In the world of home router security, MAC address filtering is a technique that can add an extra layer of protection to your network. By controlling which devices can connect to your WiFi based on their unique MAC address, you can potentially prevent unauthorized access and improve your overall wireless security. However, MAC address filtering also has its limitations and drawbacks that every network administrator should be aware of.
In this article, we’ll explore MAC address filtering, how to set it up on your home router, and when it’s most effective as part of a comprehensive network security strategy.
Key Takeaways
- MAC address filtering allows you to control which devices can connect to your home network based on their unique MAC addresses.
- It can provide an additional layer of security alongside WiFi encryption, but it has limitations and should not be relied upon alone.
- MAC addresses can be spoofed by determined attackers, bypassing the filter.
- Setting up MAC filtering involves accessing your router‘s settings and adding devices to an allowed or blocked list.
- MAC filtering can be useful for parental controls, guest access, and blocking suspicious devices, but it can also introduce management overhead and potential connectivity issues.
- For the best home network security, use MAC filtering in combination with other measures like strong WiFi encryption, firewalls, network segmentation, and monitoring tools.
What is MAC Address Filtering?
Before we explore MAC address filtering, let’s first understand what a MAC address is. MAC stands for Media Access Control, and it’s a unique identifier assigned to every network interface card (NIC) in a device. This includes the WiFi and Ethernet cards in your computers, smartphones, tablets, and smart home devices. MAC addresses are typically represented as a string of 12 hexadecimal characters, like “00:11:22:33:44:55”.
MAC address filtering is a network access control technique that allows or blocks devices from connecting to a network based on their MAC addresses. Routers can be configured to maintain a list of permitted or blocked MAC addresses, which is checked each time a device attempts to connect. There are two main approaches to MAC filtering:
- Whitelisting: Only devices with MAC addresses on the allowed list can connect to the network. All other devices are blocked by default.
- Blacklisting: Devices with MAC addresses on the blocked list are specifically denied access to the network. All other devices are allowed by default.
MAC address filtering works similarly to access control lists (ACLs) used in corporate firewalls and other network security devices. However, it’s important to note that MAC filtering only controls access to the local WiFi or Ethernet network, not the wider internet.
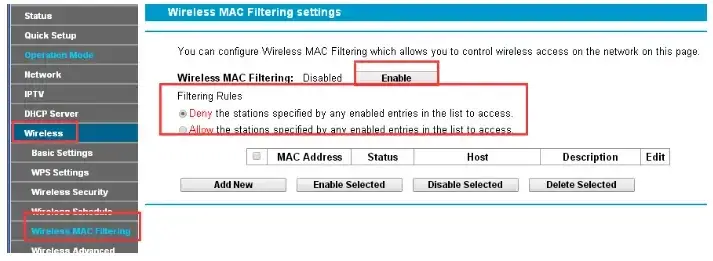
Setting Up MAC Address Filtering on Home Routers
Now that you understand what MAC address filtering is, let’s walk through the process of setting it up on your home router. The exact steps may vary depending on your router brand and model, but the general process is similar across most routers.
- Access your router‘s settings by entering its IP address into a web browser. This is typically something like “192.168.1.1” or “10.0.0.1”. Check your router‘s manual or the label on the device for the exact address.
- Log in to the router using your administrator username and password. If you haven’t changed these from the defaults, they may be something like “admin” and “password”, or they might be printed on the router itself.
- Look for a section labeled “MAC Filtering“, “MAC Address Filtering“, “Access Control“, or similar. This is often found under the “Wireless” or “Security” menus.
- Choose whether you want to use whitelisting or blacklisting mode. Some routers may have separate lists for allowed and blocked devices.
- To allow or block a device, you’ll need to enter its MAC address into the appropriate list. You can usually find a device’s MAC address in its network settings, or you may see a list of currently connected devices in your router‘s interface.
- Save your changes and reboot the router if prompted. The new MAC filtering rules should now be active.
Keep in mind that if you’re using whitelisting mode and you block a device that was previously connected, it will immediately lose its connection to the router. Make sure you have an alternate way to access the router settings (like a wired connection) in case you accidentally block your own device.
Potential Benefits of MAC Address Filtering
When properly configured, MAC address filtering can offer several benefits for your home network security:
- Additional layer of security: MAC filtering can work alongside your WiFi encryption (WPA2 or WPA3) to provide an extra barrier against unauthorized access. Even if someone guesses your WiFi password, they still won’t be able to connect unless their device’s MAC address is on the allowed list.
- Parental controls: By blocking the MAC addresses of your children’s devices, you can control when and how they connect to the network. For example, you could block their gaming console during homework hours.
- Guest access: If you have frequent visitors who need WiFi access, you can set up a separate guest network with MAC filtering enabled. This allows you to grant temporary access to specific devices without giving them full access to your primary network.
- Blocking suspicious devices: If you notice an unknown device on your network, you can block its MAC address to prevent potential hacking attempts or malware infections.
Limitations and Drawbacks of MAC Address Filtering
Despite its potential benefits, MAC address filtering also has several significant limitations and drawbacks that you should be aware of:
- MAC spoofing: One of the biggest weaknesses of MAC filtering is that MAC addresses can be easily spoofed by determined attackers. Using readily available tools, a hacker could change their device’s MAC address to match one on your allowed list, bypassing the filter entirely.
- Local network only: MAC filtering only controls access to your local WiFi or Ethernet network, not the wider internet. Once a device is connected, MAC filtering does nothing to prevent malware, data breaches, or other online threats.
- Management overhead: Maintaining an accurate list of allowed or blocked MAC addresses can be time-consuming, especially if you have many devices on your network. Every time you get a new device, you’ll need to add its MAC address to the list.
- Connectivity issues: Some devices, particularly smartphones and tablets, use randomized MAC addresses for privacy reasons. This can cause them to be blocked by MAC filtering even if they were previously allowed. Additionally, if a device’s MAC address is spoofed by malware, it may be blocked and unable to connect.
- False sense of security: Perhaps the biggest risk of MAC filtering is that it can give network administrators a false sense of security. While it can be a useful tool as part of a layered security approach, it’s far from foolproof and should never be relied upon as the sole means of network access control.
Alternatives and Complementary Security Measures
Given the limitations of MAC address filtering, it’s important to consider alternative and complementary security measures for your home network:
- Strong WiFi encryption: WPA2 or WPA3 encryption should be the foundation of your wireless security. Make sure to use a strong, unique password and change it regularly.
- Guest networks: Set up a separate guest WiFi network for visitors and untrusted devices. This keeps them isolated from your primary network and your sensitive data.
- Firewall rules: Most home routers include a basic firewall that can be configured to block incoming traffic from specific IP addresses or ports. This can help prevent unauthorized access attempts from the internet.
- Network segmentation: If you have IoT devices or other potentially vulnerable devices on your network, consider using VLANs (virtual LANs) to isolate them from your main devices. Many newer routers support this feature.
- Monitoring tools: Use network monitoring tools to keep an eye on connected devices and traffic patterns. This can help you spot suspicious activity early and take action to prevent data breaches.
- Physical security: Don’t forget about physical security for your router and other network devices. Keep them in a secure location and limit physical access to prevent tampering or unauthorized configuration changes.
See also:
- USB Ports on Home Router
- Dynamic DNS or DDNS on Home Routers
- Port Forwarding on Home Routers
- Mastering QoS Settings on Home Router
Conclusion
MAC address filtering can be a useful tool for improving the security of your home network, but it’s important to understand its limitations and use it as part of a comprehensive security strategy. By combining MAC filtering with strong WiFi encryption, guest networks, firewall rules, and other measures, you can create a layered defense that helps protect your devices and data from unauthorized access and malware.
However, it’s crucial not to rely solely on MAC filtering or to assume that it makes your network invulnerable. Hackers and malware can still find ways to bypass MAC filters, and even legitimate devices can sometimes be blocked inadvertently.
Ultimately, the decision to use MAC address filtering on your home router will depend on your specific network setup, security needs, and level of technical expertise. If you do choose to implement it, be sure to follow best practices for router configuration and to regularly review and update your allowed/blocked lists as your devices change over time.
FAQs
Q: Will MAC address filtering slow down my network?
A: In most cases, no. MAC filtering happens at the router level and has minimal impact on network performance. However, if you have a very large number of devices and complex filtering rules, it could potentially introduce some latency.
Q: Can I use MAC filtering instead of a WiFi password?
A: While you could theoretically use MAC filtering as your only means of access control, it’s not recommended. WiFi encryption is a much stronger and more reliable security measure. MAC filtering should be used in addition to, not instead of, WPA2 or WPA3 encryption.
Q: What happens if I accidentally block my own device with MAC filtering?
A: If you’re using whitelisting mode and you block a device that was previously allowed, it will immediately lose its connection to the router. To regain access, you’ll need to connect to the router using an alternate method (like an Ethernet cable) and update the MAC filter list.
Q: Can my Internet Service Provider (ISP) help me set up MAC filtering?
A: Most ISPs provide basic support for the routers they supply to customers. However, the level of support for advanced features like MAC filtering can vary. It’s best to check your ISP‘s support website or contact their customer service directly for guidance on your specific router model.




