- Maximizing BGP Security with BGP Filtering Best Practices: Techniques and Guidelines for Using AS-Path Filters, Distribute-Lists, Prefix-Filters, and More.
- BGP Filtering Techniques – AS-Path Filters
- BGP Filtering using AS-Path Access-List to prevent being used as transit BGP AS
- BGP Filtering Techniques – Distribute-Lists
- BGP Filtering Techniques – Prefix-Lists
- Best Practices for BGP Filtering – Planning And Design
- Best Practices for BGP Filtering – Implementation and deployment
- Best Practices for BGP Filtering – Maintenance and updates
- Conclusion
Maximizing BGP Security with BGP Filtering Best Practices: Techniques and Guidelines for Using AS-Path Filters, Distribute-Lists, Prefix-Filters, and More.
Greetings, fellow networking enthusiasts! Today we’re going to dive into the exciting world of Border Gateway Protocol (BGP) security and the magic of BGP filtering. As you may already know, BGP is the routing protocol that helps guide data packets through the vast and complex network that makes up the internet. It’s like a GPS system for the internet!
But, like with any road trip, there’s always the risk of taking a detour through a sketchy neighborhood. In the internet world, these sketchy neighborhoods can be represented by malicious actors who want to hijack or redirect traffic for their own gain. That’s where BGP filtering comes in to save the day!
BGP filtering is like having a security guard at the door of your network, only allowing trusted routes and filtering out any unwanted ones. And just like with a good security guard, it’s important to have solid BGP filtering best practices in place to ensure maximum security.
So sit back, grab your favorite caffeinated beverage, and let’s dive into the wonderful world of BGP filtering and its role in maximizing BGP security!
BGP Filtering Techniques – AS-Path Filters
Definition and purpose
AS-Path Filters can be like the secret agents of the BGP filtering world! They use the AS-path list to selectively filter routes, choosing only the most trustworthy data packets to let into your network.
When it comes to incoming routes, AS-Path filters work like a secret door at a VIP party. Only the permitted routes are allowed in and added to the local BGP table, while the denied routes are silently dropped, like a party crasher trying to sneak in.
For outgoing routes, AS-Path filters are like a trusty messenger. The permitted routes are transmitted to the neighbor, while the denied routes are never sent, like a message that’s too sensitive to send to just anyone.
How to create and apply AS-Path filters
ip as-path access-list [ACCESS_LIST_NAME] permit [AS_PATH_REGEX]
! specify the AS path regular expression
!
router bgp [AS_NUMBER]
! specify the AS number
!
neighbor [IP_ADDRESS] filter-list [ACCESS_LIST_NAME] in
! apply the AS-Path filter to incoming routes from the BGP neighbor
neighbor [IP_ADDRESS] filter-list [ACCESS_LIST_NAME] out
! apply the AS-Path filter to outgoing routes to the BGP neighborAnd to verify your AS-Path filter configuration:
show ip bgp neighbor [IP_ADDRESS] received-routes
! display the received routes from the specified BGP neighbor
!
show ip bgp neighbors [IP_ADDRESS] filters
! display the applied filters on the specified BGP neighborBGP Filtering Best Practices for using AS-Path filters
BGP Filtering Best Practices for using AS-Path filters
- Regularly review and update your AS-Path filters to ensure maximum security.
- Use different filters for different types of data packets, just like having different VIP lists for different areas of your party.
- Test your filters before applying them in a production environment.
- Document your AS-Path filter configuration for future reference.
BGP Filtering using AS-Path Access-List to prevent being used as transit BGP AS
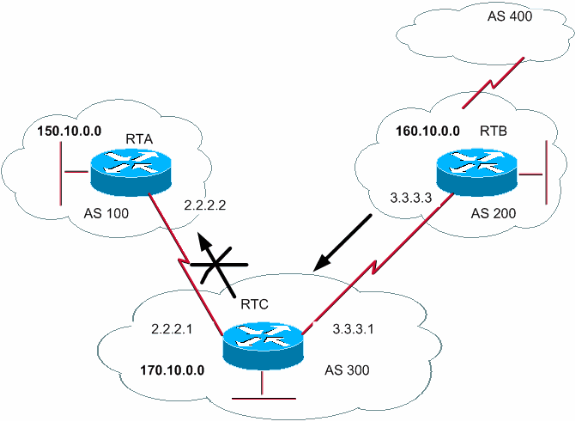
One of the most important things to do with BGP in a dual-homing network is to stop our BGP AS number from being used as a transit AS between two service providers. Although there are several methods to perform them, for example, using BGP communities, etc. One easy approach is to use BGP filtering to achieve this design.
- Suppose our AS is 300, and we don’t want BGP AS 200 to use our AS as a transit AS. We are able to accomplish this through the use of an “IP as-path access-list” and by matching the as-path and then filtering it to the desired neighbor by BGP “filter-list”. Below is an example –
- The syntax of AS-PATH access-list.
RTC(conf)#ip as-path access-list 13 allow ^$
Right here ^ matches the beginning of the string.
Right here, $ matches the end of the string.
- The syntax of the BGP filter-list.
router bgp 300
neighbor[ip address] filter-list 13 out
By doing this, we are only advertising network prefixes originating in our local AS, which is AS300, to our neighbors in AS100 and AS200. The result of this filter list will be that AS 200 will not be able to use AS 300 to reach AS 100. This is achieved by using filtering primarily based on AS-PATH data. Because the AS-PATH of a prefix is not added when the prefix leaves the AS, prefixes that have originated inside the AS could have an empty AS-PATH.
This may be simply matched with a regular expression that specifies that the end of the as-path string comes instantly after the beginning of the as-path string and is denoted as ^$.
You can use the below command to check the configuration:-
R1#show ip bgp neighbors [ip address of EBGP Neighbor] advertised-routes
BGP Filtering Techniques – Distribute-Lists
Definition and purpose:
Distribute-lists, my friend, are like bouncers at a popular nightclub. They control who gets in and who doesn’t. In BGP, distribute-lists act as filters for incoming or outgoing routes. They help you control which routes are advertised or accepted from a neighboring router. With distribute-lists, you can be in charge of what routes enter or exit your network, giving you the power to control your network’s traffic flow.
How to create and apply Distribute-lists:
Creating a distribute-list is quite simple. You can do it with just a few lines of configuration. Here’s an Example of creating a distribute-list in Cisco IOS:
Router(config)# ip access-list standard 10
Router(config-std-nacl)# 10 permit 11.11.11.0 0.0.0.255
Router(config-std-nacl)# 20 deny anyOnce you’ve created the distribute-list, you can apply it to a BGP neighbor by using the following configuration:
Router(config)# router bgp 100
Router(config-router)# neighbor 1.1.1.1 distribute-list 10 inWith this configuration, all incoming routes from the 1.1.1.1 neighbor will be checked against the distribute-list before being accepted into the BGP table.
BGP Filtering Best Practices for using distribute-lists:
Here are a few tips:
- Always keep your distribute-lists up-to-date and relevant. This helps prevent unwanted routes from entering your network.
- Extended access lists should be used instead of standard access lists because standard ACLs have a fundamental flaw: they cannot exactly match the length of a network mask, allowing more than the intended length.
- Use a combination of distribute-lists and prefix-lists for a more comprehensive filtering approach. This can help prevent potential routing loops and other issues.
- Use the “show ip bgp” command to verify your distribute-lists and ensure they’re working as intended.
- Regularly monitor your BGP sessions and routes to catch any potential issues early on.
BGP Filtering Techniques – Prefix-Lists
Definition and purpose:
Prefix-filters, my friend, are like sieves in a kitchen. They sort out the unwanted bits and keep only what you want. In BGP, prefix-filters act as filters for incoming or outgoing routes based on the prefixes of the routes. They help you control which routes are advertised or accepted from a neighboring router based on the prefix of the route. With prefix-filters, you can be in charge of what routes enter or exit your network, giving you the power to control your network’s traffic flow.
How to create and apply prefix-filters:
Creating a prefix-filter is a snap. You can do it with just a few lines of configuration.
Here’s an example of creating a prefix-filter in Cisco IOS:
Router(config)# ip prefix-list prefix-filter seq 5 permit 11.11.11.0/24
Router(config)# ip prefix-list prefix-filter seq 10 deny 0.0.0.0/0 le 32Once you’ve created the prefix-filter, you can apply it to a BGP neighbor by using the following configuration:
Router(config)# router bgp 100
Router(config-router)# neighbor 1.1.1.1 prefix-list prefix-filter inWith this configuration, all incoming routes from the 1.1.1.1 neighbor will be checked against the prefix-filter before being accepted into the BGP table.
BGP Filtering Best Practices for using prefix-filters:
Here are a few tips:
- Always keep your prefix-filters up-to-date and relevant. This helps prevent unwanted routes from entering your network.
- Use a combination of distribute-lists and prefix-filters for a more comprehensive filtering approach. This can help prevent potential routing loops and other issues.
- Use the “show ip bgp” command to verify your prefix-filters and ensure they’re working as intended.
- Regularly monitor your BGP sessions and routes to catch any potential issues early on.
Best Practices for BGP Filtering – Planning And Design
Aha! You’re now ready to take your BGP filtering to the next level! We’ll start with planning and design, the cornerstone of a successful BGP filtering implementation. Here’s what you need to keep in mind.
Defining BGP filtering requirements and goals:
Before you start, it’s important to know what you’re aiming for. Ask yourself, what kind of traffic do you want to allow or block in your network? This will help you determine the BGP filtering requirements and goals. It’s like deciding what kind of pizza you want to order before you pick up the phone – you want to make sure you get what you want!
Identifying potential risks and threats:
Once you know what you want, it’s time to look for potential risks and threats. What kind of malicious traffic could your network be exposed to? Who do you need to protect your network from? It’s like looking out for the boogie man before you go to bed. You want to make sure you’re protected!
Evaluating BGP filtering options:
Finally, it’s time to evaluate the different BGP filtering options available. What techniques and tools will best suit your needs? Which ones are the most secure and effective? It’s like trying on different outfits before you go out on a date. You want to make sure you look and feel your best!
So, that’s the planning and design stage done and dusted. Now it’s time to move on to the next step: implementation and deployment!
Best Practices for BGP Filtering – Implementation and deployment
Awesome, you’ve made it to the implementation and deployment stage! This is where the rubber meets the road, so let’s make sure we do it right.
Testing BGP filtering rules in a lab environment:
Before you deploy BGP filtering rules in a production environment, it’s important to test them in a lab environment first. This allows you to fine-tune the rules and make sure they’re working as expected. It’s like a dress rehearsal before a big performance. You want to make sure everything is perfect before you hit the stage!
Monitoring BGP sessions and routes:
Once you’ve deployed the BGP filtering rules, it’s important to monitor the BGP sessions and routes to make sure everything is working as expected. You want to make sure your network is secure and that the filtering rules are having the desired effect. It’s like keeping an eye on your pizza in the oven to make sure it doesn’t burn!
Documenting BGP filtering rules and policies:
Finally, it’s important to document the BGP filtering rules and policies so that others can understand what you’ve done and why. This makes it easier for others to maintain and update the filtering rules in the future. It’s like writing down a recipe for a delicious dish so that others can follow it and make it again.
And that’s it! You’re now ready to deploy BGP filtering in your network. Just remember to stay vigilant and keep monitoring your BGP sessions and routes. The internet is a big and ever-changing place, so it’s important to keep your BGP filtering up-to-date.
Best Practices for BGP Filtering – Maintenance and updates
So let’s talk about maintenance and updates of your BGP filtering rules. This is an important aspect of BGP security that often gets overlooked, but it’s crucial to keep your network secure.
Regularly reviewing and updating BGP filtering rules
First, you should regularly review and update your BGP filtering rules. This will help you keep up with changes in your network and ensure that your filtering rules are still effective in protecting against potential threats. Think of it like brushing your teeth – it’s a simple task that you should do regularly to keep things in check.
Testing BGP filtering rules after updates
Next, after you’ve made any updates to your filtering rules, it’s important to test them. This is like taking a sip of water after brushing your teeth – you want to make sure everything is working as it should. Testing your filtering rules in a lab environment before deploying them to your live network will help you avoid any unexpected issues and ensure that your network remains secure.
Documenting changes and updates
Finally, it’s essential to document any changes and updates to your filtering rules. This is like writing down what you did at the dentist – you want to make sure you have a record of what you did in case you need to refer back to it later. Documenting changes and updates to your filtering rules will also help you keep track of what’s changed over time and ensure that everyone involved in managing your network is on the same page.
Conclusion
Once you’ve set up your AS-Path filters, distribute-lists, and prefix-list filters, be sure to test them out in a safe environment before rolling them out live. It’s best practice to keep BGP traffic isolated from your general internal network traffic. And remember, it may be tempting to create huge and complex filters with the intention of completely locking down your network. Remember that less is more! Going overboard with complex filtering could potentially block legitimate routes from reaching the gateway.
Hopefully, this post covered a little bit of everything. There’s a lot to consider when it comes to BGP, but don’t let that intimidate you. Every network has its own set of requirements, and there isn’t one solution that will work for everyone (at least not yet). By implementing some security best practices and using a combination of filters on your networks, you should be well on your way to filtering out the bad routes and keeping your data safe!