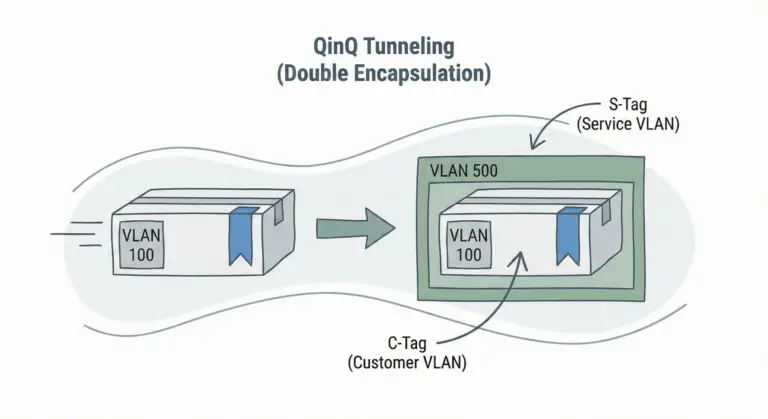
Bridging LAN Over WAN
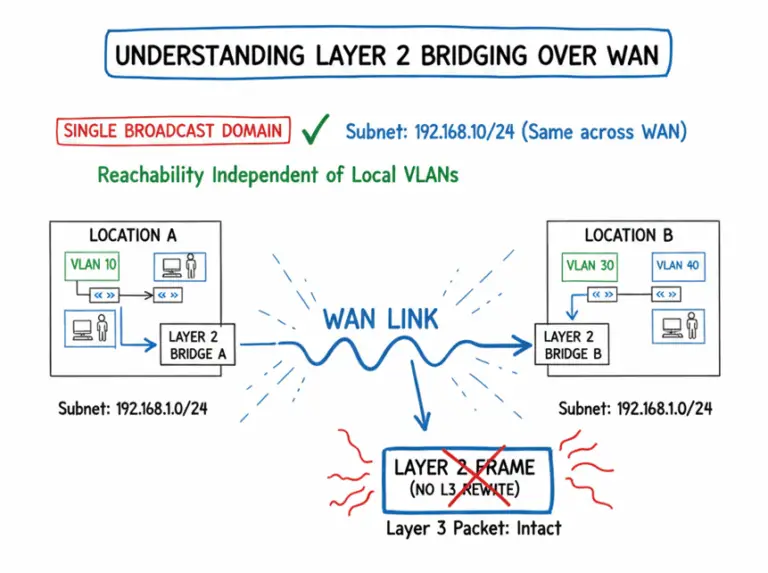
⚠️ Legacy Technology Notice: This article covers legacy Cisco transparent bridging with IRB using deprecated bridge-group commands from classic IOS. These commands do not work on modern IOS-XE or IOS-XR platforms. This content is preserved for historical reference and exam…