Quick Answer: 👉 Use IKEv2. Period.
IKEv1 was formally deprecated, and its core RFCs were moved to Historic status in April 2023 (RFC 9395). If you’re still using it, you’re running on borrowed time ⏳.
Internet Key Exchange (IKE) negotiates IPsec Security Associations (SAs) between endpoints (hosts or security gateways) for networks that require a secure channel.
- IKEv1 was specified in November 1998 (RFC 2409), alongside RFC 2407 and RFC 2408.
- IKEv2 was first published in December 2005 (RFC 4306), updated in 2010 (RFC 5996), and advanced to Internet Standard (STD 79) in October 2014 (RFC 7296).
IKEv2 is the current standard for key exchange in IPsec and provides:
- Clearer negotiation
- Stronger defaults
- Better reliability and resilience
For older configuration examples, see IKEv1 — but don’t deploy it.
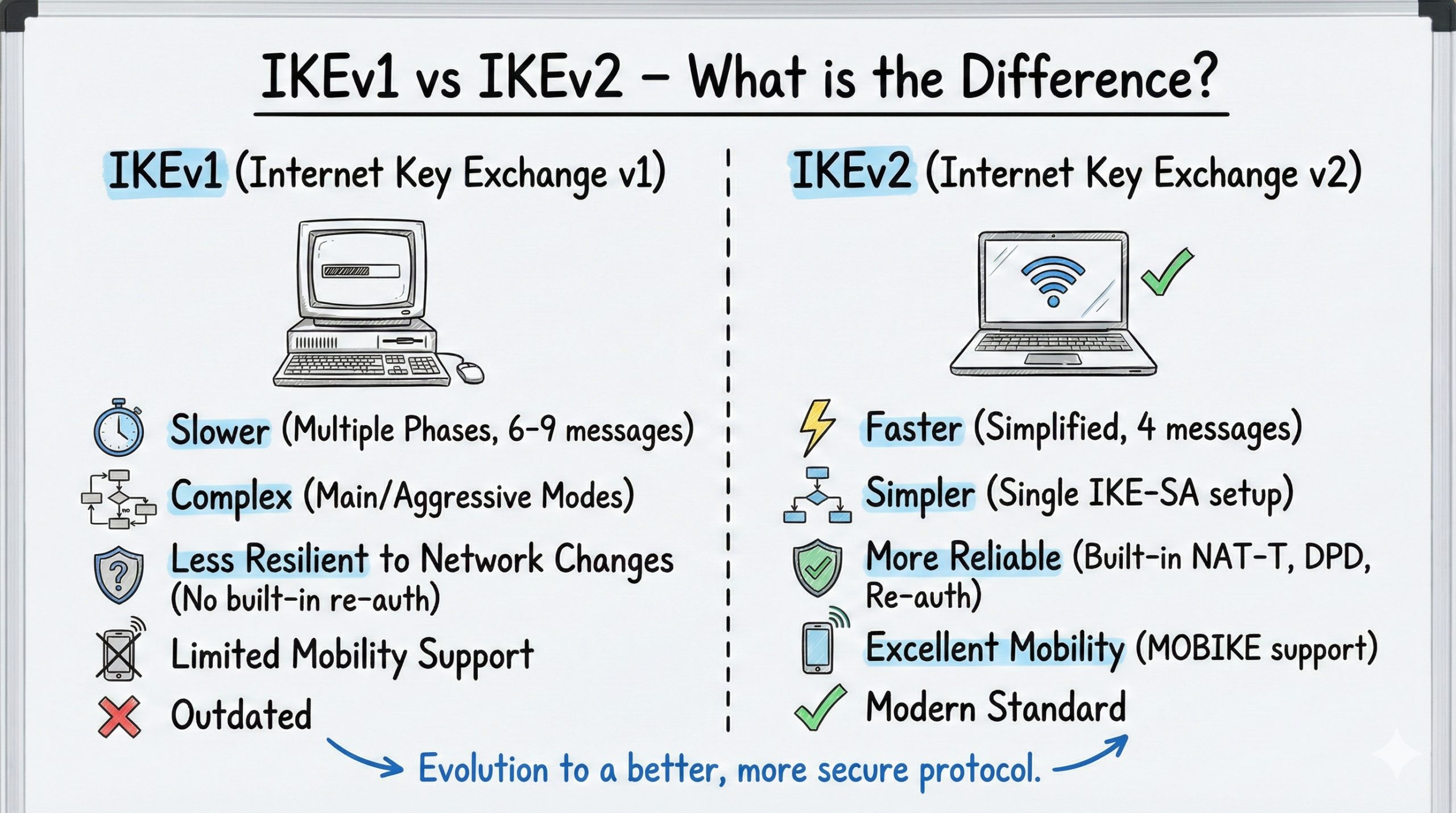
Key differences between IKEv1 vs IKEv2
IKEv1 vs IKEv2 — Detailed Comparison
| Category | IKEv1 | IKEv2 |
|---|---|---|
| Standards status | Deprecated; RFCs 2407/2408/2409 moved to Historic (RFC 9395, 2023) | Current Internet Standard STD 79 (RFC 7296) |
| Initial handshake | Two phases + Quick Mode; 6–9 messages | Two exchanges (IKE_SA_INIT + IKE_AUTH); 4 messages total |
| Complexity | Complex, many modes (Main, Aggressive, Quick) | Cleaner, fewer states, easier to debug |
| Aggressive Mode | Yes (3‑message handshake) | Removed |
| PSK security | Vulnerable to offline dictionary attacks (Aggressive Mode); Main Mode PSK vulnerable (CVE‑2018‑5389) | No equivalent attacks; negotiation hardened |
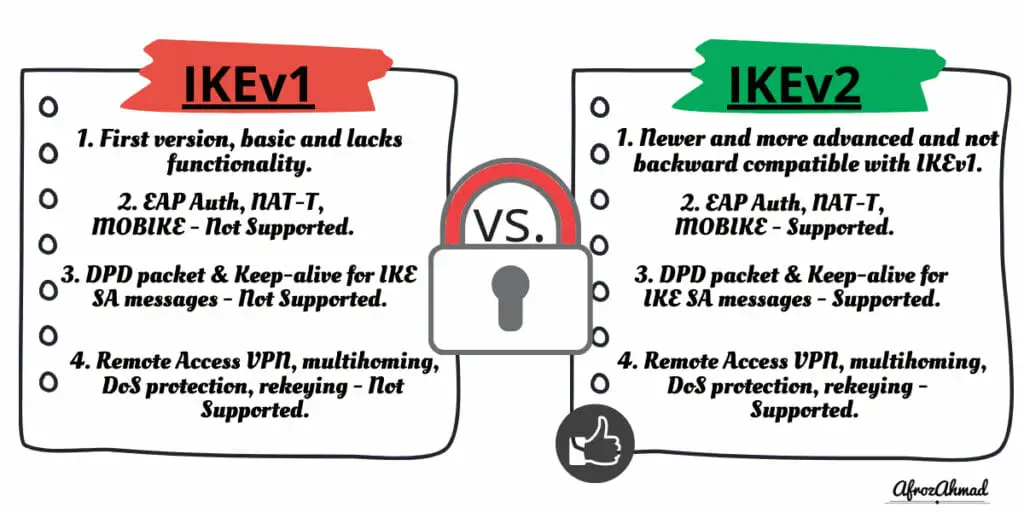
| Authentication | PSK, certificates, XAUTH (extension) | PSK, certificates, native EAP support |
| NAT traversal | NAT‑T via extensions | NAT detection and UDP encapsulation built‑in |
| Mobility / roaming | Not supported | MOBIKE (RFC 4555) for IP changes |
| Rekeying / child SAs | Quick Mode; more round trips | CREATE_CHILD_SA; fewer messages |
| DoS protection | Limited | Cookies + fewer round trips |
| Algorithm guidance | Outdated; weak ciphers seen in legacy configs | Modern guidance (RFC 8247, RFC 8221) |
| Preferred crypto | Often legacy AES‑CBC / SHA‑1 | AEAD (AES‑GCM), SHA‑2, modern DH/ECDH |
| Perfect Forward Secrecy | Optional, inconsistently deployed | Expected and well‑defined |
| Post‑quantum protection | None | PPK support (RFC 8784, RFC 9867) |
| Use today? | ❌ No — deprecated and risky | ✅ Yes — recommended for all deployments |
Migration Checklist (IKEv1 → IKEv2)
1️⃣ Inventory tunnels and authentication methods (PSK vs. certificates).
2️⃣ Align crypto with current guidance (AEAD + SHA‑2; modern DH/ECDH groups).
3️⃣ Enable IKEv2 profiles and policies; test EAP for remote access users.
4️⃣ Plan NAT‑T and MOBIKE behavior for roaming devices and multihomed sites.
5️⃣ Perform staged cutovers, monitor rekeying and DPD, then disable IKEv1.
6️⃣ Optionally deploy PPKs for post‑quantum protection where policy requires it.
Conclusion
Both IKEv1 and IKEv2 can establish IPsec VPNs, but today the choice is obvious.
- IKEv1 is deprecated; its core RFCs (2407/2408/2409) were moved to Historic status in 2023.
- Its design carries real security risks, especially when using pre‑shared keys:
- Aggressive Mode enables offline dictionary attacks
- Main Mode with PSK is vulnerable (CVE‑2018‑5389)
IKEv2, now the official Internet Standard (STD 79 / RFC 7296), fixes these problems with:
- A cleaner handshake
- Integrated NAT traversal
- Optional mobility via MOBIKE
- Stronger defaults and clearer crypto guidance
- Optional post‑quantum hardening via PPKs
For new deployments and migrations, the answer is simple: ✅ Use IKEv2
✅ Use modern cipher suites with PFS
✅ Consider post‑quantum protection where it makes sense
If this comparison helped, feel free to share it with teammates who are planning an IPsec upgrade or finally saying goodbye to IKEv1 👋🔐
- Telecom Network Infrastructure: Complete Guide to Components & Design - January 6, 2026
- TP-Link TL-SG108E vs Netgear GS308E: Budget Smart Switches - January 5, 2026
- MikroTik CRS305-1G-4S+ Review: The Ultimate Budget SFP+ Switch Guide - December 25, 2025