- What is Cisco vPC and its brief History
What is Cisco vPC and its brief History
What is Cisco vPC (virtual Port Channel), and how has normal port-channel evolved to this point? Let us understand port-channel first; it is the simplest and oldest technology that combines two or more interfaces. In return, it gives the benefits like load balancing across links, redundancy in case any link goes down, increased bandwidth since you combined two or more links, and a single spanning-tree view of the links. However, these benefits come at the cost of connecting all the links within a bundle to a single device. And if that single device fails, you will lose everything connected to that switch. However, port channels are still common in networks because of their simplicity and vendor-neutral approach.

Then Cisco introduced Cisco Catalyst 6500 in late 1999’s with the MEC (multi-Etherchannel) feature, which offered to combine two links in a bundle going to the two different 6500 switches. And because the end device is cabled to two separate 6500 switches, It provided a better resiliency than a simple port channel. This technology is called Cisco VSS (Virtual Switch System). That was a huge advantage, and almost all enterprises purchased Cisco 6500’s due to this feature alone.
Then in 2008, Cisco introduced the Nexus series switches which also had the link bundling (Multi-Etherchannel) feature similar to Cisco 6500 VSS, and it was called vPC. Finally, Cisco officially launched vPC in 2009. The main difference between VSS and vPC is that VSS creates a logical switch that combines the control and management plane of the two Cisco 6500 chassis. On the other hand, in Cisco vPC, both Cisco Nexus switches have separate control planes and are managed independently. More on this topic later in a separate post.
Please refer to the table to find the difference between Simple port-channel, Cisco VSS, and Cisco vPC technologies.
Simple Port-channel vs Cisco VSS vs Cisco vPC
| Technology Area | Simple Port-Channel | Cisco VSS | Cisco vPC |
|---|---|---|---|
| Redundancy | It can only be connected between two switches or devices. | It can be connected between three devices making a triangle. | It can be connected between three devices making a triangle. |
| Software | It is supported in Cisco Catalyst Operating system. | It is supported in Cisco Catalyst Operating system. | It is supported in Cisco NXOS only. |
| Platform | It is supported on Cisco Catalyst Switches. | It is supported on only Cisco 6500 series Catalyst Switches. | It is supported on Cisco Nexus Series Switches. |
| Control Plane | Separate control plane on single switch. | Single control plane on two 6500 switches. | Two separate control plane , one on each cisco nexus switch. |
| Etherchannel Protocols support | Static, PAgP, PAgP, LACP | Static, PAgP, PAgP, LACP | Static, LACP |
| Configuration | Single Configuration on single Cisco Catalyst switch. | Single Configuration on two Cisco 6500 switches. | Two different configurations on two nexus switches. |
| STP as a failback | Yes | Yes | Yes |
| Loop-free topology | Yes | Yes | Yes |
| Multi-Chassis Port Channel | No | Yes | Yes |
| Maximum Physical Nodes | 1 | 2 | 2 |
| No Disruptive ISSU support | Not required | No | Yes |
| Layer 3 port channel support | Yes | Yes | Limited |
| Heart beat link between devices | Not required. | VSL is used to transfer data and control messages between the active and standby switches. | CFS transmits control messages through Peer Link, and a Peer keep alive link is utilized to monitor heartbeats and detect dual-active states. |
| HSRP required for layer 3 redundancy | HSRP is required. | Not required | HSRP is required. |
| Separate Instance for other protocols | Single instance on single switch. | On each physical switch in the VSS, the same instance of STP, FHRP, IGP, and BGP will be used. | On each physical switch in the VPC, a separate instance of STP, HSRP, VRRP, IGP, and BGP will be required. |
Let’s elaborate on Cisco vPC; it enables a device to view cables/links that are physically connected to two separate Cisco Nexus switches as a single port channel. A switch, server, or any other networking device that supports port channels can be that device. A vPC can provide Layer 2 multipathing, which has great benefits: it increases bisectional bandwidth and redundancy by providing numerous parallel pathways and load balancing between nodes. (the best definition I found online and then simplified to digest it quickly).
Cisco VPC Benefits
The following are the advantages of using Cisco vPC:
- Allows a single device to use a port-channel across two upstream devices.
- vPC Eliminates ports that are blocked by Spanning Tree Protocol (STP).
- Provides a loop-free topology.
- Uses all available uplink bandwidth.
- Provides fast convergence in the case of link failure or device failure.
- Provides link-level resiliency.
- Assures high availability.
Cisco vPC Explained
Cisco vPC has the following components:-
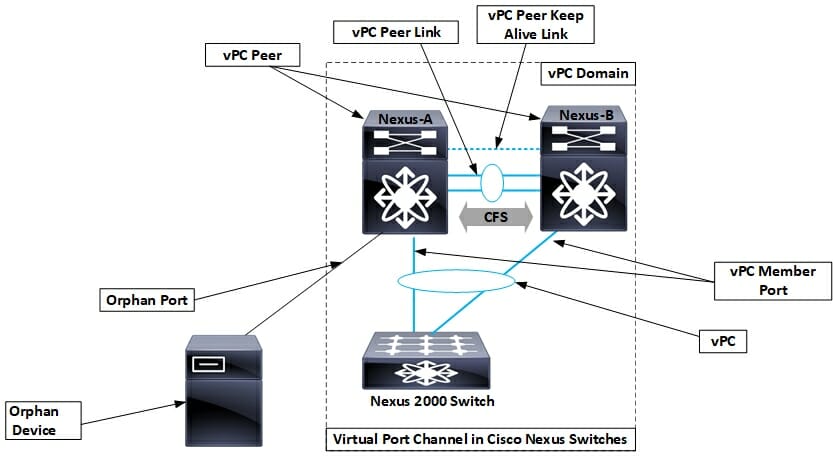
| vPC Terminology | Brief Definition |
|---|---|
| vPC | It is the port-channel that includes vPC peers and the downstream device altogether. A vPC is an L2 port type: switchport mode trunk or switchport mode access. |
| vPC Peer Switch | A vPC switch (one of a Cisco Nexus 7000/9000 Series pair) |
| vPC domain | A Domain contains 2 nexus peer switches. vPC domains are limited to have a maximum of two peer devices each. |
| vPC member Port | One of a set of ports (that is, port-channels) that form a vPC (or port-channel member of a vPC). |
| vPC peer link | vPC Peer-Link is used to synchronize vPC peer state between two vPC peer switches. It must be 10GbE. It is also an L2 trunk carrying vPC VLAN. |
| vPC peer keepalive link | The keepalive link between vPC peer devices is used to monitor their liveness. |
| vPC Vlan | vPC VLAN is carried via the vPC peer-link and is used to communicate with a third device via the vPC. Once a VLAN is defined on a vPC peer-link, it automatically becomes a vPC VLAN. |
| Non vPC Vlan | A VLAN that is not a member of any vPC and is not attached to any vPC peer link. |
| Orphan Port | A port that belongs to a single attached device. vPC VLAN is commonly used on this port. |
| Cisco Fabric Services (CFS) protocol | Underlying protocol running on top of vPC peer-link providing reliable synchronization and consistency check mechanisms between the 2 peer devices. |
Cisco vPC Requirements:-
- vPC technology is supported since NX-OS 4.1.3. NX-OS appropriate version depends on line cards configuration, so it is always advisable to check the detailed hardware guide before deployment.
- vPC feature is included in the base NX-OS software license.
How to Configure Cisco vPC
Configuring vPC is easy; follow the below steps, and you will configure it in no time.
- Enable necessary features
- Create vPC vrf and Define vPC domains
- Establish vPC Peer Keepalive connectivity
- Create a vPC Peer link
- Create vPCs
- Make Sure Configurations are Consistent
Please note: Order does matter.
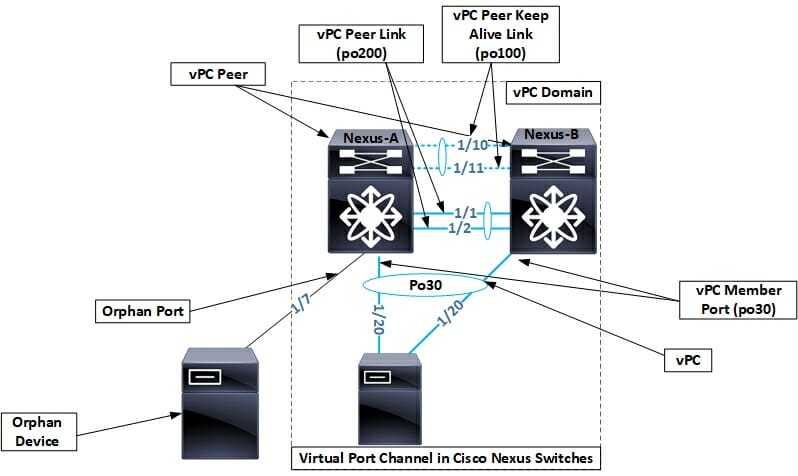
You must enable vPC and LACP features inside nexus switches.
Nexus-A and B
feature vpc
feature lacp
Create vPC vrf
Nexus-A and B
vrf context VPC_PKAL
Define vPC Domains
We will be using vPC domain 1. So you can choose domain id between <1-1000>. Then we will set priorities for both switches; lower priority will become primary.
Nexus-A
vpc domain 1 role priority 8192 peer-keepalive destination 10.1.1.2 source 10.1.1.1 vrf VPC_PKAL
Nexus-B
vpc domain 1 role priority 16384 peer-keepalive destination 10.1.1.1 source 10.1.1.2 vrf VPC_PKAL
Establish vPC Peer Keepalive connectivity ( back to back physical connection is preferred)
Nexus-A & B
interface Ethernet1/10
description vPC Keepalive
no switchport
channel-group 100 mode active
interface Ethernet1/11
description vPC Keepalive
no switchport
channel-group 100 mode active
interface port-channel100 description vPC Keepalive vrf member VPC_PKAL no switchport ip address 10.1.1.[1-2]/30
Create a vPC Peer link
Nexus-A & B
interface Ethernet1/1
description vPC Peerlink
switchport mode trunk
channel-group 200 mode active
interface Ethernet1/2
description vPC Peerlink
switchport mode trunk
channel-group 200 mode active
interface port-channel200
description vPC Peerlink
vpc peer-link
Create vPC Member Ports
The next step is to bundle the downstream vPC member ports with “Channel-group 30” and “vPC 30” commands on both switches. This will accomplish our vPC configuration.
The last step would be to do the port-channel config on the downstream device, a server in our case.
Nexus-A & B
interface Ethernet1/20
channel-group 30
interface po30
vpc 30
Make Sure vPC Configurations are Consistent
Use the below command to check vPC consistency across vPC peer switches.
Nexus-A & B
show vpc consistency-parameters vpc 30
Important Show Commands to verify and Troubleshoot VPC Deployments
Show vpc brief
The first place to check to see an overview and status of vPC setup via the command “show vpc brief”
Nexus-A & B
Nexus-B# show vpc brief Legend: (*) - local vPC is down, forwarding via vPC peer-link vPC domain id : 1 Peer status : peer adjacency formed ok vPC keep-alive status : peer is alive Configuration consistency status : success Per-vlan consistency status : success Type-2 consistency status : success vPC role : secondary Number of vPCs configured : 2 Peer Gateway : Enabled Peer gateway excluded VLANs : - Dual-active excluded VLANs : - Graceful Consistency Check : Enabled Auto-recovery status : Enabled (timeout = 240 seconds) vPC Peer-link status - ---- ------ --------------------------------------------------- id Port Status Active vlans -- ---- ------ -------------------------------------------------- 1 Po200 up 1,2,5,10 vPC status ---------------------------------------------------------------------------- id Port Status Consistency Reason Active vlans ------ ----------- ------ ----------- -------------------------- ----------- 30 Po30 up success success 10
Check if you have any Orphan Ports
The following command is used to determine Orphan ports.
Nexus-A# show vpc orphan-ports
Nexus-A & B
Nexus-A# show vpc orphan-ports Note: --------::Going through port database. Please be patient.::-------- VLAN Orphan Ports ------- ------------------------- 900 Eth1/7
show vpc consistency-parameter
You can use “Show vpc consistency-parameter” to check configuration consistency among two Nexus Switches.
Nexus-A & B
Nexus-A# shpw vpc consistency-parameters vpc 30 Legend: Type 1 : vPC will be suspended in case of mismatch Name Type Local Value Peer Value ------------- ---- ---------------------- ----------------------- Shut Lan 1 No No STP Port Type 1 Edge Trunk Port Edge Trunk Port STP Port Guard 1 None None STP MST Simulate PVST 1 Default Default lag-id 1 [(7f9b, [(7f9b, 0-2-4-ef-be-69, 801b, 0-2-4-ef-be-69, 801b, 0, 0), (8000, 0, 0), (8000, f4-cf-e2-0-1e-76, 2, f4-cf-e2-0-1e-76, 2, 0, 0)] 0, 0)] mode 1 active active Speed 1 10 Gb/s 10 Gb/s Duplex 1 full full Port Mode 1 trunk trunk Native Vlan 1 1 1 MTU 1 1500 1500 Admin port mode 1 vPC card type 1 Empty Empty Allowed VLANs - 2-8,10-4092,4094 2-8,10-4092,4094 Local suspended VLANs - - - Peer-KeepAlive
Show vPC Peer-KeepAlive
Finally, to check the status of the vPC keepalive the command show vpc peer-keepalive is used.
Nexus-A & B
Nexus-B# show vpc peer-keepalive vPC keep-alive status : peer is alive --Peer is alive for : (2900862) seconds, (249) msec --Send status : Success --Last send at : 2021.08.20 03:32:42 418 ms --Sent on interface : Po100 --Receive status : Success --Last receive at : 2021.08.20 03:32:43 645 ms --Received on interface : Po100 --Last update from peer : (0) seconds, (192) msec vPC Keep-alive parameters --Destination : 10.1.1.1 --Keepalive interval : 1000 msec --Keepalive timeout : 5 seconds --Keepalive hold timeout : 3 seconds --Keepalive vrf : VPC_PKAL --Keepalive udp port : 3200 --Keepalive tos : 192
Cisco vPC Show Commands
| Cisco vPC Command | Purpose |
|---|---|
| show feature | Displays whether the vPC is enabled or not. |
| show vpc brief | Displays brief information about the vPCs. |
| show vpc consistency-parameters | Displays the current status of parameters that must be constant/consistent across all vPC interfaces on both vPC peer switches. |
| show running-config vpc | Displays running configuration information for vPCs. |
| show port-channel capacity | Displays how many port channels are configured and how many are still available on the device. |
| show vpc statistics | Displays statistics about the vPCs. |
| show vpc peer-keepalive | Displays information about the peer-keepalive messages. |
| show vpc role | Displays the vPC peer's state including its role, the vPC system MAC address and system priority, and also the MAC address and priority of the local device. |
Cisco vPC best practices
Use the below table as a guideline when configuring vPC.
| vPC Configuration parameters | Best Practice |
|---|---|
| vPC Domain-ID | You should always use unique Domain-id's for all vPC pairs in a contiguous layer 2 domain. |
| vPC Peer-Link | vPC Peer-link should be a point-to-point connection. Peer-Link member ports can be 10/40/100GE interfaces. You should design peer-Link bandwidth as per the vPC. DONT's:- vPC imposes the rule that peer-link should never be blocking. |
| vPC Peer-Keepalive link | Use dedicated back to back links as a primary option and mgmt0 interface as secondary when using Nexus 7X00 and 9500 series. Use mgmt0 interface as a primary option and dedicated back to back links as a secondary option when using Nexus 9300/6000/5X00/3X00 series. Use layer3 infrastructure as a 3rd a option for all kind of Nexus Switches. |
| vPC Peer-Keepalive link – Dual Supervisors | Use the management interface when you have an out-of-band management network (management switch in between). DONT's:- When using dual supervisors and mgmt0 interfaces to carry the vPC peer-keepalive, DO NOT connect them back to back between the two switches. |
| Spanning Tree (STP) | All switches in Layer 2 domain should run either Rapid-PVST+ or MST. You should always set the vPC domain as the STP root for all VLANs in that domain. DONT's:- Do not disable spanning-tree protocol for any VLAN. |
| vPC Peer-Gateway | Always configure vPC Peer-gateway under vPC domain. N7k(config-vpc-domain)# peer-gateway It makes a vPC switch as the active gateway for packets addressed to the peer router MAC. It keeps forwarding of traffic local to the vPC node and avoids the use of the peer-link. It also allows Interoperability with features of some NAS or load-balancer devices. |
| vPC Peer-switch | Always configure vPC Peer-switch under vPC domain. N7k(config-vpc-domain)# peer-switch Peer-Switch makes the vPC peer devices to appear as a single STP root. BPDUs processed by the logical STP root formed by the 2 vPC peer devices. |
| PVLAN on vPC | PVLAN configuration across both VPC switches should be identical. Note- PVLAN configuration not supported on Peer-Link. |
| vPC auto-recovery | Always enable auto-recovery. Nexus(config)# vpc domain 1 Nexus(config-vpc-domain)# auto-recovery Auto-recovery addresses two cases of single switch behavior --> Peer-link fails and after a while primary switch (or keepalive link) fails --> Both VPC peers are reloaded and only one comes back up. |
| Object-tracking | It is good practice to configure Object Tracking as per your company's SLA. vPC object tracking, tracks both peer-link and uplinks in a list of Boolean OR Object Tracking triggered when the track object goes down. Suspends the vPCs on the impaired device. Traffic forwarded over the remaining vPC peer |
| Spanning Tree Bridge Assurance | STP Bridge Assurance is enabled by default on vPC Peer-Link. DONT's:- DON’T disable Bridge Assurance on vPC Peer-link. NO Bridge Assurance on vPC member ports (even with peer-switch) |
| Unidirectional Link Detection (UDLD) | UDLD only in normal mode on vPC member ports if required. UDLD is a Lightweight Layer 2 failure detection protocol. UDLD is Designed for detecting, One-way connections due to physical or soft failure and Mis-wiring detection (loopback or triangle). DONT's:- UDLD is NOT recommended on vPC peer-link. UDLD is NOT recommended on vPC member ports if LACP is used. |
Acronyms used in this blogpost
- vPC: Virtual Port-Channel
- VSS: Virtual Switch System
- UDLD: Unidirectional Link Detection
Cisco vPC Quiz
Conclusion
In this article, we discussed Cisco vPC, its brief history, and its benefits, and then we explained each vPC architecture component in detail. In addition, we also looked into vPC configuration nexus 9000 and important show and debug commands to verify and troubleshoot any vPC deployment issues. Finally, we ended the article with a Cisco vPC quiz. I hope you liked the article; please share it and subscribe to the mailing list to receive networking tips, tricks, and news.
Frequently Asked Questions About Cisco VPC
Is vpc cisco proprietary ?
What is vpc cisco?

Cisco vPC is a Cisco Nexus Switch-specific feature that provides the capability to the links/cables of the third or downstream device that are physically connected to two different Cisco Nexus Switches to appear as a single port channel. The third device in this case can be a switch, server, or any other networking device that supports port channels. A vPC can provide Layer 2 multipathing, which creates redundancy and increase the bisectional bandwidth by enabling multiple parallel paths between the nodes.