Understanding VLANs (Virtual Local Area Networks) and Private VLANs unlocks advanced network segmentation capabilities, enhancing security, manageability, and performance.
Essentially, VLANs split a single physical network into multiple logical segments, each isolated from the others to minimize broadcast traffic and increase security without the need for additional hardware. Private VLANs take this further by restricting communication within a VLAN for tighter security.
In this article, we will discuss the nuts and bolts of VLANs and Private VLANs, their advantages, configuration steps, and how they fundamentally differ from traditional LANs, equipping you with the knowledge to leverage these technologies effectively in your networking environment.
What are VLANs – Infographic
A Brief History of How we evolved from Hub to a Switch and then to VLANs
People commonly used network hubs in the early days of networking to connect devices to a local area network (LAN). Because these devices were not intelligent, they sent every packet they received to every other device linked to them, creating a big broadcast domain that was extremely “noisy.”
Hubs also had a single broadcast domain, meaning a Hub will deliver all traffic to all connected devices at once. Furthermore, all of the ports on a hub (in those days) were all part of a single collision domain, and if two devices attempted to communicate on the network simultaneously, their packets would collide. As a result, they would have to resend those packets to the other device.
As networks evolved, network devices became more intelligent, and switches were introduced.
Each port on a switch is in its own collision domain, and many devices connected to a switch can send packets simultaneously across the same port on the switch. Additionally, switches can track which ports are in use and which devices are connected to them, and it builds a table called MAC address table.
Switches do not flood packets to all ports except for the ports to which a device is connected, reducing network traffic. But, the switch continues to flood broadcast or unicast packets, and for the packets, it doesn’t know the MAC of the intended recipient.
Switches are still limited to a single broadcast domain, which means that switch will still send broadcast packets to all ports. Therefore, you need to do network segmentation on a device-by-device basis. If you want to distinguish between different groups of users on the network, you have to link them to separate switches.
Although this is not a significant issue on smaller networks, it is wasteful on larger networks. So, not anymore, Welcome to the world of virtual local area networks (VLANs).
What are VLANs and what are VLANs used for?
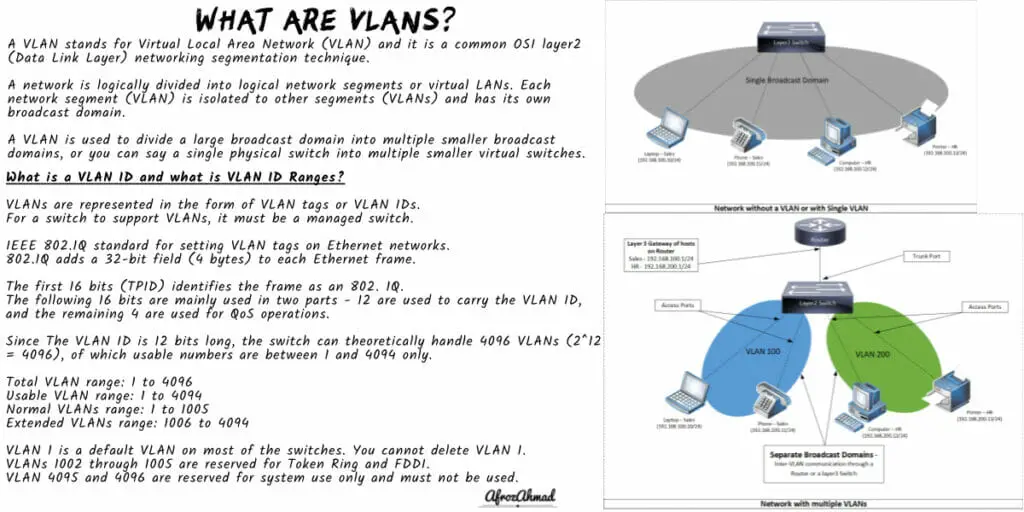
A VLAN stands for Virtual Local Area Network (VLAN) and it is a common OSI layer2 (Data Link Layer) networking segmentation technique.
A network is logically divided into logical network segments or virtual LANs. Each network segment (VLAN) is isolated to other segments (VLANs) and has its own broadcast domain.
A VLAN is used to divide a large broadcast domain into multiple smaller broadcast domains, or you can say a single physical switch into multiple smaller virtual switches.
Let us take an example:-
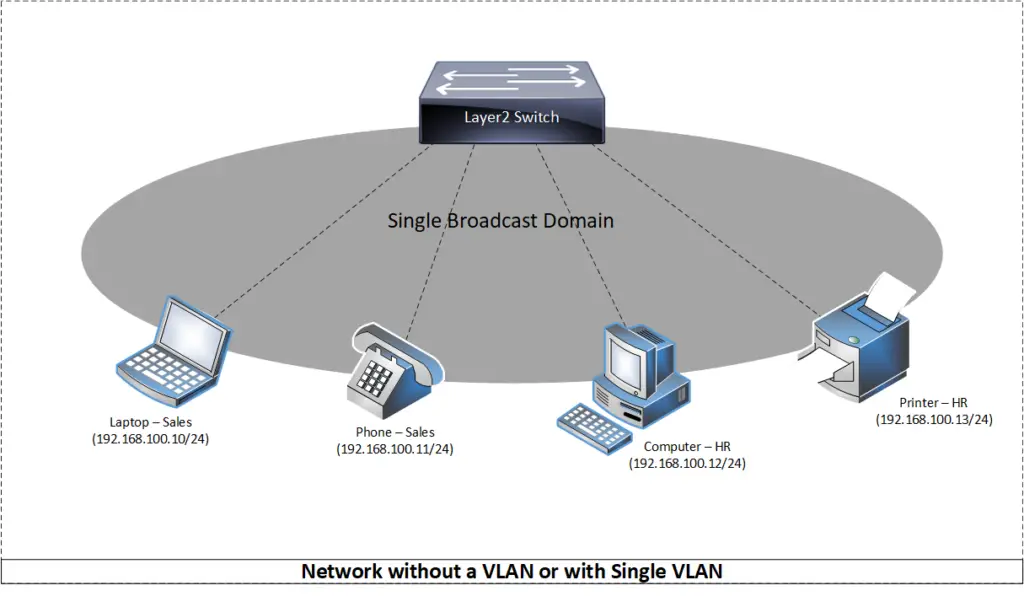
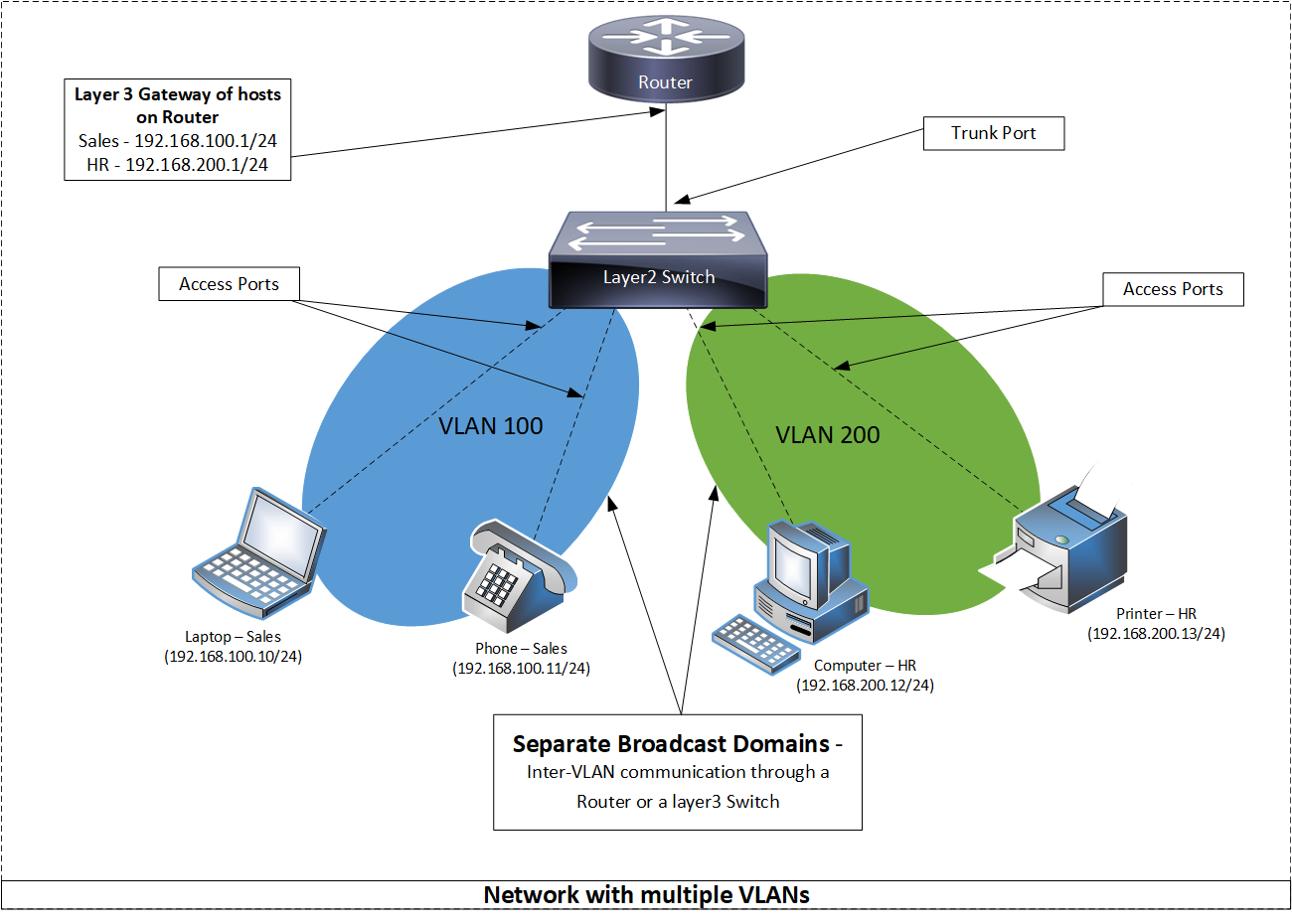
In the first diagram, the switch’s ports are all configured without a VLAN. This means that all hosts (laptop, phone, computer, printer) can directly communicate and hear each other’s broadcast traffic.
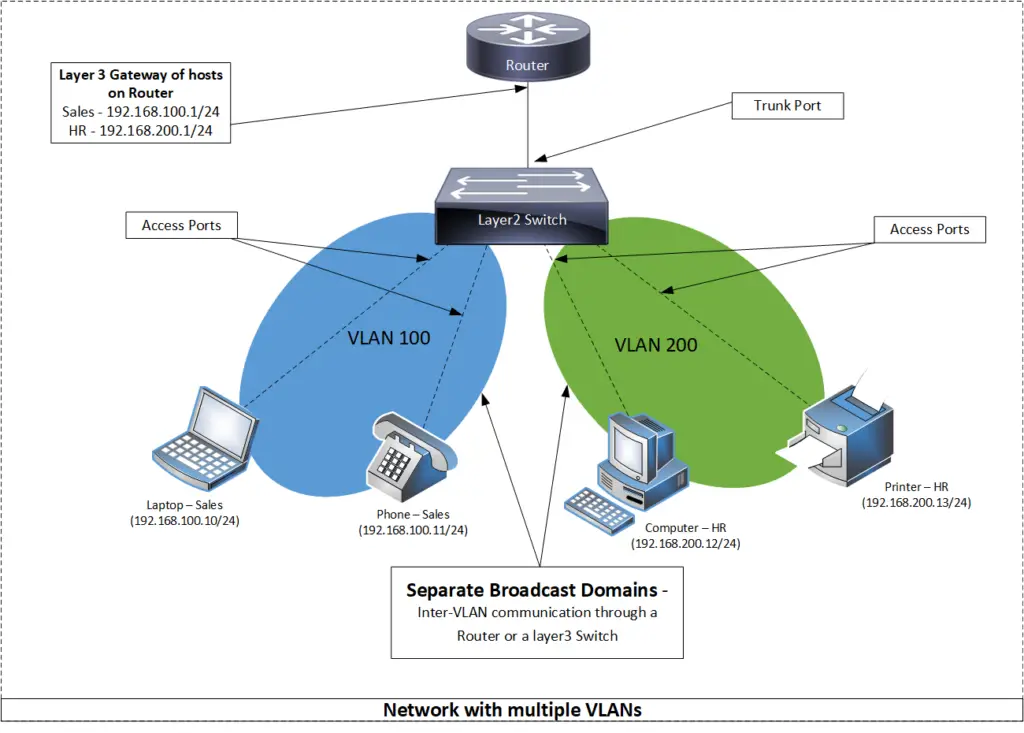
In the second diagram, we have segmented the existing networks into two VLANs (100 and 200). Now each VLAN has its own broadcast domain, and they can talk to devices within the same VLAN (VLAN 100 can talk to devices in VLAN 100) but they cannot talk to a different VLAN (VLAN 100 cannot talk to VLAN 200) without a layer switch or a router.
What are the advantages or benefits of using VLANs
- Security and Manageability – VLAN provides logical segmentation within a network which gives more control over which device is allowed to talk to another device. In addition, VLANs can only talk to each other by using a layer3 router or switch only, providing better network security and manageability. The general rule is devices that belong to the same VLAN can talk to each other however devices in different VLANs require a layer device to talk.
- Better Flexibility and Scalability – VLAN increases computer networks’ flexibility, scalability, and performance by creating smaller, more intimate networks based on departments, functions, teams, etc.
- Reduced Cabling – VLAN is a way to divide networks without running cables to separate hardware.
- Reduced Hardware – VLAN makes one Physical Switch into many Virtual Switches. So, If you have a single switch with enough physical ports and only need segmentation, then by using VLANs, you can easily achieve it without additional hardware, which can save you some money.
- No physical Boundaries – VLANs are logical entities; they are not constrained to a single device’s physical location and span many switches.
- Reduced Congestion – Individual VLANs work as distinct LANs and share traffic among each other without the need for another layer3 device, reducing congestion.
- Improve Overall performance of Network – With a VLAN you can group devices together which talk to each other more often by putting them in a single LAN, which in turn increases the overall performance of the network.
- Terminal reallocations become easy.
- Virtual LANs simplify the process of connecting devices that are on different parts of the same LAN (Local Area Network) by giving you a framework to group them together.
Learn how to manage VLANs efficiently through VTP.
What are the Disadvantages of using VLAN
- A packet can leak between VLANs. A virus in one system can infect a whole logical network.
- There are various VLAN-based attacks hackers use for cyber attacks, a network administrator must be aware of those attacks and use different security strategies to prevent such attacks.
- VLANs have a hard limitation of just 4,096 VLANs per switching domain, major hosting providers often need to allocate tens or hundreds of VLANs per client. In those situations, Other protocols, such as VXLAN, NVGRE, and Geneve, provide larger tags, and the ability to tunnel Layer 2 frames within Layer 3 (network) packets must be used.
- VLANs cannot talk to each other without a Routers or a layer3 device.
What are Private VLANs and What are Private VLANs used for?
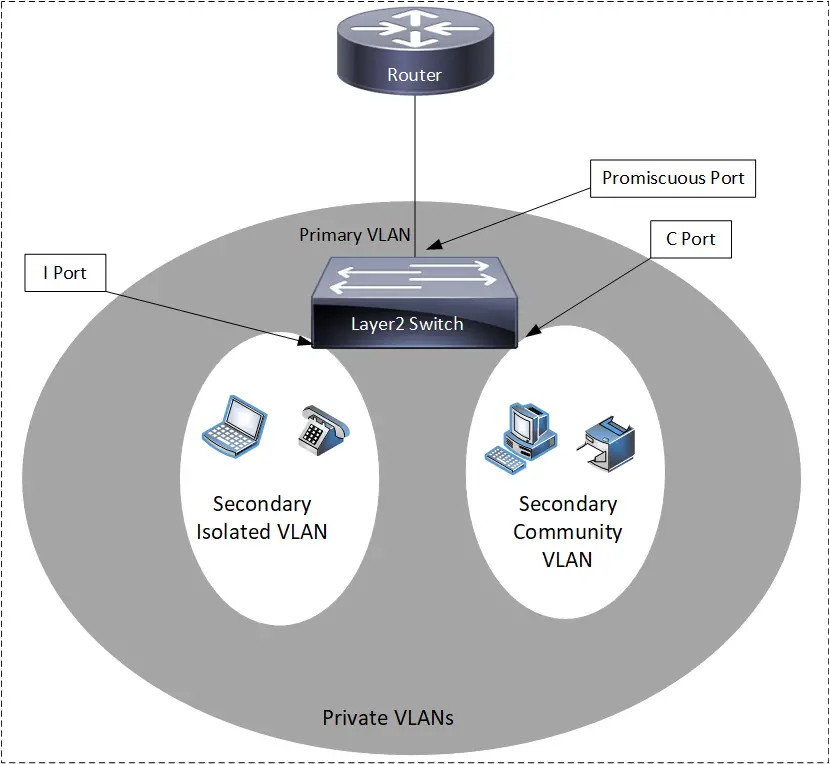
- Traditional VLANs have limitations and they don’t work if you want to restrict one host to talk to another host within a VLAN, you need Private VLANs to achieve this.
- A Private VLAN is a VLAN collection, a primary VLAN, and one or more secondary VLANs.
- A Primarily VLAN is a normal VLAN. It is promiscuous and able to communicate with any secondary VLAN or any traditional VLAN.
- The secondary VLANs are linked to the Primary VLAN. These secondary VLANs are used to restrict/separate devices from each other within a VLAN.
- Secondary VLANs come in two flavors, namely Community and Isolated.
- Community VLANs – Devices within a single community VLAN can communicate with each other, but they are not able to communicate with other community VLANs and Isolated VLANs.
- Isolated VLANs – Devices in Isolated VLAN are totally restricted and they cannot communicate to any Community VLAN or even any Isolated VLAN.
- The primary VLAN can connect to everything. That’s why routers are connected here. This allows segregated or devices in secondary VLANs to share internet connections and links and can still have all isolation policies intact.
- Promiscuous Ports are primary VLAN ports (P-Ports).
- A layer-3 switch’s primary VLAN can have an SVI (Switch Virtual Interface), however, Secondary VLANs cannot have SVIs.
- Secondary VLAN ports are called Host Ports because this is where hosts connect.
- An I-Port is a host port in an isolated VLAN.
- A C-Port in a community VLAN host port.
I highly recommend reading more about layer 3 SVI’s and router on a stick configuration to digest the full concept.
LAN vs VLAN
| Basis for comparison | LAN | VLAN |
|---|---|---|
| Acronym | LAN - Local Area Network | VLAN - Virtual Local Area Network |
| Commonly used Devices | Hub, Repeaters, Switches, Wireless Access Points, Printers, and Routers. | Switches and bridges. |
| Broadcast control | Each device on the LAN receives a broadcast of the frame. | Only specific devices in that particular VLAN (broadcast domain) receives the broadcast of the frame. |
| Latency | The latency of LAN is usually high compared to VLAN. | The latency of VLAN is usually less compared to LAN. |
| Security | The LAN is not sufficiently safe, and security measures are only implemented at the router level. | The use of VLANs increases security by restricting frames to the specific broadcast domain. |
| Efficiency, Flexibility and scalability | LAN only filters the frames and is less scalable than VLAN. | More Flexible and scalable, The VLAN specifies the port and protocols that is used to identify a frame. |
| Cost | High cost as more devices are required to segregate users. | Less costly as , one switch can be virtually divided into multiple VLANs. |
| Failure domain | If a switch serving a user group breaks, they cannot be readily transferred to another switch. That makes LAN less efficient than VLAN. | If a switch servicing a user group fails, they can be moved to another switch with little configuration.Outperforms a LAN in both performance and efficiency |
| Networking Mechanism (Protocols used) | Token ring and FDDI. | ISL, Dot1Q, VTP, etc. |
| Composed of | A LAN can be composed of Multiple VLANs. | a VLAN can span multiple LAN if required. |
| Physical vs Virtual | LAN is Physical. | A VLAN is Virtual. |
How VLANs work?
To understand how VLANs work, we have to compare two scenarios, one without a VLAN tag and the other with a VLAN tag.
Before VLAN tags, a switch’s decision was simple:
- If the switch received a broadcast packet or unicast packet but didn’t know the destination MAC address, it would flood it to all other ports except the one port that received the packet.
- If the switch gets a unicast packet and knows the target MAC address, it will only forward it to that port.
With VLANs, a switch is more intelligent and has a lot to do now:
- For example, is the destination packet on the same VLAN or a different VLAN?
- Is the Destination packet is on the same switch or another switch?
- What to do if it receives an untagged packet (no VLAN tag)?
- What to do if it receives a tagged packet (with VLAN tag)?
- What to do if it gets an untagged packet on a tagged port?
In short:-
- Each switch makes use of the VLAN tag (Valid Range is 1-4094) to keep each VLAN’s traffic isolated from other VLANs, forwarding it solely to the destinations that the VLAN has been configured for.
- Trunk links between switches are capable of supporting numerous VLANs, with the tag serving to keep them apart.
- As soon as the frame arrives at the target switch port, the VLAN tag is removed and the frame is ready to be transferred to the destination device.
What is a VLAN ID and what is VLAN ID Ranges
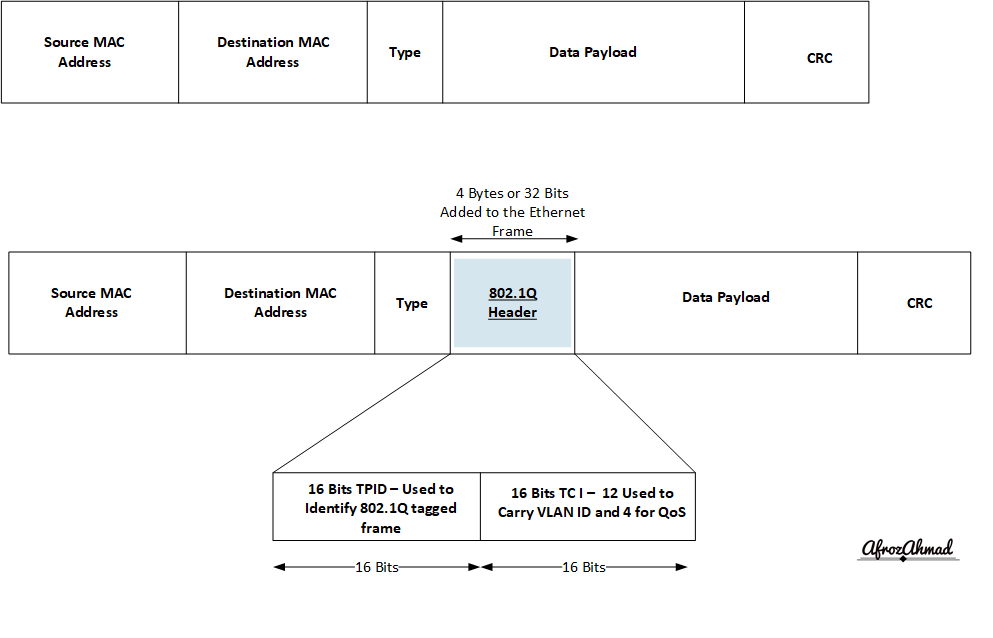
- VLANs are represented in the form of VLAN tags or VLAN IDs.
- For a switch to support VLANs, it must be a managed switch. Most networking device vendors, including Cisco, implement the IEEE 802.1Q standard for setting VLAN tags on Ethernet networks.
- 802.1Q adds a 32-bit field (4 bytes) to each Ethernet frame.
- The first 16 bits (TPID) contain the hardcoded number 0x8100 which identifies the frame as an 802. 1Q.
- The following 16 bits are mainly used in two parts, 12 are used to carry the VLAN ID, and the remaining 4 are used for QoS operations.
- Since The VLAN ID is 12 bits long, the switch can theoretically handle 4096 VLANs (2^12 = 4096), of which usable numbers are between 1 and 4094 only.
- Total VLAN range: 1 to 4096
- Usable VLAN range: 1 to 4094
- Normal VLANs range: 1 to 1005
- Extended VLANs range: 1006 to 4094
- VLAN 1 is a default VLAN on most of the switches. You cannot delete VLAN 1.
- VLANs 1002 through 1005 are reserved for Token Ring and FDDI.
- VLAN 4095 and 4096 are reserved for system use only and must not be used.
Types of VLANs
The following are the most common types of VLANs. VLANs are classified into several categories.
Static or Port-Based VLAN
- Static VLANs are also known as port-based VLANs – They require a network administrator to statically assign specific VLANs to a network switch port. Any device that plugs into that port joins that particular VLAN’s broadcast network.
- The issue with this network is knowing which ports belong to which VLAN because a switch’s physical port cannot tell you a VLAN’s membership.
Dynamic or Protocol Based VLAN
- In a dynamic VLAN setup, network membership is defined by device attributes/characteristics rather than switch port location. As an example, a dynamic VLAN can be defined with network account names or MAC addresses.
- Dynamic VLAN handles traffic using a protocol that defines filtering criteria for untagged packets. In this VLAN, the packet carries the layer-3 protocol to determine VLAN membership. It works with multiple protocols.
Default VLAN
If you have a switch that has default VLAN 1 assigned to it, all of its ports are automatically assigned to the same broadcast domain. Any network device connected to a switch port can communicate with other devices on other switch ports using default VLAN. VLAN 1 cannot be renamed or deleted makes it unique.
Native VLAN
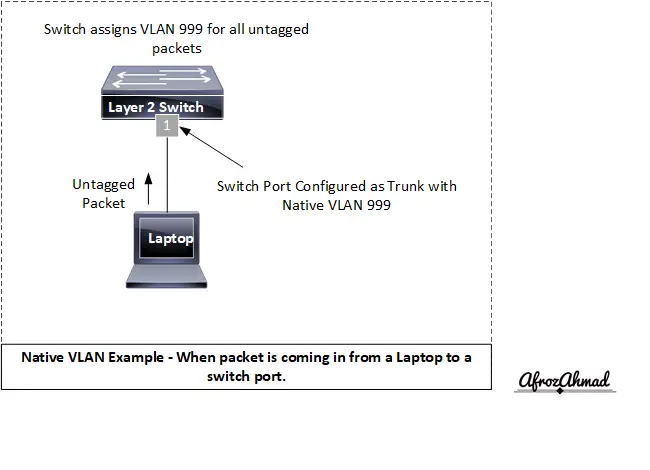
Native VLAN is exclusively assigned to an 802.1Q trunk port and is used to identify traffic that originates at each end of a trunk port. The 802.1Q trunk port puts untagged traffic (traffic that does not have any VLAN tag) to the native VLAN, which is the default setting. It is recommended that the native VLAN be configured as an unused VLAN.
Data VLAN
Data VLAN divides the network into two groups. A user group and a device group. The data VLAN, often known as a user VLAN, is solely for user-generated data. This VLAN has only data. It does not transport management or voice traffic.
Voice VLAN
Voice VLAN is set up for voice traffic. Voice VLANs usually have priority over other network traffic. We need a distinct voice VLAN to assure VoIP quality (latency of less than 150 ms over the network) while preserving capacity for other applications.
Please note: – You can assign two VLANs ( a Data VLAN and a Voice VLAN) on a single switch port on cisco switches.
Management VLAN
A management VLAN is set to provide access to a switch’s management capabilities (traffic like system logging, monitoring). By default, VLAN 1 is the administration VLAN (VLAN 1 would be a bad choice for the management VLAN). If the administrator has not configured a unique VLAN to serve as the management VLAN, any of the switch VLANs may be defined as the management VLAN. This VLAN ensures that management bandwidth is available even during periods of high user demand.
VLAN Configuration Steps
Network administrators create new VLANs as follows:
- Define VLAN’s purpose, like whether they will be used for Data or Management, or Voice.
- Then tag the switch port with a Valid VLAN number, do this for each type of VLAN.
- Then we do subnetting and allocate an IP subnet , mostly from private IP address range to each VLAN.
- Choose whether you will configure the switch device statically or dynamically. In static settings, each switch port gets a VLAN number. To create a dynamic VLAN, the administrator gives MAC addresses or usernames.
- If VLANs have to travel to another switch or router, make sure you configure the trunk between switches or towards the router and allow all necessary VLAN IDs.
- Configure VLAN routing as needed. A VLAN-aware router or a Layer 3 switch is required to configure two or more VLANs to communicate.
Please note: The administrative tools and interfaces utilized differ per equipment. Also, configuration syntax differs from vendor to vendor.
Cisco What are VLANs and How to create a VLAN on Cisco switch
- Switch1# configure terminal -> Enters global configuration mode.
- Switch1(config)# vlan vlan_ID –> Configures VLAN on a switch , VLAN ID can be between 1-4094
- Switch1(config-vlan)# –> Under Switch VLAN configuration
- Switch1(config-vlan)# end –> Return from config to Enable mode
- Switch1# show vlan [id | name] vlan_name –> Verify VLAN configured properly or not.
Sample VLAN Configuration:-
- layer2-Switch#configure terminal
- layer2-Switch(config)#vlan 100
- layer2-Switch(config-vlan)#vlan 200
- layer2-Switch(config)#int Fa0/1-2
- layer2-Switch(config-if)switchport mode access
- layer2-Switch(config-if)#switchport access VLAN 100
- layer2-Switch(config)#int Fa0/3-4
- layer2-Switch(config-if)switchport mode access
- layer2-Switch(config-if)#switchport access VLAN 200
- layer2-Switch(config)#int Fa0/8
- layer2-Switch(config-if)#switchport mode trunk
- layer2-Switch(config-if)#switchport trunk encapsulation dot1q
VLANs: Best Practices.
- Always change the default VLAN assigned by the device manufacturer to something per your company standards.
- It is advisable to change the default Native VLAN 1 to 999 or something different than 1 to safeguard switches with spoofing and other layer2 attacks.
- Make sure Native VLAN matches on both sides when connecting two switches through a Trunk configuration – VLAN hopping can happen when two native VLANs on opposite sides of a trunk don’t match. Hackers often use this to get into a network, and it’s a big security risk.
- Make sure you turn off DTP on a port:- The default switch port configuration uses the Dynamic Trunking Protocol (DTP) to figure out whether a port should be an Access Port or a Trunk Port, and it does this automatically. You can turn off DTP by setting the switchport to either “switchport nonegotiate” or “switchport mode trunk” or to “switchport mode access” or “no switchport.”
- Always Use 802.1q to tag packets. Cisco ISL is obsolete, so don’t use it.
- Any port that is not in use should be assigned to an unused VLAN and put into shutdown mode.
- Especially in high-risk environments, don’t rely solely on VLANs for security! Switch spoofing and double tagging are methods used to gain access to a VLAN. VLAN hopping, especially where trunks interconnect switches, can be used to cause a denial of service attacks.
Acronyms Used in the Blog
- LAN:- Local Area Network
- VLAN:- Virtual Local Area Network
- DTP:- Dynamic Trunking Protocol
- SVI:- Switch Virtual Interface
- TPID:- Tag Protocol identifier
Conclusion
In conclusion, in this article, we have discussed what are VLANs and how VLANs work. VLAN is a networking technique that splits a single broadcast domain into multiple broadcast domains for the ease of manageability, scalability, and security. It is a widely used feature, and all the vendors that make switches support VLANs, but you need to understand some basic terms and concepts before using this technology.
Please share so that it can reach out to the maximum number of people searching for this topic.
- MAC Address Filtering on Home Routers: A Comprehensive Guide - April 16, 2024
- Unlock the Power of USB Ports on Your Home Router | Enhance Your Network - April 15, 2024
- How to Configure Guest Networks on Home WiFi Routers: A Step-by-Step Guide - April 15, 2024