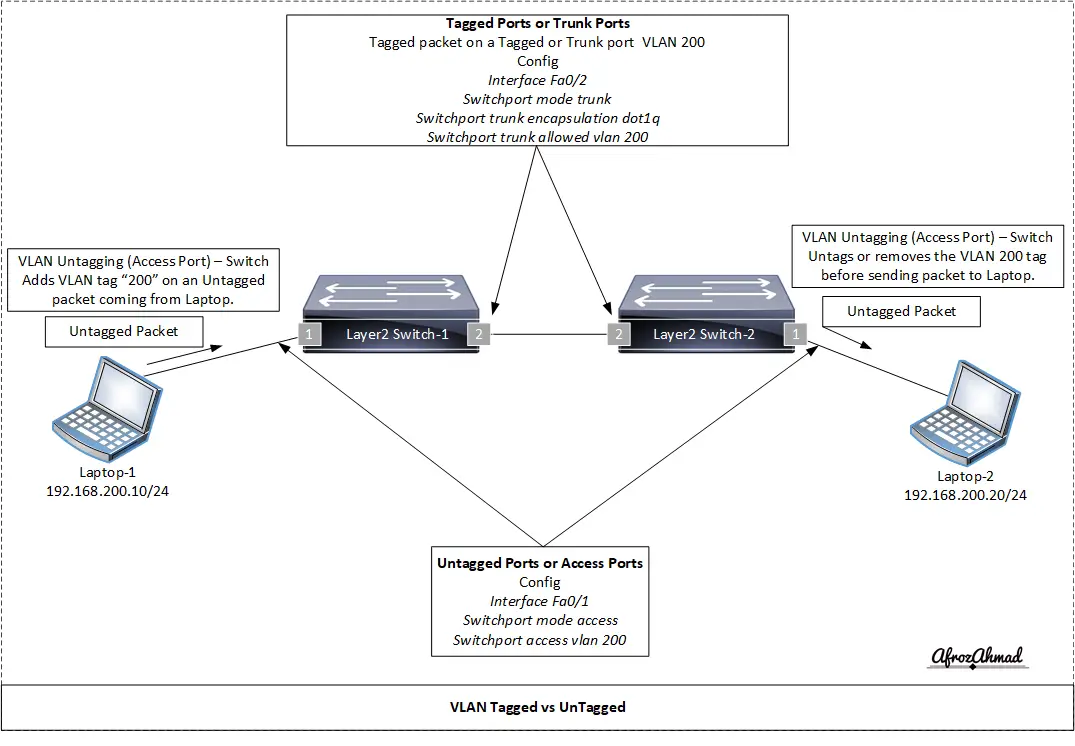
VLAN-tagged ports are configured to carry multiple VLANs, while VLAN untagged ports (access ports) carry traffic for a single VLAN on a switch. Let’s get into more details and the best practices that matter in production networks.
VLAN tagged vs Untagged Comparison
| Technology Area | VLAN Tagged | VLAN Untagged |
|---|---|---|
| Definition | A switch port that carries traffic for one VLAN is known as an Access port by Cisco and an Untagged port by other vendors. | A switch port that carries multiple VLANs is a Trunk port by Cisco and a Tagged port by other vendors. |
| VLAN Quantity can be configured on a single port | A VLAN tagged port can be configured to carry multiple VLANs simultaneously. | A VLAN Untagged port can carry One Data VLAN and one Voice VLAN at maximum. |
| Frame Type | Frame with a VLAN tag. | Frame without a VLAN tag. |
| Cisco Terminology | Trunk Port | Access Port |
| Cisco Configuration Example | interface Fast Ethernet 0/3 switchport mode trunk switchport trunk encapsulation dot1q switchport trunk allowed vlan 100,200,300 | interface Fast Ethernet 0/1 switchport mode access switchport access vlan 100 switchport voice vlan 300 |
| Ingress Rule for packet | Only tagged packets can pass; other or untagged packets will be dropped. An Untagged packet can be marked if switchport is configured to tag the untagged packet by "switchport access vlan 100" command on cisco switches. | The switch must be configured with VLAN Tag to mark the Untagged packet coming from the end device. |
| Egress Rule for Packet | The packets will be passed unchanged. | Switch strips the VLAN before sending it to the end device. |
Let’s briefly discuss VLANs and the 802.1Q tag, then dive into the difference between VLAN tagged vs. untagged (access vs. trunk).
VLANs:- Virtual LANs, or Virtual Local Area Networks, work at the Data Link layer of the OSI model. VLANs help create virtual separations within a switch that provide distinct logical LANs or segregated broadcast domains that each behave as if they were configured on a separate physical switch.
Before the invention of VLANs, a switch used to serve a single LAN and maintained a single broadcast domain, which meant broadcast packets were sent to all ports.
802.1Q VLAN tags enable a single switch to serve multiple LANs by dividing a single broadcast domain into multiple broadcast domains.
Learn how to manage VLANs centrally through VTP.
What is a VLAN tag, and why do we need a VLAN tag in the network?
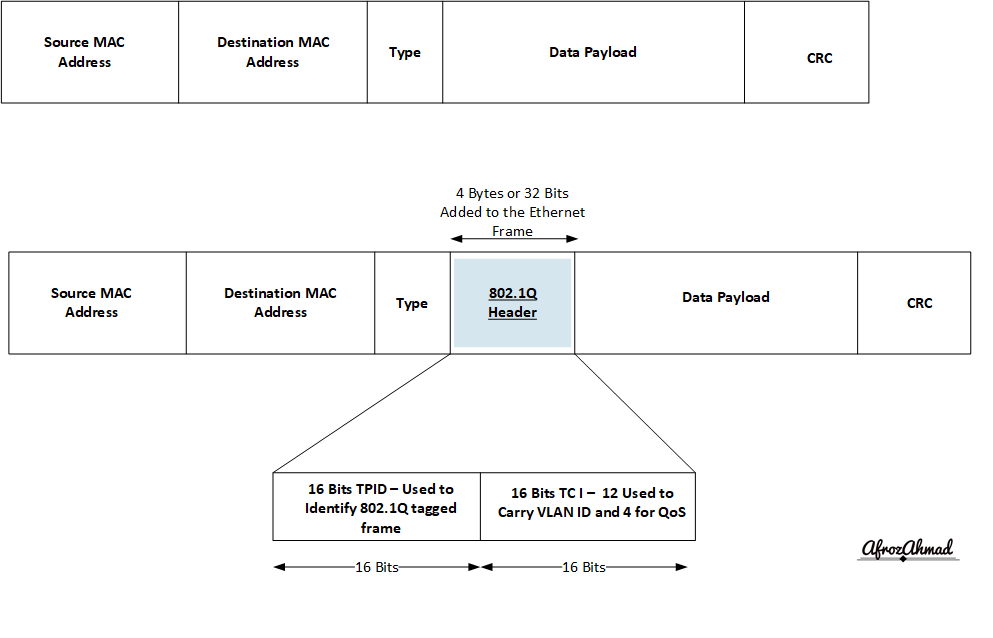
- VLAN tags are a core part of VLANs. To support VLANs on Ethernet, frames are tagged using IEEE 802.1Q.
- IEEE 802.1Q (current base revision 802.1Q-2022) is the widely used standard for VLAN tagging on switches.
- 802.1Q inserts a 4-byte tag: a Tag Protocol Identifier (TPID, 16 bits, value 0x8100) and a Tag Control Information (TCI, 16 bits).
- TCI is split into Priority Code Point (PCP, 3 bits) for 802.1p QoS priority, Drop Eligible Indicator (DEI, 1 bit) for drop preference, and VLAN ID (VID, 12 bits).
- The VLAN ID is 12 bits long so a switch can handle 4096 values. Normal VLAN IDs are 1–4094. VLAN 0 indicates a priority‑tagged frame (PCP only) and VLAN 4095 is reserved.
Let us look further into untagged ports (access), tagged ports (trunk), and the default and native VLAN concepts.
What is VLAN untagging, and what does Untagged packet mean?
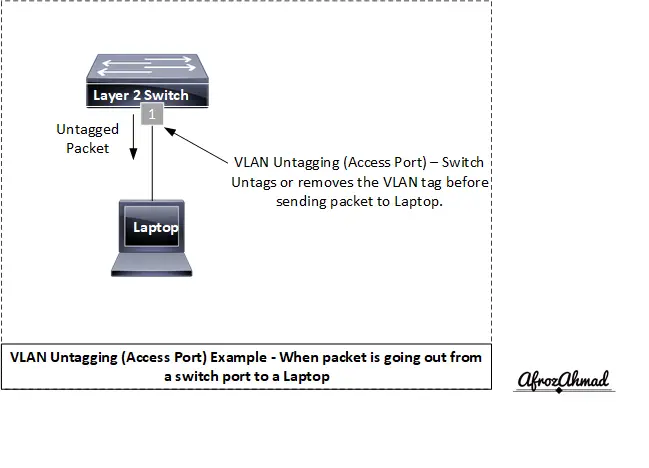
Ports on switches normally connect to end devices that do not understand VLAN tags, so the switch performs VLAN untagging before forwarding frames from the switch to the end device. The switch strips the VLAN tag from the frame before sending it out the access port.

When a frame comes from an end device to the switchport, it is untagged. “Untagged” traffic means the connected host does not include an 802.1Q header; the switch classifies the frame into the port’s configured access VLAN.
Frames do not have 802.1Q tags when they arrive on an access port. The switch associates the frame with the access VLAN (for example, VLAN 200), applies the tag internally as needed, and forwards it across the network.
In Cisco terms, the port is called an access port, and this VLAN is called the access VLAN.
In short: a switchport that carries traffic for one VLAN is known as an access port by Cisco and an untagged port by many other vendors.
What is VLAN tagging?
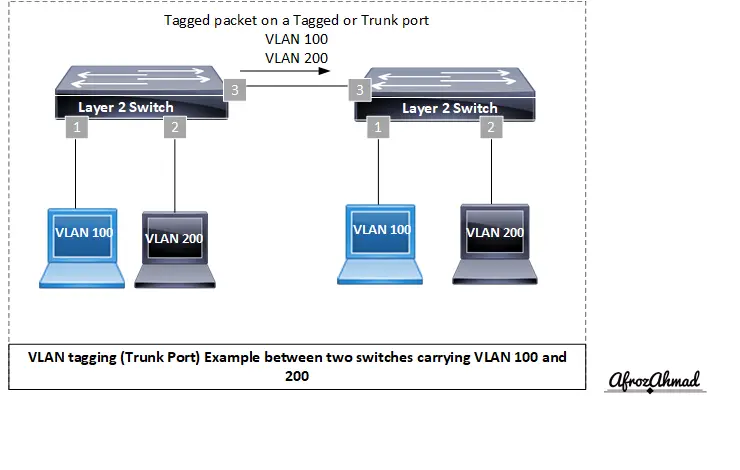
VLAN tagging refers to understanding 802.1Q tag information and carrying multiple VLANs on a single switchport.
When an interface expects frames with VLAN tags, it is referred to as a tagged port or a trunk port in Cisco terminology. Tagged (trunk) ports connect two switches or a switch and another network device to pass multiple VLANs on a single port. By default, trunks allow all VLANs; in practice, you should allow only the VLANs that are needed.
In short: a switchport that carries multiple VLANs is known as a trunk port by Cisco and a tagged port by other vendors.
So to summarize VLAN tagging vs. untagging, the terms “access port” and “trunk port” are frequently used in the context of Cisco networks. VLANs are an open standard, so other vendors implement the same concepts and often call them untagged (access) and tagged (trunk) ports.
What is a Native VLAN?
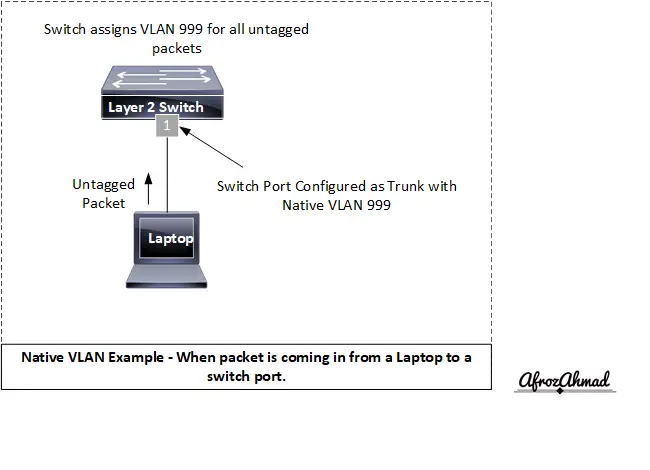
A native VLAN is used to identify or mark all untagged packets on a tagged or a trunk port.
Native VLANs are generally the same as the switch’s default VLAN, e.g., VLAN 1, unless you change it to something else (e.g., 999). For security and consistency, avoid using VLAN 1 for user/data traffic; move access ports to a non‑default VLAN, set a non‑1 native VLAN on trunks or enable global native VLAN tagging (for example, vlan dot1q tag native on Cisco platforms), and place unused ports into a dedicated “black‑hole” VLAN and shut them down.
What is Default VLAN?
Most switches that support VLANs come with a default VLAN. Therefore, all ports on that switch belong to the default VLAN by default until you configure otherwise.
Devices connected to the default VLAN on switch ports can access one another without configuration, which can increase risk inside the network. Do not use VLAN 1 for user/data traffic. Instead, change access ports to a different VLAN as per your policies, assign a non‑1 native VLAN (or tag the native), and prune trunks to only the VLANs required.
For example: many Cisco switches come with VLAN 1 as the default VLAN on all ports.
VLAN Tagging and Untagging Example and Traffic Flow
Let’s take a scenario when Laptop‑1 tries to ping Laptop‑2. Both laptops are part of VLAN 200, so communication will work without using any Layer 3 device.
Laptop‑1 and Laptop‑2 are part of VLAN 200 and subnet 192.168.200.0/24 and their IP addresses are 192.168.200.10/24 and 192.168.200.20/24 respectively.
Both switches have populated their MAC address tables with all laptops/devices MAC addresses and their corresponding connected ports.
I have used a pair of Layer 2 switches to demonstrate the VLAN Tagged vs Untagged concept. You can use any switch vendor of your choice, and the idea remains the same.
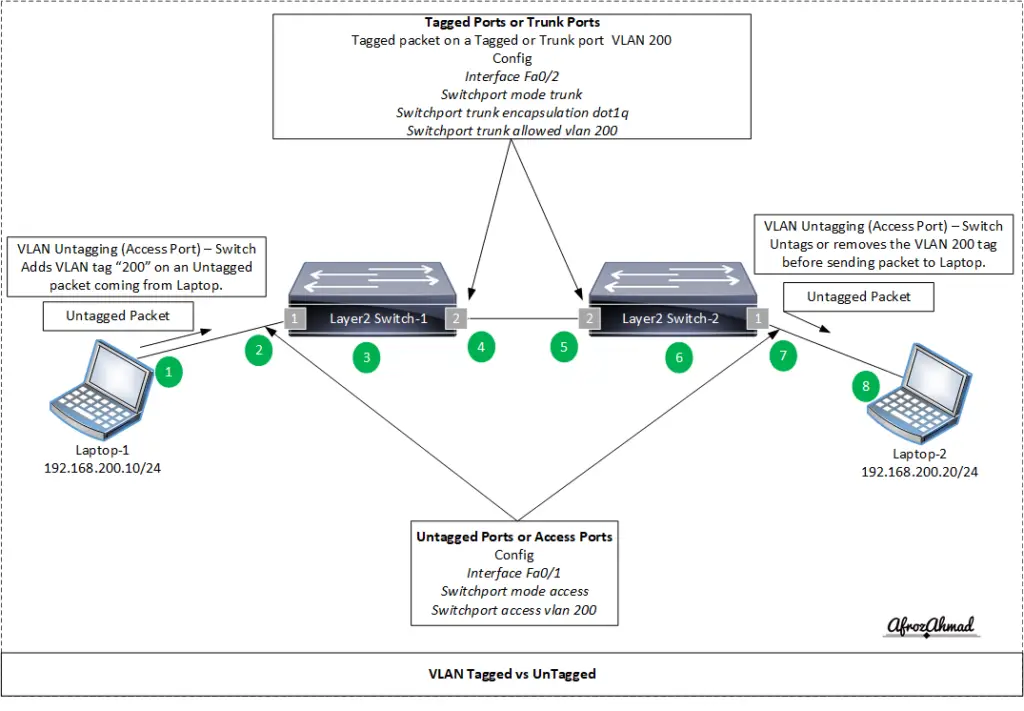
Ports 1 on both switches (Layer 2 switch‑1, Layer 2 switch‑2) are untagged (access) ports.
Sample config
- interface Gi1/0/1
- switchport mode access
- switchport access vlan 200
Ports 2 on both switches (Layer 2 switch‑1, Layer 2 switch‑2) are tagged (trunk) ports. By default, a trunk allows all VLANs; restrict the trunk to only the VLANs that must traverse it and avoid carrying VLAN 1 unless required by specific control protocols.
Sample config
- interface Gi1/0/2
- switchport mode trunk
- switchport trunk allowed vlan 200
- switchport nonegotiate
- Laptop‑1 forwards an untagged frame to Layer 2 switch‑1 port 1.
- Layer 2 switch‑1 port 1 classifies the frame into VLAN 200 (the access VLAN) and applies the VLAN tag internally.
- Layer 2 switch‑1 looks up the destination MAC in its MAC address table. It finds the entry and forwards the frame to port 2.
- Layer 2 switch‑1 port 2 checks the VLAN tag and, because VLAN 200 is allowed on the trunk, forwards the tagged frame to Layer 2 switch‑2 port 2.
- Layer 2 switch‑2 port 2 repeats the process for its MAC address table.
- Layer 2 switch‑2 forwards the frame to port 1.
- Layer 2 switch‑2 port 1 removes the VLAN 200 tag (untags) and sends the frame to Laptop‑2.
- Laptop‑2 receives an untagged frame and replies accordingly.
The result of the above process is that ping works from Laptop‑1 to Laptop‑2.
Acronyms Used in the Blog
- LAN: Local Area Network
- VLAN: Virtual Local Area Network
- DTP: Dynamic Trunking Protocol (disable on access ports; on static trunks use
switchport nonegotiate)
Conclusion
In this post, we started with a basic understanding of VLANs and 802.1Q tags (PCP/DEI/VID), then discussed the difference between VLAN tagged vs. untagged (access vs. trunk). We wrapped up with a simple traffic flow and modern configuration and security best practices you can apply today.
I hope you liked the article, please share for maximum reach.
- Telecom Network Infrastructure: Complete Guide to Components & Design - January 6, 2026
- TP-Link TL-SG108E vs Netgear GS308E: Budget Smart Switches - January 5, 2026
- MikroTik CRS305-1G-4S+ Review: The Ultimate Budget SFP+ Switch Guide - December 25, 2025