Is 1000 Mbps Fast Internet? (The Gold Standard of Internet Speeds)
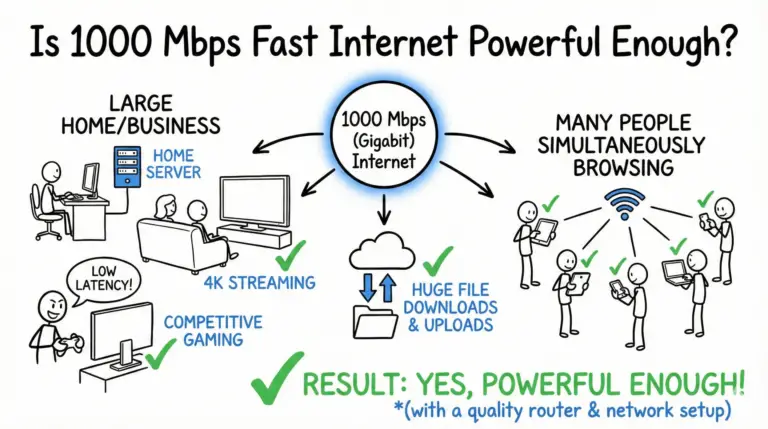
In this article, we will dive into the world of 1000 Mbps, aka gigabit internet, and explore the question: Is 1000 Mbps fast Internet speed?

In this article, we will dive into the world of 1000 Mbps, aka gigabit internet, and explore the question: Is 1000 Mbps fast Internet speed?
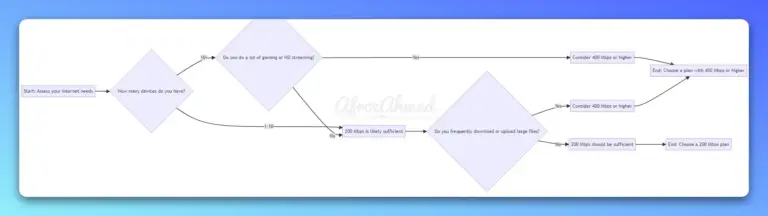
200 Mbps is fast for most households. It easily handles multiple HD streams and everyday work-from-home tasks, but many concurrent 4K streams, heavy uploads, and cloud gaming can push you toward 300–500+ Mbps—especially on plans with limited upload speed.
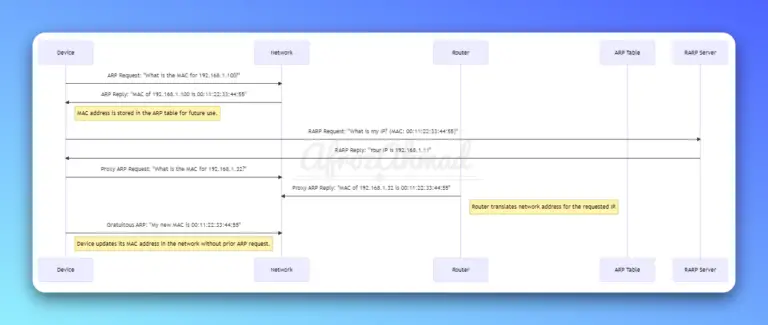
In this article, we delve into the specifics of networking protocols like ARP (Address Resolution Protocol), RARP (Reverse Address Resolution Protocol), Proxy ARP, and GARP (Gratuitous Address Resolution Protocol).
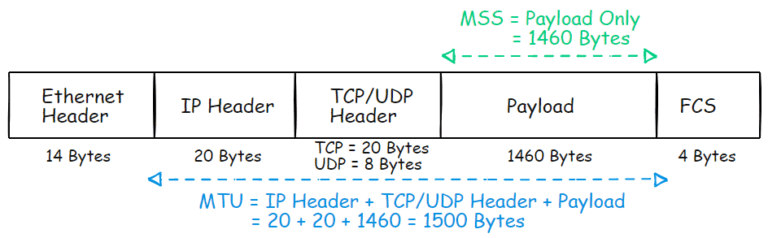
Want to know the difference between MTU vs MSS? Read on to know.
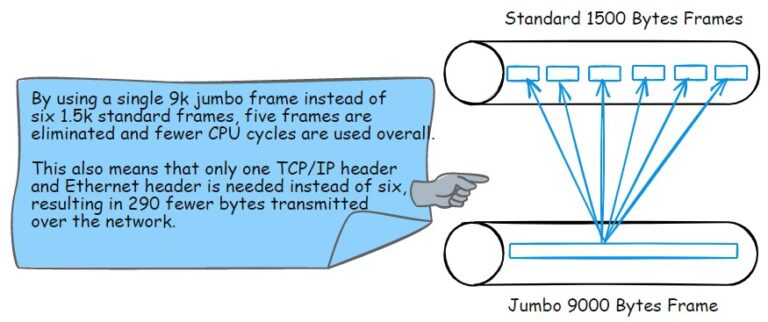
By the end of this article, you should have a clear understanding of MTU, Jumbo Frames, and MSS and how they influence your network's efficiency and performance.
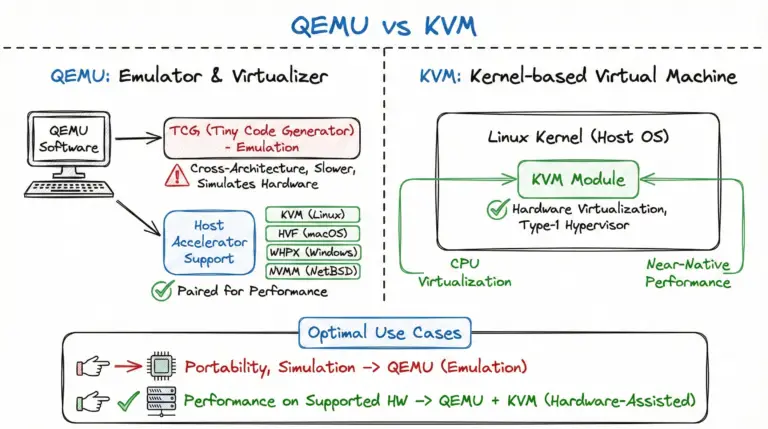
Understand the real differences between QEMU and KVM, how accelerators like KVM, HVF, WHPX, and NVMM change performance, and when to use QEMU alone vs QEMU+KVM.
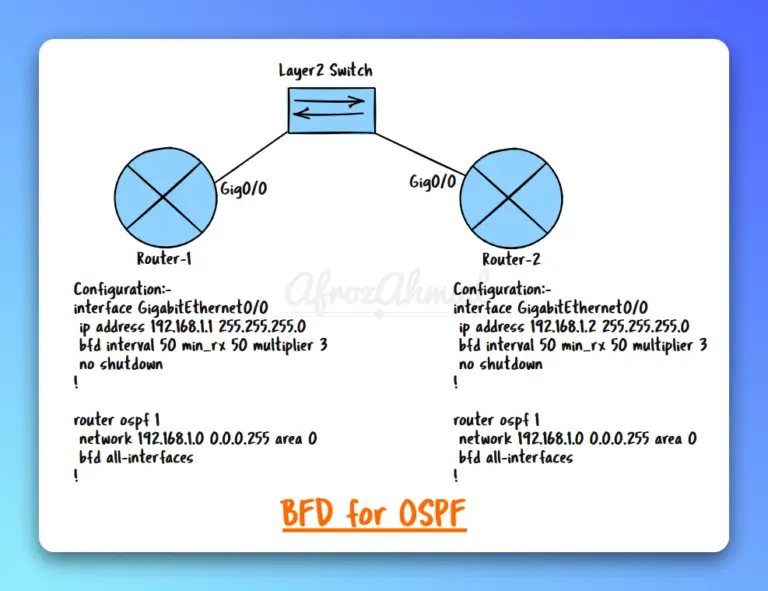
In this article, we will delve into the details of BFD (Bidirectional Forwarding Detection), including how it works, its configuration, use cases, best practices, integration with various networking protocols, and more.
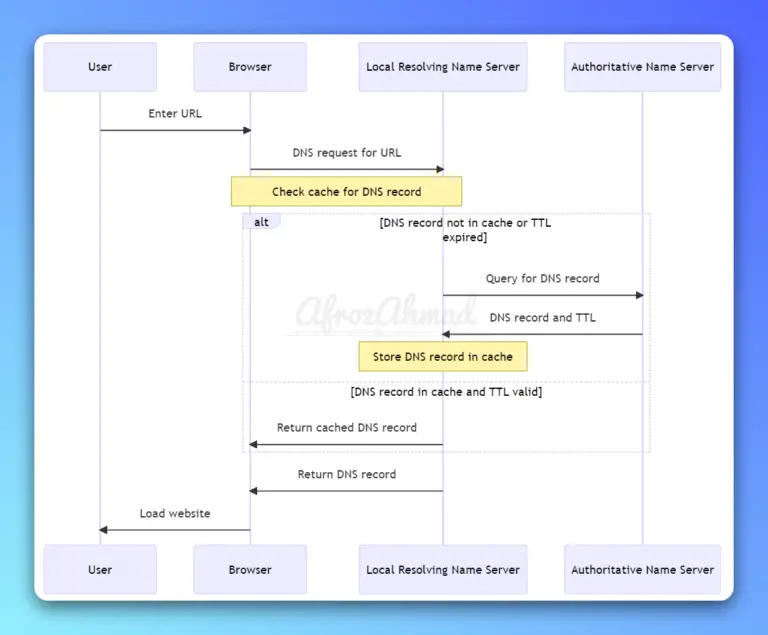
Discover everything you need to know about DNS TTL, including what is TTL in DNS, its purpose, how it works, best practices, troubleshooting, and how to optimize it for your domain.
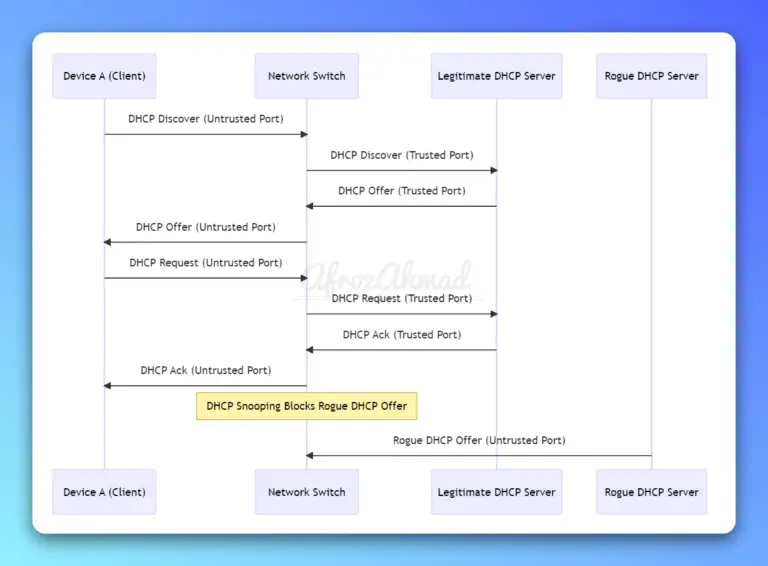
Discover what is DHCP Snooping and its significance in network security. Learn how it prevents DHCP-based attacks and rogue servers in our comprehensive guide.
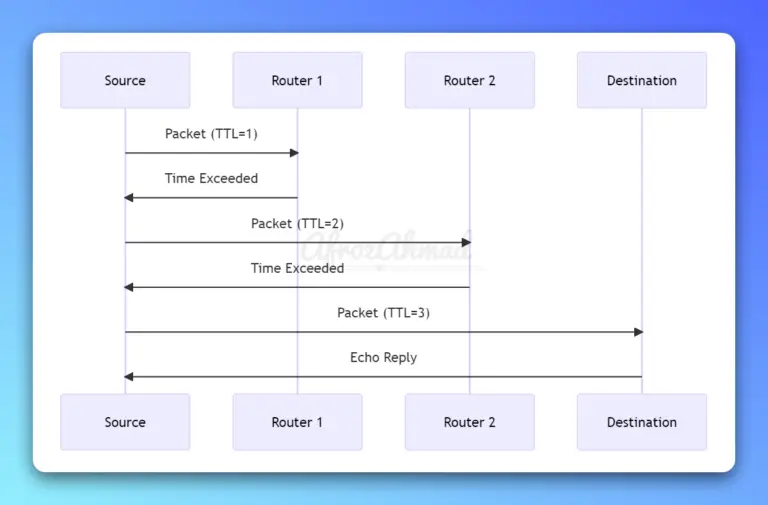
Discover the power of traceroute in this comprehensive guide, covering its purpose, usage across platforms, reading outputs, response types, and network troubleshooting. Unravel the complexities of this essential network diagnostic tool.