How to Configure a Secure Site-to-Site VPN on Cisco Firepower Complete Guide
Learn how to configure a secure site-to-site VPN on Cisco Firepower with a step-by-step guide covering policy-based and route-based VPNs, NAT, routing, and troubleshooting.

Learn how to configure a secure site-to-site VPN on Cisco Firepower with a step-by-step guide covering policy-based and route-based VPNs, NAT, routing, and troubleshooting.

Discover legal and ethical ways to implement internet monitoring for better compliance and efficiency.

Outdated Wi-Fi security? Learn why WPA2 or WPA3 are essential upgrades for protecting your network.

Maximize your Wi-Fi security with WPA3. Learn the benefits and how to upgrade for robust protection.

Our updated 2026 guide to the best parental control routers compares Wi‑Fi 6 and Wi‑Fi 7 options, subscription needs, ports, and mesh notes—so you can keep your family safer online without surprises.
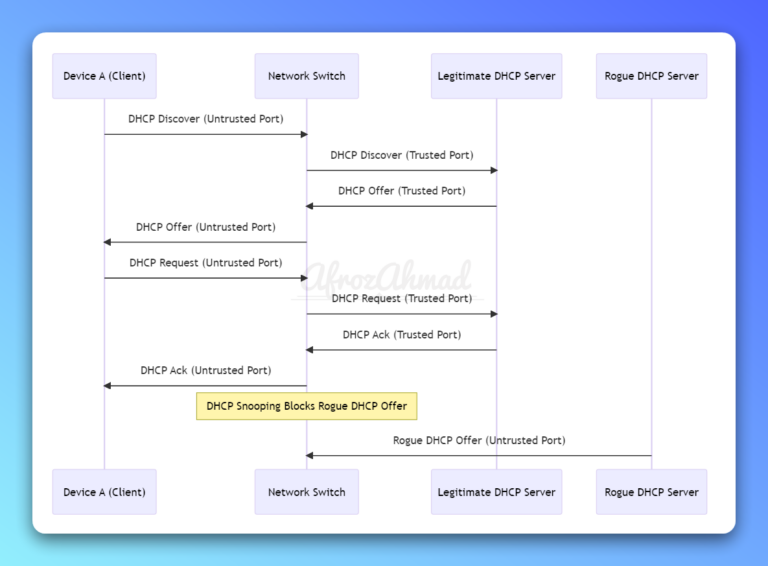
Discover what is DHCP Snooping and its significance in network security. Learn how it prevents DHCP-based attacks and rogue servers in our comprehensive guide.
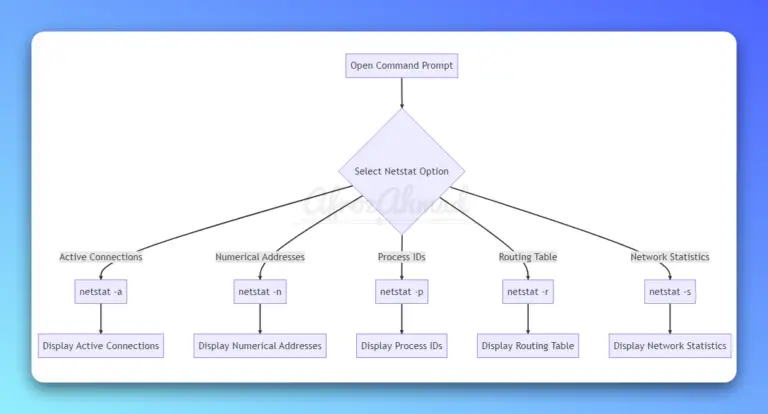
A practical guide to the netstat command across Windows, Linux, and macOS—with quickstart examples, accurate flags, and modern ss/iproute2 equivalents.
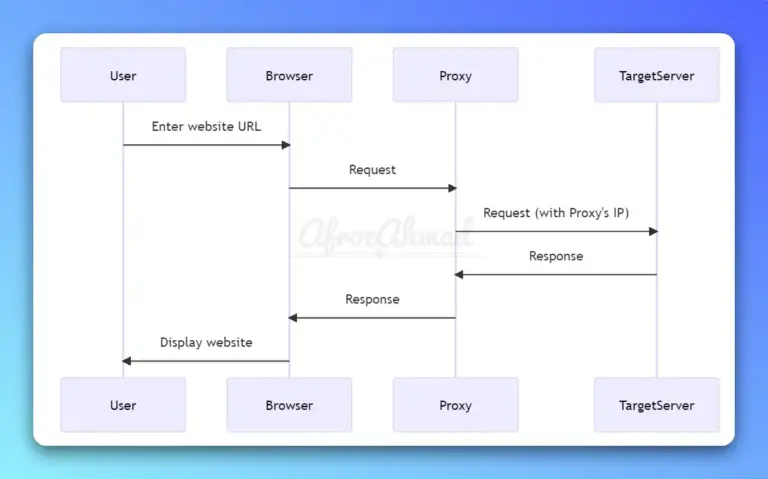
This comprehensive guide will walk you through the ins and outs of proxies, from understanding how they work and their primary purpose to exploring their usage, drawbacks, free, open-source, and paid options and alternatives.
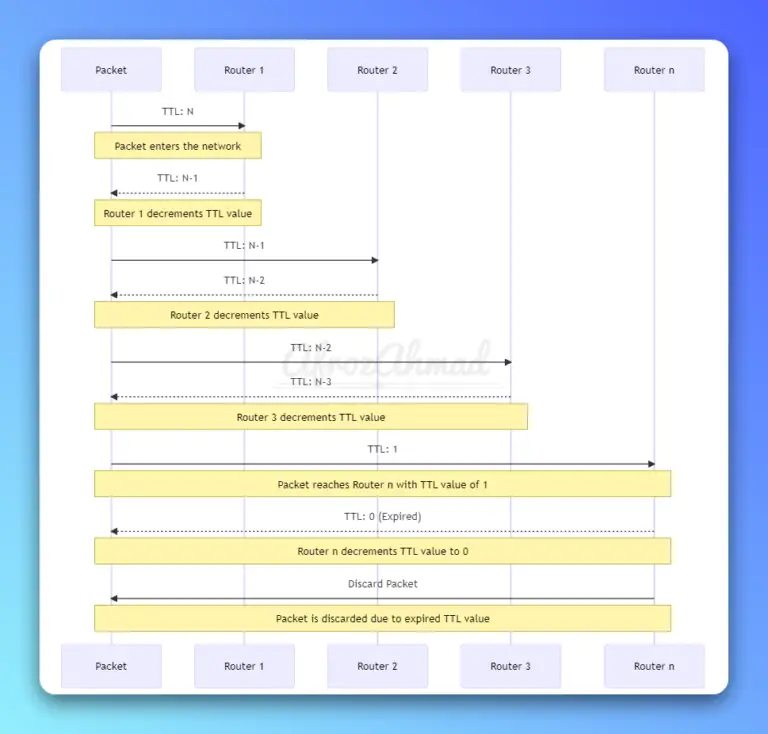
Explore Time To Live (TTL) in computer networking, its purpose, mechanism, implementation in protocols, troubleshooting, real-world examples, and best practices.
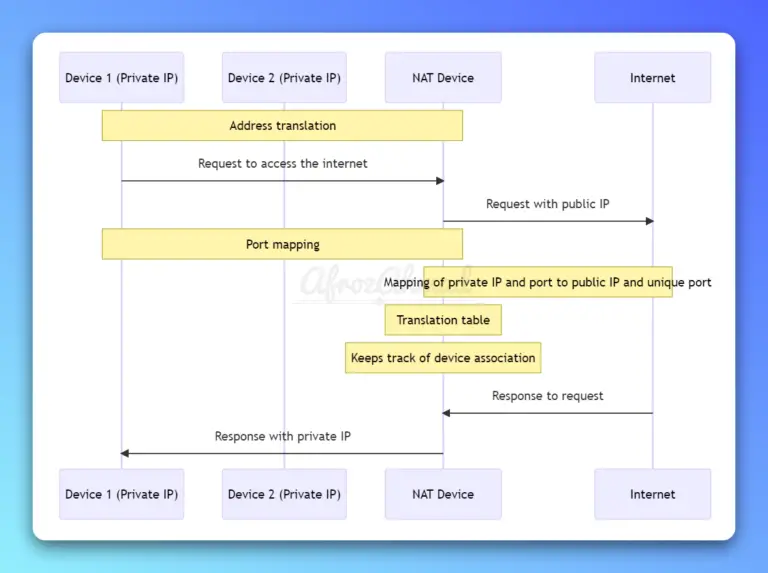
Explore Network Address Translation (NAT) in computer networking, its purpose, types, benefits, limitations, and real-world applications. Understand NAT's role in IPv4 and IPv6 networks.