.
- Untrusted ports: These ports are automatically considered untrusted unless explicitly configured otherwise. They typically connect to end-user devices like computers, laptops, and mobile devices. Untrusted ports allow only client-to-server DHCP messages, such as DHCPDISCOVER and DHCPREQUEST, and block server-to-client messages, like DHCPOFFER and DHCPACK.
When DHCP snooping is enabled, the switch inspects DHCP messages received on untrusted ports. If a rogue DHCP server sends DHCPOFFER or DHCPACK messages through an untrusted port, the switch will drop these messages, preventing clients from receiving malicious configurations. In addition, the switch maintains a DHCP snooping binding database, which records the mapping of IP addresses, MAC addresses, VLAN numbers, and port numbers for each client connected to untrusted ports.
By monitoring and filtering DHCP traffic, DHCP snooping effectively prevents rogue DHCP servers from impacting the network and ensures that clients receive valid network configurations from authorized DHCP servers.
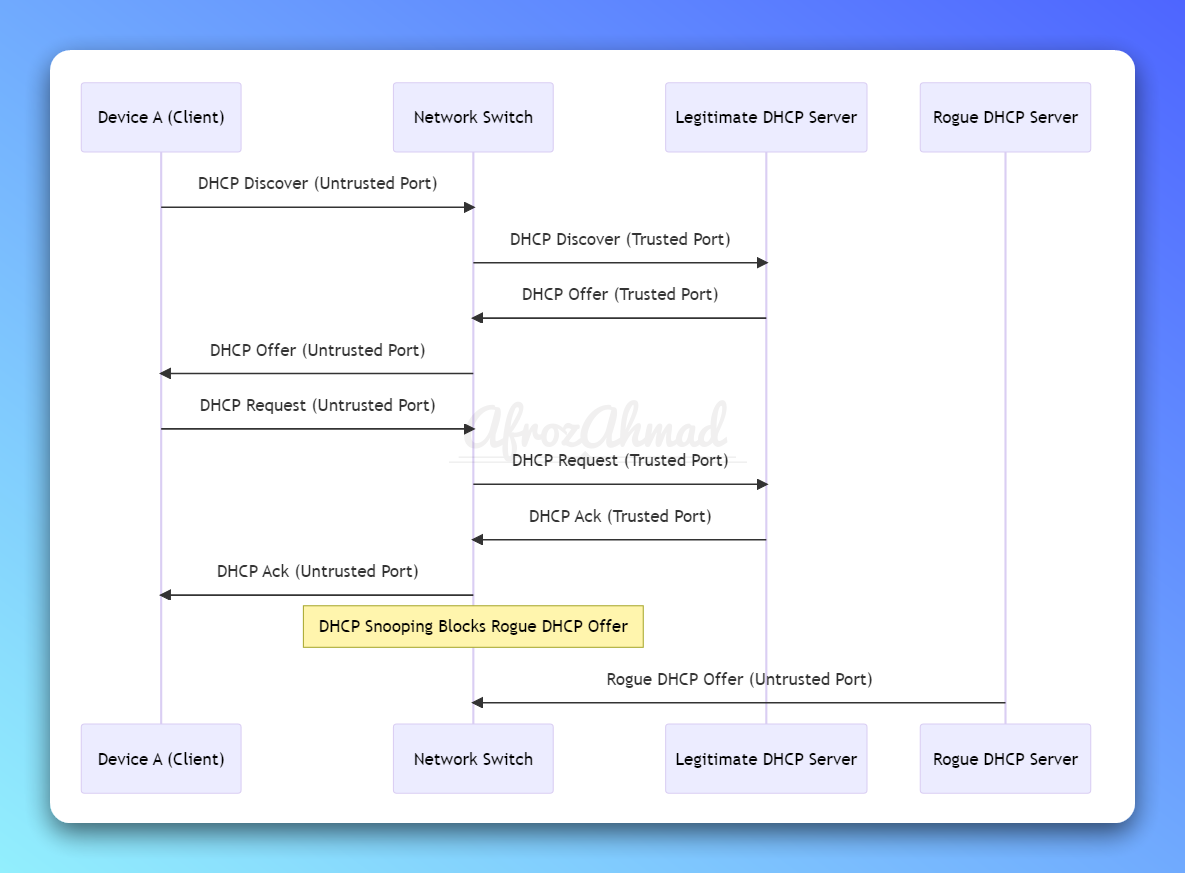
Let’s understand DHCP snooping one more time with the below diagram to solidify your knowledge.
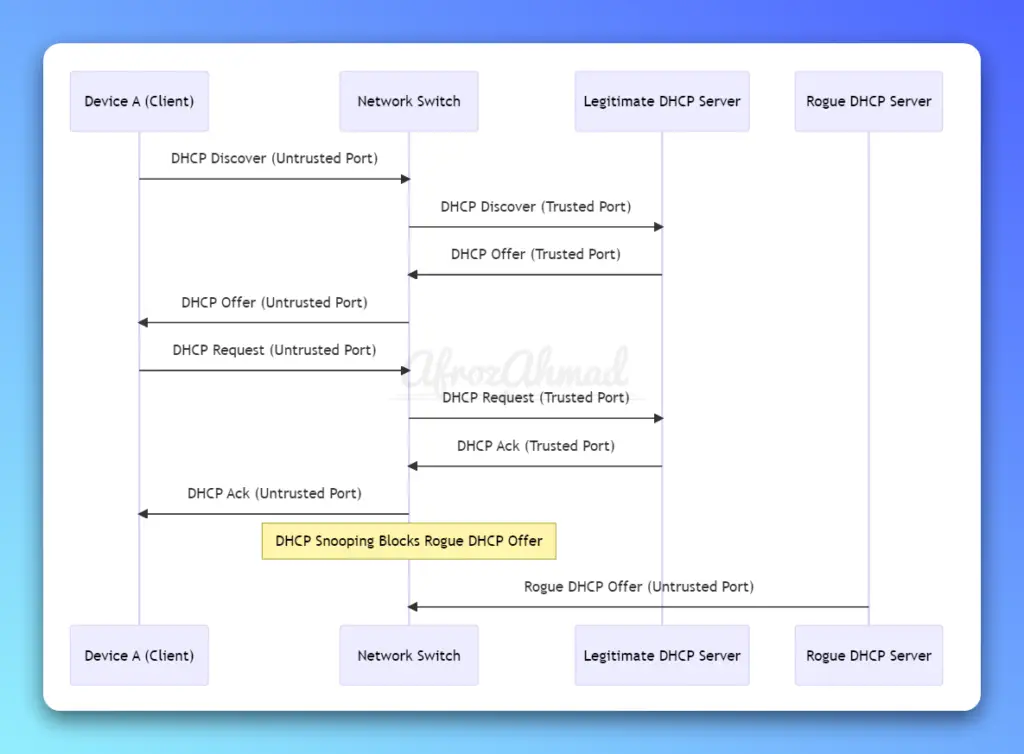
The diagram demonstrates the following DHCP snooping process:
- Device A sends a DHCP Discover message to the Network Switch.
- The Network Switch forwards the DHCP Discover message to the Legitimate DHCP Server through the trusted port.
- The Legitimate DHCP Server responds with a DHCP Offer message for Device A.
- The Network Switch forwards the DHCP Offer message to Device A through the untrusted port.
- Device A sends a DHCP Request message to the Network Switch.
- The Network Switch forwards the DHCP Request message to the Legitimate DHCP Server through the trusted port.
- The Legitimate DHCP Server sends a DHCP Ack message for Device A, confirming the IP address assignment.
- The Network Switch forwards the DHCP Ack message to Device A through the untrusted port.
Meanwhile, the Rogue DHCP Server attempts to send a DHCP Offer message to Device A, but DHCP snooping on the Network Switch blocks this message, preventing the rogue server from assigning IP addresses and causing potential network issues.
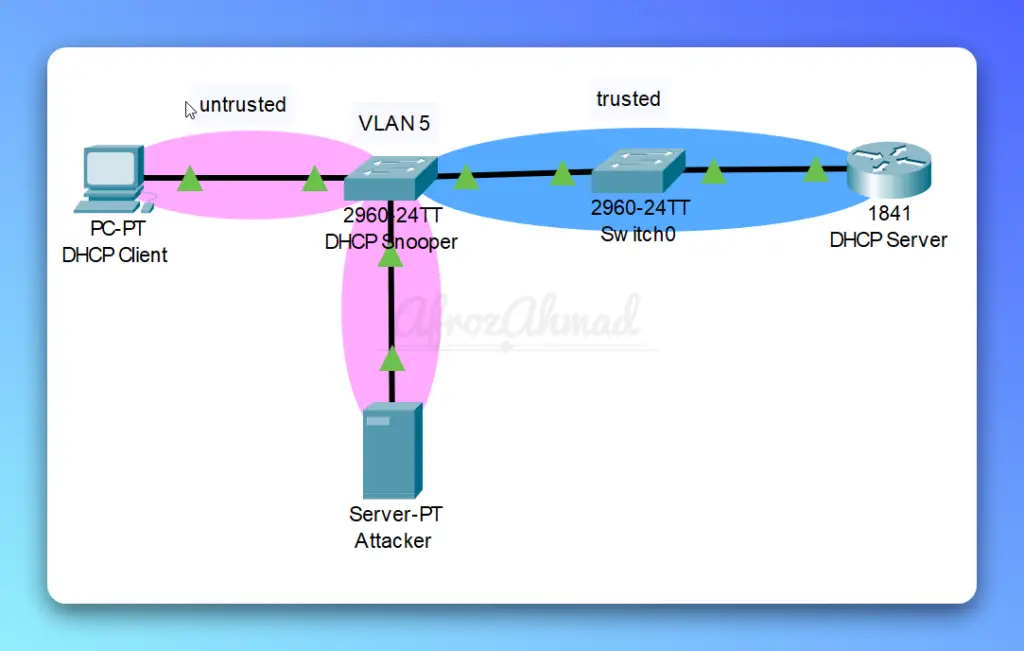
DHCP Snooping Cisco Configuration
Let’s take a sample topology example in Cisco Packet Tracer.
To configure and enable DHCP snooping on network switches and routers, follow these steps:
- Enable DHCP snooping globally:
(config)# ip dhcp snooping
- Specify the VLANs for which DHCP snooping is enabled:
(config)# ip dhcp snooping vlan <vlan-range>
Configure trusted and untrusted ports:
- Ports that are connected to a DHCP server are always configured as trusted ports.
(config-if)#interface Fa0/1
(config-if)# ip dhcp snooping trust
- Set untrusted ports for DHCP clients(by default, all ports are untrusted):
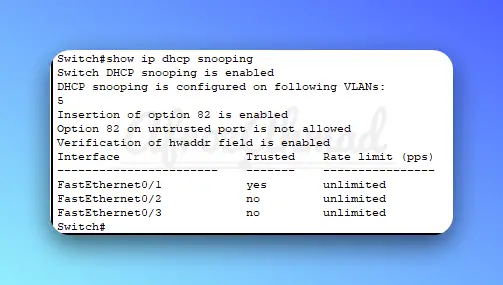
- Verify the DHCP snooping configuration:
# Switch#show ip dhcp snooping binding
# Switch# show ip dhcp snooping
Consider the specific requirements and constraints of your network environment when configuring DHCP snooping.
DHCP Snooping Binding Database: Enhancing Network Security with Dynamic ARP Inspection
The DHCP Snooping has a DHCP Snooping Binding Database, which is a dynamic table that stores information about untrusted hosts with leased IP addresses in VLANs where DHCP Snooping is enabled. This database is essential for another Layer 2 security feature called Dynamic ARP Inspection (DAI), which prevents ARP poisoning and spoofing attacks.
In a Cisco switch, the command to display the DHCP snooping binding database is “show ip dhcp snooping binding“. Here’s a sample output from a Cisco switch:
Switch# show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- ----------------
00:11:22:33:44:01 192.168.1.100 85005 dhcp-snooping 10 FastEthernet0/2
00:11:22:33:44:02 192.168.1.101 86300 dhcp-snooping 10 FastEthernet0/3
00:11:22:33:44:03 192.168.1.102 85989 dhcp-snooping 10 FastEthernet0/4
00:11:22:33:44:04 192.168.2.100 84370 dhcp-snooping 20 FastEthernet0/5
00:11:22:33:44:05 192.168.2.101 86400 dhcp-snooping 20 FastEthernet0/6
Total number of bindings: 5In this sample output:
- MacAddress: Represents the MAC addresses of the clients.
- IpAddress: Represents the IP addresses assigned to the clients by the DHCP server.
- Lease(sec): Represents the remaining lease time in seconds for the IP addresses assigned to the clients.
- Type: Indicates the type of entry (dhcp-snooping) in the binding database.
- VLAN: Represents the VLAN IDs associated with the clients’ connections.
- Interface: Represents the switch interfaces (ports) to which the clients are connected.
This output provides information about the DHCP snooping bindings, including IP-MAC address pairs, remaining lease time, associated VLANs, and switch interfaces for clients connected to untrusted ports.
Dynamic ARP Inspection (DAI) uses the information in the DHCP Snooping Binding Database to validate Address Resolution Protocol (ARP) requests and replies. By doing so, DAI ensures that only valid ARP messages are forwarded within the network, preventing attackers from manipulating ARP tables and launching man-in-the-middle attacks.
Traffic Dropped by DHCP Snooping and Violation Syslog Messages
DHCP Snooping monitors and drops specific types of DHCP traffic to protect the network from rogue DHCP servers and other threats. Some traffic dropped by DHCP Snooping includes:
- DHCP server messages (DHCPACK, DHCPNAK, DHCPOFFER) from untrusted ports.
- DHCP messages that release or decline an offer, if not originating from the original port of the DHCP conversation.
- DHCP packets with mismatched source MAC addresses and client MAC addresses.
If a violation is detected by DHCP Snooping, the packet(s) causing the violation will be dropped, and a message will be logged in the switch’s syslog. These messages can assist network administrators in identifying potential security threats and taking necessary actions.
Potential Limitations and Challenges
Some potential limitations and challenges associated with DHCP snooping include:
- Increased processing load on network devices
- Possible misconfigurations that can disrupt network functionality
Best Practices for DHCP Snooping
To effectively deploy and manage DHCP snooping in a network environment, follow these best practices:
- Regularly review and update trusted and untrusted port configurations
- Monitor network traffic for signs of unauthorized DHCP activity
- Continuously test and validate the effectiveness of DHCP snooping configurations
Combining DHCP snooping with other security technologies – DAI, IP Source Guard, Port Security
Combining DHCP snooping with other security technologies on switches can create a more robust and secure network environment. Some of the complementary technologies include:
- Dynamic ARP Inspection (DAI): As mentioned above. DAI is a security feature that prevents Address Resolution Protocol (ARP) poisoning and man-in-the-middle attacks by validating ARP packets in the network. It uses the DHCP snooping binding database to ensure that the IP-MAC address bindings in ARP packets are legitimate. If an ARP packet contains invalid bindings, the switch discards it, preventing the poisoning of the ARP cache.
- IP Source Guard (IPSG): IPSG is another security feature that helps prevent IP spoofing attacks by filtering IP traffic based on the source IP address and VLAN information. It leverages the DHCP snooping binding database to create a whitelist of allowed IP-MAC address bindings and blocks traffic from IP addresses not present in the whitelist. This ensures that only legitimate devices can send traffic on the network, preventing attackers from impersonating other devices.
- Port Security: Port security is a feature that restricts the number of MAC addresses allowed on a specific switch port. It can be used in conjunction with DHCP snooping to limit the number of devices that can connect to a specific port, further reducing the risk of unauthorized devices or rogue DHCP servers gaining access to the network.
- VLAN Security: Properly segregating and configuring VLANs in the network can help enhance security by isolating different types of traffic and limiting the broadcast domain. Combining VLAN security with DHCP snooping ensures that rogue DHCP servers cannot provide IP configurations across VLAN boundaries.
- Private VLANs (PVLANs): PVLANs provide additional layer 2 security by further segregating devices within the same VLAN. They prevent devices from communicating directly with each other, forcing all communication through an upstream device, such as a router or firewall. This can help prevent the spread of rogue DHCP servers and limit their impact on the network.
- Access Control Lists (ACLs): ACLs can be used to filter traffic at the layer 3 level, allowing or denying specific IP addresses or protocols. By applying ACLs in conjunction with DHCP snooping, you can further restrict unauthorized devices or services from accessing critical network resources.
By combining DHCP snooping with these additional security technologies, you can create a more robust and secure network environment that is better equipped to prevent and mitigate threats from rogue DHCP servers and other types of attacks.
Conclusion
DHCP Snooping is a crucial network security feature that helps protect your network infrastructure from DHCP-based attacks and rogue DHCP servers. By understanding its importance and how it works, you can effectively configure and manage DHCP Snooping in your network environment.
Combining DHCP Snooping with other security technologies like Dynamic ARP Inspection, IP Source Guard, and Port Security will further enhance your network’s security posture. While there may be some limitations and challenges in implementing DHCP Snooping, by following best practices and staying vigilant, you can maintain secure and reliable network infrastructure.
FAQs
What does DHCP snooping protect against?
DHCP snooping is a security feature implemented on Layer 2 switches that provides protection against various security threats and attacks, primarily related to rogue DHCP servers and DHCP-based attacks. Some of the key threats that DHCP snooping protects against include the following:
- Rogue DHCP Servers: DHCP snooping prevents rogue or unauthorized DHCP servers from distributing malicious or incorrect network configuration information to clients. By filtering DHCP messages on untrusted ports, DHCP snooping ensures that clients receive valid configurations only from authorized DHCP servers.
- Man-in-the-Middle Attacks: In this type of attack, an attacker intercepts and potentially alters the communication between two parties. Rogue DHCP servers can be used to perform man-in-the-middle attacks by providing clients with an incorrect gateway or DNS server information, redirecting their network traffic through the attacker’s device.
- DHCP Starvation Attacks: An attacker can flood a DHCP server with numerous DHCPDISCOVER requests, consuming all available IP addresses in the DHCP pool and preventing legitimate clients from obtaining IP addresses. DHCP snooping can limit the rate of DHCP messages received on untrusted ports, mitigating the impact of DHCP starvation attacks.
- IP Spoofing: DHCP snooping maintains a binding database of IP-MAC address pairs, which can be used by other security features like IP Source Guard and Dynamic ARP Inspection to prevent IP spoofing attacks. By ensuring that only legitimate devices with valid IP-MAC address bindings can send traffic on the network, DHCP snooping helps prevent attackers from impersonating other devices.
- ARP Poisoning: Although DHCP snooping doesn’t directly protect against ARP poisoning, it plays a crucial role in enabling Dynamic ARP Inspection (DAI), which does. DAI relies on the DHCP snooping binding database to validate the legitimacy of ARP packets and prevent ARP cache poisoning.
In summary, DHCP snooping helps protect against various network threats and attacks, primarily rogue DHCP servers, by monitoring and filtering DHCP messages on untrusted ports, maintaining a binding database, and facilitating other security features like DAI and IP Source Guard.