Spanning Tree Protocol (STP) remains a critical Layer 2 defense mechanism, even in the age of advanced network fabrics. The STP Root Guard feature is an indispensable tool for preventing rogue switches from becoming the root bridge, thus maintaining network stability and predictable traffic flow. Originally published in 2011, I have thoroughly revised it for the current networking landscape, emphasizing modern best practices, automation, and observability.
Understanding STP Root Guard
Root Guard is a crucial STP enhancement designed to protect the integrity of your Spanning Tree topology. It helps prevent Layer 2 loops and ensures that the designated root bridge, typically a high-performance core switch, maintains its role.
This feature forces an interface to operate as a designated port, actively preventing any connected switch from becoming the root bridge. When a port enabled with Root Guard receives superior STP Bridge Protocol Data Units (BPDUs)—indicating a potential rogue root bridge—the port immediately moves to a root-inconsistent STP state. This state effectively blocks traffic and prevents the undesirable root bridge takeover, enforcing your network’s designed STP hierarchy.
Illustrative Scenario: The Importance of Root Guard
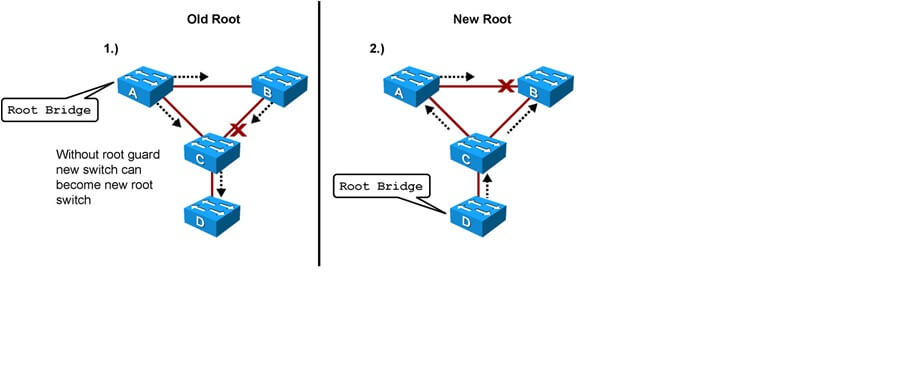
Consider the following network topology:
- Switches A and B form the core, with Switch A serving as the designated root bridge for the network.
- Switch C is an access layer switch.
Now, imagine an unauthorized Switch D (perhaps a misconfigured device or a user’s personal switch) is connected to Switch C. If Switch D has a lower STP priority (or a lower MAC address in a tie-break scenario) than Switch A, it could attempt to become the new root bridge.
This scenario is highly undesirable. If Switch D becomes the root, it could force the high-bandwidth Gigabit Ethernet link between core Switches A and B to block. Consequently, all network traffic might be rerouted through a slower, 100-Mbps link via the access layer through Switch D. Such an outcome significantly degrades network performance and introduces instability.
By enabling Root Guard on the port connecting Switch C to Switch D, Switch C will block that port upon receiving superior BPDUs from Switch D. The port transitions to a root-inconsistent STP state, preventing Switch D from influencing the STP topology. No traffic will pass through the port while it’s in this state.
A key advantage of Root Guard is its automatic recovery. When Switch D stops sending superior BPDUs (e.g., if it’s removed or reconfigured), the port on Switch C will automatically unblock. It will then proceed through the standard STP listening and learning states before transitioning back to the forwarding state, requiring no manual intervention.
Identifying Root Guard Events
When a Root Guard-enabled port detects a superior BPDU, Cisco switches log messages similar to this:
%SPANTREE-2-ROOTGUARDBLOCK: Port 1/1 tried to become non-designated in VLAN 77.
Moved to root-inconsistent state.
To check which ports are currently in a root-inconsistent state, you can use the following command:
Switch# show spanning-tree inconsistentports
Name Interface Inconsistency
---------- ----------- --------------------
VLAN0001 FastEthernet3/1 Port Type Inconsistent
VLAN0001 FastEthernet3/2 Port Type Inconsistent
VLAN1002 FastEthernet3/1 Port Type Inconsistent
VLAN1002 FastEthernet3/2 Port Type Inconsistent
Number of inconsistent ports (segments) in the system :4
Modern Best Practices for Root Guard Deployment
The current design recommendation remains robust: enable Root Guard on all access layer ports and any port where a root bridge should never be established. This includes access ports on core and distribution switches that connect to downstream devices or other network segments.
- Switch A (Distribution/Core): Any access port connecting to non-core infrastructure.
- Switch B (Distribution/Core): Any access port connecting to non-core infrastructure.
- Switch C (Access): Any access port, including the port connecting to potentially rogue devices like Switch D.
Configuration Examples Across Vendors
While the concept of Root Guard is universal, syntax may vary slightly across different networking platforms.
Cisco IOS/IOS-XE
The configuration on Cisco devices is straightforward and remains consistent:
Switch(config)# interface FastEthernet 5/8
Switch(config-if)# spanning-tree guard root
Switch(config-if)# end
Verification of the configuration:
Switch# show running-config interface FastEthernet 5/8
Building configuration...
Current configuration: 67 bytes
!
interface FastEthernet5/8
switchport mode access
spanning-tree guard root
end
Juniper Junos OS
For Juniper devices, you would configure Root Guard (part of BPDU protection) under the STP interface settings:
edit protocols rstp interface ge-0/0/1
set bpdu-protection
This enables BPDU protection, which includes the functionality similar to Root Guard, preventing interfaces from becoming root ports.
Arista EOS
Arista EOS provides a similar command structure to Cisco for consistency:
switch(config)# interface Ethernet 1
switch(config-if)# spanning-tree guard root
switch(config-if)# end
Automation and Observability for STP Guard Controls
Intent-Based and Automated Enforcement of Root Guard Policies
In modern networks, manually configuring Root Guard on every port is no longer scalable or efficient. Intent-Based Networking (IBN) platforms like Cisco DNA Center, Juniper Apstra, and Arista CloudVision allow network architects to define security policies (such as “all access ports must have Root Guard enabled”) as high-level intent. These platforms then translate this intent into device-specific configurations and continuously monitor compliance.
This approach ensures consistent policy application across large deployments and can even provide auto-remediation if policy drift is detected.
Event-Driven Automation for STP Security Events
The automatic recovery of Root Guard is excellent, but knowing when and where these events occur is critical. Event-Driven Automation (EDA) leverages real-time network events (like a port entering root-inconsistent state) to trigger automated actions.
Tools like Ansible Automation Platform, combined with network automation frameworks (e.g., Nornir with Scrapli), can:
- Send immediate alerts to monitoring systems or NOC teams.
- Automatically capture diagnostic information (e.g.,
show spanning-tree inconsistentports,show interface details). - Initiate remediation workflows if the event is persistent or part of a larger security incident.
Here’s a conceptual Ansible playbook snippet for auditing Root Guard status:
---
- name: Audit Root Guard status on network devices
hosts: network_devices
gather_facts: false
tasks:
- name: Get interface configurations
cisco.ios.ios_command:
commands:
- show running-config | section interface
register: interface_configs
when: ansible_network_os == 'ios' # Example for Cisco IOS
- name: Check for spanning-tree guard root on interfaces
ansible.builtin.debug:
msg: "Interface {{ item.split(' ')[1] }} has Root Guard configured."
loop: "{{ interface_configs.stdout[0].split('\n') }}"
when:
- 'spanning-tree guard root' in item
- ansible_network_os == 'ios'
This type of automation allows for proactive monitoring and rapid response to STP security violations.
Network Observability and Telemetry for Root Guard Enforcement
Beyond simple SNMP traps, modern network observability platforms leverage advanced telemetry (e.g., streaming telemetry, gNMI/gRPC) to provide granular, real-time insights into STP operations and Root Guard states.
- Baseline STP Topology: Continuously monitor and baseline the STP topology to detect any deviations from the intended root bridge or path costs.
- Anomaly Detection: Automatically flag abnormal
root-inconsistentstates, port blocking events, or unexpected BPDU patterns. - Cross-Vendor Reporting: Integrate data from various vendors (Cisco, Juniper, Arista) into a unified dashboard for comprehensive network health visibility.
- Historical Analysis: Analyze past Root Guard events to identify trends, potential attack vectors, or recurring misconfigurations.
STP Protection as an Element of Zero Trust Access Control
Root Guard, alongside other port security features like BPDU Guard and port security, forms a critical component of a comprehensive Zero Trust Network Access (ZTNA) strategy at the access layer.
In a Zero Trust model, every connection attempt is verified. An unauthorized device attempting to become an STP root bridge is a clear policy violation. Events triggered by Root Guard can be integrated with Network Access Control (NAC) solutions to:
- Automatically quarantine the offending port or device.
- Trigger further security assessments or block the MAC address entirely.
- Provide context to endpoint orchestration systems, enhancing the overall security posture.
STP Guard Controls in EVPN/VXLAN Data Center Fabrics
While traditional STP is typically replaced by BGP EVPN (Ethernet VPN) in modern VXLAN-based data centers, the concept of protecting against rogue devices at the fabric edge remains important. In these environments, classic STP might not run within the VXLAN overlay, but it often operates on the underlay network or at the fabric edge (where non-VXLAN devices connect).
Here, Root Guard, along with BPDU Guard, remains relevant on:
- Edge ports: Connecting to traditional Layer 2 devices or tenant equipment outside the VXLAN fabric.
- Underlay links: If a traditional STP is used for underlay redundancy (less common but possible).
The principle of preventing an unauthorized root bridge from disrupting the logical network segmentation or underlay routing stability still applies, though the enforcement points and monitoring mechanisms might integrate more closely with the EVPN control plane and data center orchestration tools.
Conclusion
The STP Root Guard feature continues to be a foundational security control for Layer 2 networks. While its core functionality remains unchanged, its deployment and monitoring have evolved significantly. By integrating Root Guard with Intent-Based Networking, Event-Driven Automation, advanced Observability, and Zero Trust principles, network engineers can build more resilient, secure, and self-healing networks. Proactive implementation and automated monitoring of Root Guard ensure that your network’s STP topology remains stable, protecting against disruptions from misconfigurations or malicious attempts to hijack the root bridge.
- Telecom Network Infrastructure: Complete Guide to Components & Design - January 6, 2026
- TP-Link TL-SG108E vs Netgear GS308E: Budget Smart Switches - January 5, 2026
- MikroTik CRS305-1G-4S+ Review: The Ultimate Budget SFP+ Switch Guide - December 25, 2025