This article provides comprehensive coverage of OSPF authentication, including an explanation of what it is, why you should actively use it, and how to configure and troubleshoot it.
I would recommend you go through these posts to grasp a solid understanding of OSPF.
- What is OSPF in Networking
- OSPF States
- Types of OSPF Routers
- OSPF LSA Types
- OSPF Area Types
- OSPF Network Types
- OSPF Virtual Link
- OSPF Path Selection Process
What is OSPF authentication?
OSPF authentication is a security measure that you can use to protect OSPF routing information from being modified or tampered with. When OSPF authentication is enabled, each router must authenticate itself before exchanging routing information with other routers. This authentication can be done using a simple clear-text password, or it can be done using more sophisticated methods such as MD5 cryptographic checksums.
Why use OSPF authentication?
One of the main reasons to use OSPF authentication is to prevent unauthorized devices from forming an OSPF neighborship, which in turn prohibits accessing and manipulating the network. By authenticating devices, OSPF can ensure that only authorized devices can establish an OSPF neighborship, access the network, and make changes. This can help to improve security and prevent unauthorized access and modifications.
OSPF authentication can also help improve performance by making sure that only approved devices can connect to the network. This can help reduce traffic and improve overall performance.
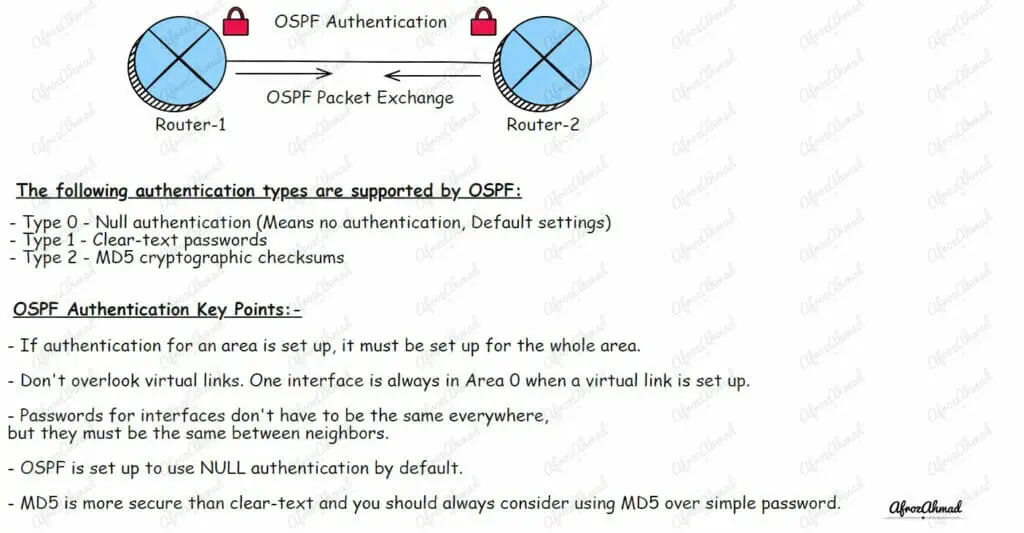
OSPF Authentication Key Points:-
- If authentication for an area is set up, it must be set up for the whole area.
- Don’t overlook virtual links. One interface is always in Area 0 when a virtual link is set up.
- Passwords for interfaces don’t have to be the same everywhere, but they must be the same between neighbors.
- OSPF is set up to use NULL authentication by default.
- MD5 is more secure than clear text, and you should always consider using MD5 over a simple password.
Which type of authentication is used by the OSPF protocol?
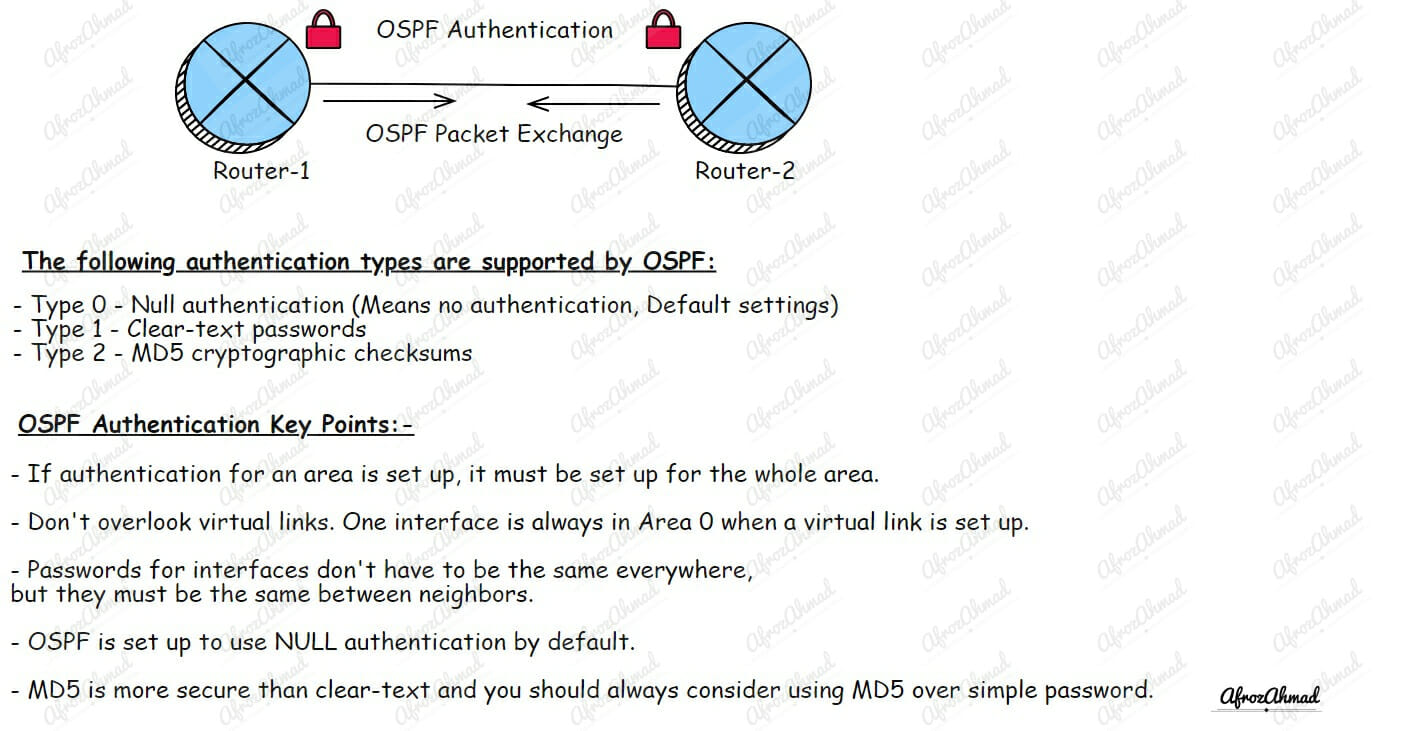
The following authentication types are used and supported by OSPF:
- Type 0 – Null authentication (Means no authentication, Default settings)
- Type 1 – Clear-text passwords
- Type 2 – MD5 cryptographic checksums
How does OSPF authentication work?
The Open Shortest Path First (OSPF) is a link-state routing protocol for Internet Protocol (IP) networks. It uses the “shortest path first” (SPF) technique to calculate the best path through a network. OSPF is a widely used interior gateway protocol (IGP).
One of the key features of OSPF is that it supports authentication. This means each router can verify the identity of the other routers it communicates with. Two types of authentication can be used with OSPF: simple password authentication and MD5 authentication.
OSPF plain text authentication (Type 1) is the most basic form. With this method, each router has a clear-text password configured that it uses to authenticate with other routers. The problem with this authentication method is that the password is shown in the configuration and in OSPF messages. This is not a secure way to configure devices.
OSPF MD5 authentication (Type-2) is more secure than simple text authentication. This approach computes a hash value from the contents of an OSPF packet and a password using the MD5 algorithm (or key). This hash value is delivered alongside a key ID and a non-decreasing sequence number in the packet.
How to configure OSPF authentication in a Cisco router?
There are two ways to configure authentication.
Step-1
You can enable OSPF authentication area-wide by using the below commands. Then, as mentioned in Step 2, you must configure a clear-text password OR message digest key under an OSPF-enabled interface.
router OSPF 1
area 1 authentication –> enables type 1 clear-text password authentication.
area 2 authentication message-digest –> enables type 2 or md5 authentication
Step-2
Next, you have to enable OSPF authentication on a per-interface basis.
For Type-1 – Simple Authentication
Interface Gig0/1
ip ospf authentication –> enables type 1 authentication
ip ospf authentication-key password –> Make sure the password/key should match between two neighbors.
For Type-2 – Md5 Authentication
Interface Gig0/1
ip ospf authentication message-digest –> enables type 2 or md5 authentication on an interface
ip ospf message-digest-key 1 md5 password –> Key should always match between neighbors.
How to check OSPF authentication?
You can use the following command to check OSPF authentication on Cisco devices.
- Show ip OSPF interface Gig0/1 –> Check if OSPF authentication is enabled on an interface.
- Show ip OSPF | inc Area –> Check if authentication is configured for the entire OSPF area.
OSPF Authentication Troubleshooting
OSPF authentication troubleshooting can be tricky, but you can follow the below approach to make it easier.
| What to Check | Commands To use |
|---|---|
| Do all routers in a certain OSPF area have authentication configured? | show ip ospf | i Area |
| The authentication types (Type 0, 1, 2) between OSPF neighbors must match. | show ip ospf int {int} | i auth | line |
| Do the passwords for neighboring interfaces match when using clear-text authentication? | show run | i auth . *key |
| Do the MD5 authentication digest keys match between two neighboring interfaces? | show run | i digest-key |
| Do all the virtual links have authentication set up? Note: If authentication is set up for Area 0, then authentication is also needed for virtual links. | show run | i virtual-link |
| Use the debug OSPF adjacency command to find out why authentication failed. | debug ip ospf adj |
Conclusion
As we’ve seen, OSPF authentication is well worth the effort that goes into configuring it. Not only does it mitigate a number of well-known security threats, but it’s also easy to set up and simple to troubleshoot. Unfortunately, the networking world has been suffering from a lack of security for too long; with OSPF authentication, you can do your part to reverse this trend.
FAQs:
Which two authentication types does OSPF support?
OSPF supports two types of authentication: –
Type 1 – Clear-text passwords
Type 2 – MD5 cryptographic checksums
How to debug ospf authentication?
Use “debug ip ospf adj” to debug ospf packets and see the reasons for the authentication failure.
What is ospf authentication-key?
The OSPF authentication key is the actual password, whether you are using clear-text (Type-1) or message-digest (Type-2). It must be the same between two neighboring OSPF interfaces to form an OSPF adjacency.
On the other hand, authentication key-ids are locally significant to an interface, used only with MD5 authentication, and therefore may differ on a per-interface basis.
What is OSPF Authentication – Type 2 or MD5 authentication?
Type 2 or MD5 authentication is a type of OSPF authentication that uses an MD5 hashing algorithm to authenticate packets to form OSPF neighborship. It is more secure than clear text (Type 1).
Packets that are not correctly authenticated are dropped. To use OSPF authentication, you must set up two neighbors connected through an interface to use the same authentication method and MD5 key.
- Telecom Network Infrastructure: Complete Guide to Components & Design - January 6, 2026
- TP-Link TL-SG108E vs Netgear GS308E: Budget Smart Switches - January 5, 2026
- MikroTik CRS305-1G-4S+ Review: The Ultimate Budget SFP+ Switch Guide - December 25, 2025