STP RootGuard Feature
§Root guard is useful in avoiding Layer 2 loops during network anomalies. The Root guard feature forces an interface to become a designated port to prevent surrounding switches from becoming root bridges.
§Root guard-enabled ports are forced to be designated ports. If the bridge receives superior STP BPDUs on a Root guard-enabled port, the port moves to a root-inconsistent STP state, which is effectively equivalent to the STP listening state, and the switch does not forward traffic out of that port. As a result, this feature enforces the position of the root bridge.
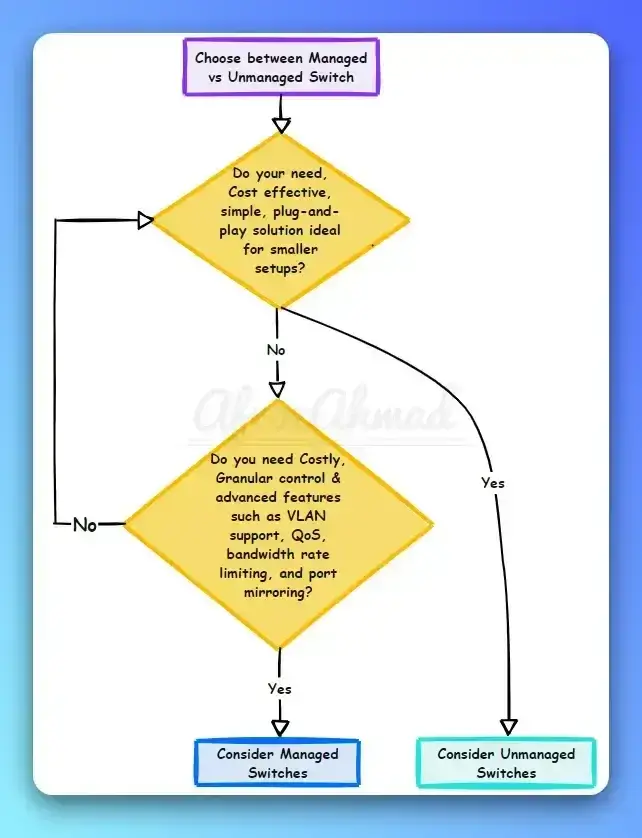
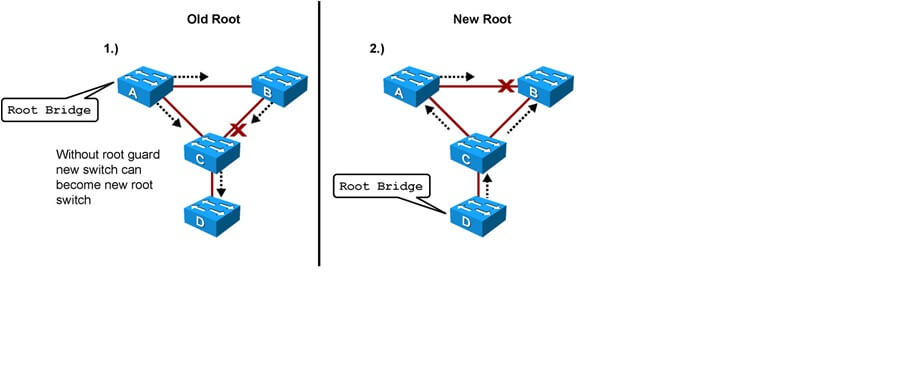
Here in the above picture:-
§Switches A and B comprise the core of the network. Switch A is the root bridge.
§Switch C is an access layer switch. When Switch D is connected to Switch C, it begins to participate in STP. If the priority of Switch D is 0 or any value lower than that of the current root bridge, Switch D becomes the root bridge.
§Having Switch D as the root causes the Gigabit Ethernet link connecting the two core switches to block, thus causing all the data to flow via a 100-Mbps link across the access layer. This is obviously a terrible outcome.
§After the root guard feature is enabled on a port, the switch does not enable that port to become an STP root port.
§Cisco switches log the following message when a root guard–enabled port receives a superior BPDU:
%SPANTREE-2-ROOTGUARDBLOCK: Port 1/1 tried to become non-designated in VLAN 77.
Moved to root-inconsistent state.
§The current design recommendation is to enable root guard on all access ports so that a root bridge is not established through these ports.
§In this configuration, Switch C blocks the port connecting to Switch D when it receives a superior BPDU. The port transitions to the root-inconsistent STP state. No traffic passes through the port while it is in root-inconsistent state.
§When Switch D stops sending superior BPDUs, the port unblocks again and goes through regular STP transition of listening and learning, and eventually to the forwarding state. Recovery is automatic; no intervention is required.
Enable Root Guard on Switches A, B, and C on the following ports:
•Switch A (Distribution/Core): Any access port
•Switch B (Distribution/Core): Any access port
•Switch C (Access): Any access port including the port connecting to Switch D
The configuration can be done:-
Switch(config)# interface FastEthernet 5/8
Switch(config-if)# spanning-tree guard root
Switch(config-if)# end
Switch# show running-config interface FastEthernet 5/8
Building configuration…
Current configuration: 67 bytes
!
interface FastEthernet5/8
switchport mode access
spanning-tree guard root
end
Important command to check the ports that are in Root-inconsistent state:-
Switch# show spanning-tree inconsistentports
Name Interface Inconsistency
——————– ———————- ——————
VLAN0001 FastEthernet3/1 Port Type Inconsistent
VLAN0001 FastEthernet3/2 Port Type Inconsistent
VLAN1002 FastEthernet3/1 Port Type Inconsistent
VLAN1002 FastEthernet3/2 Port Type Inconsistent
Number of inconsistent ports (segments) in the system :4
•Ports in root inconsistent recover automatically with no human intervention after the port stop receiving superior BPDUs. The port goes through the listening state to the learning state, and eventually transitions to the forwarding state.
I'm Afroz, a Network Engineer and CCIE with 17 years of experience in Computer Networking, Data Centers, Telecom, Internet Services and ISPs. Currently, I work as a Network Designer for a leading ISP equipment vendor. I share my expertise through my blog and courses, aiming to share my knowledge and simplify complex networking concepts for both beginners and experienced professionals.
Latest posts by Afroz Ahmad
(see all)