Dot1x Authentication
————————–
Recently i have configured the Dot1x authentication in my network,
thought of posting on my blog.
It is a cool feature,with Dot1x authentication we can provide added security
at the access layer switches of the network,it uses username and password based
authentication,it takes the username and password list either from Radius server
or TACACs server.
First we need to issue the global command “aaa new-model” to enable AAA and it
is essential to enable Dot1x authentication.
Next we need to issue “aaa authentication login default none” here the”default”
group enables the aaa process for all interfaces and lines of the device.
Next we need to tell the router to use radius server username and password list
for Dot1x authentication,we can do this simply by issuing “aaa authentication dot1x
default group [radius|tacacs+]” command.
To define the radius-server or tacacs server parameters like host,key or anything
we can simply go into the radius-server or tacacs server in global configuration
mode,you can see the available commands by :-
SWITCH#[radius-server|tacacs-server] ?
Additionally,to force the router/switch to generate radius or tacacs packets from
a single interface instead of relying on the outgoing interface of routing table,
we can issue the command:-
SWITCH#ip [tacacs|radius] source-interface [name of the interface]
Now for the Dot1x part we need to enable this feature by issuing “dot1x system
auth-control” in global configuration mode(prior to 12.4(14)EA1 IOS release this
command was not required).
Next the Dot1x feature must be enabled on a per interface basis by the interface
level command:-
SWITCH(conf-if)#dot1x port-control [mode]
Here mode is of three types,Auto,Forced-authorized,or Forced-unauthorized.
Auto means Dot1x is enabled for username and password authentication
Forced-authorized is the default mode and indicates that authorization is not
required.
Forced-unauthorized dictates that client can never access the network through
this port.
NOTE:-In some switch IOS versions like here i am using Version 12.2(55)SE,here
in interface configuration mode although the command”dot1x port-control auto” is
taken by the switch however it is showing me as “authentication port-control auto”
so better to use “authentication port-control [mode]” to define aur different
dot1x port-control modes,i think Cisco is decaying this command.
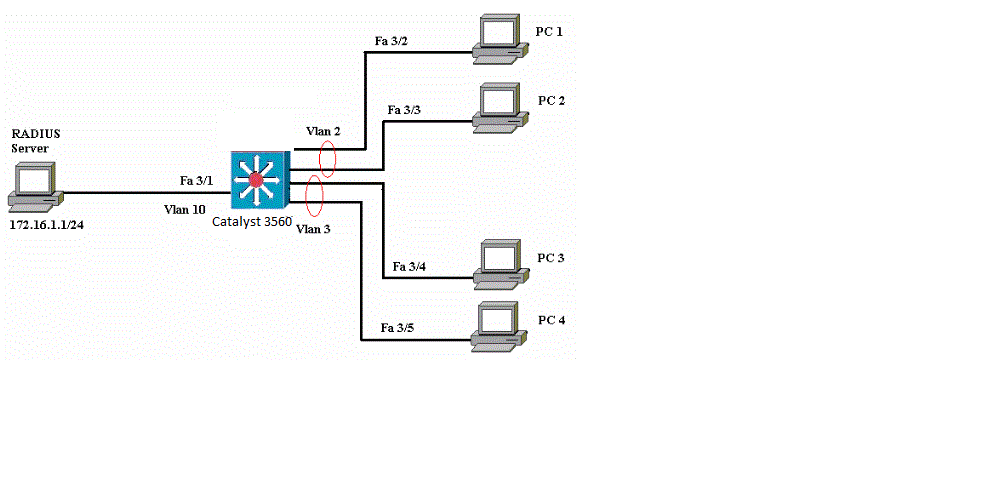
Also we need to issue the “switchport mode access” followed by the “switchport
access vlan [vlan number]” like here in the figure we are configuring Dot1x
authentication for the clients in Vlan2 and Vlan3.
At last we can check our configuration with the commands:-
SWITCH#show dot1x all
SWITCH#show aaa servers