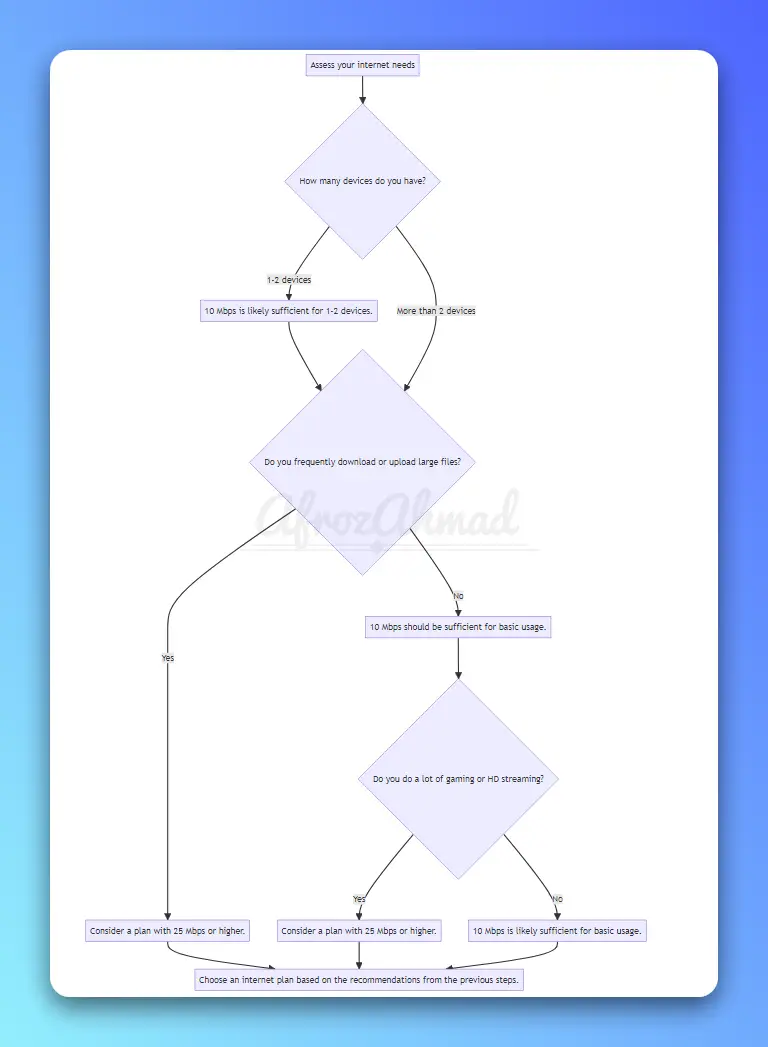
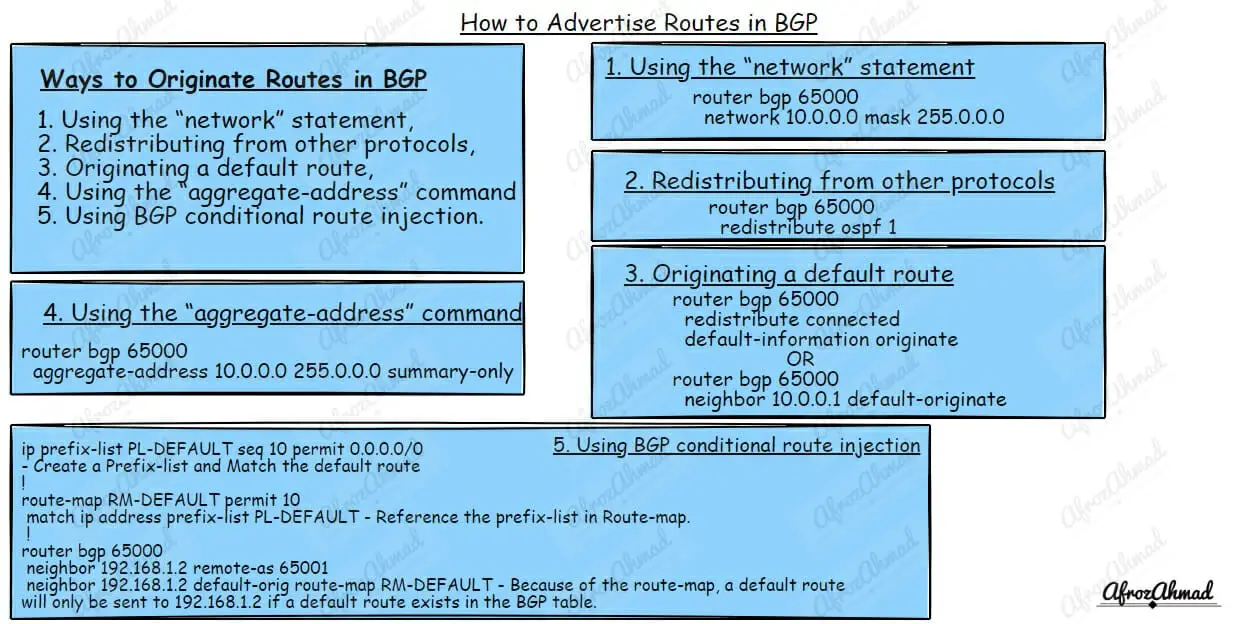
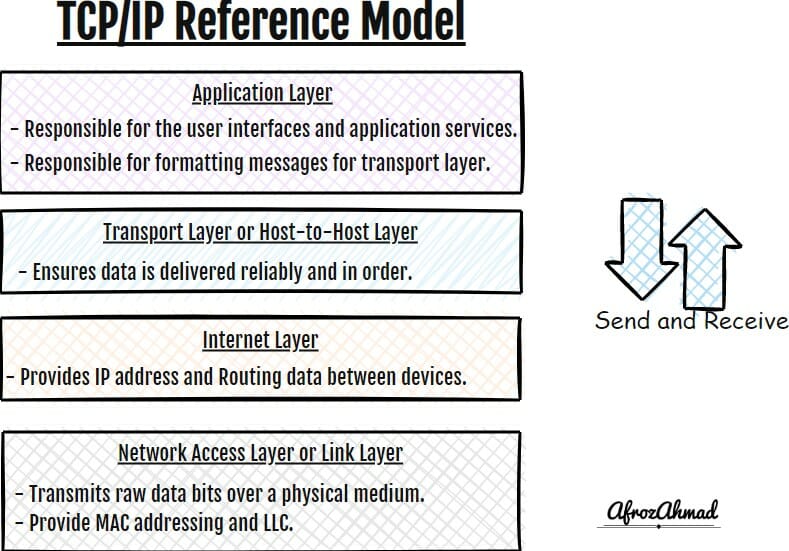
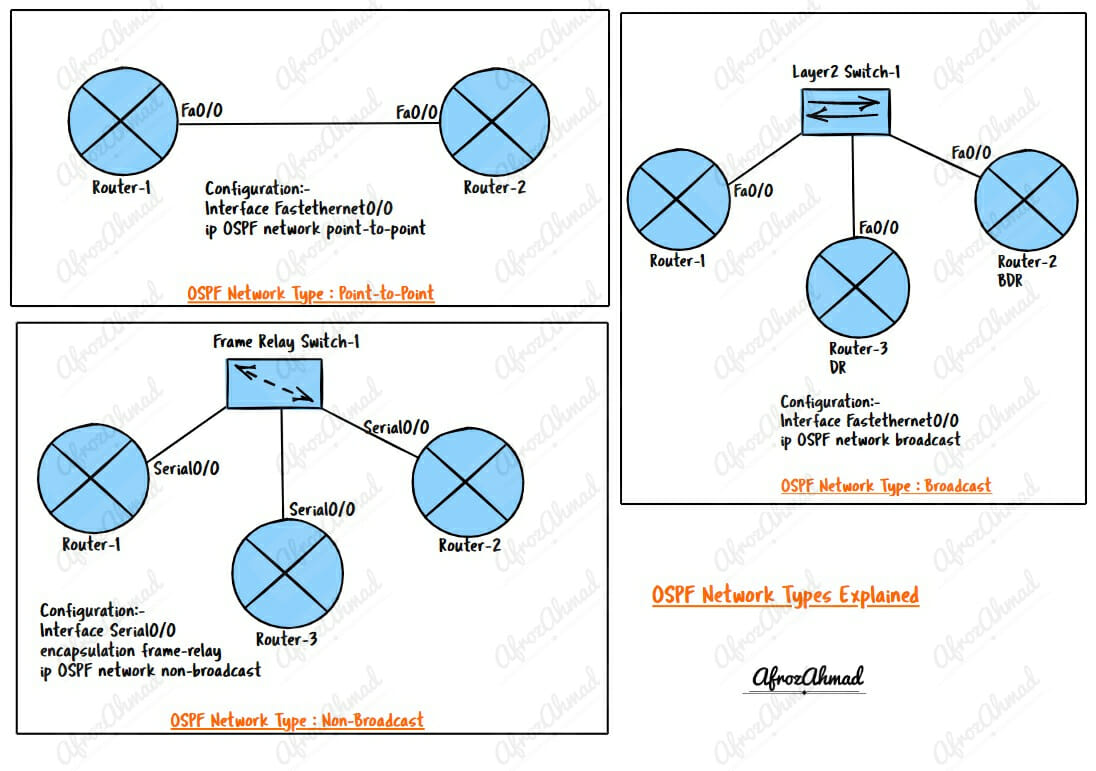
Internet Services, Modems & Routers, Tech Reviews, Computer Networking, Security, and more!

Afroz Ahmad – Main Author of AfrozAhmad.com
Welcome to Afroz Ahmad – I’ve been writing about computer network technologies on my blog since 2012. My name is Afroz Ahmad, and I am a seasoned Network Engineer and author of AfrozAhmad.com.
I’m a CCIE with more than 17 years of experience in Computer Networking, Data Centers, Telecom, Internet Services, and ISPs. Currently, I work as a Network Designer for a leading ISP equipment vendor. I share my expertise through my blog and courses, aiming to help people solve everyday internet issues, select the appropriate equipment for their tech needs, and simplify complex networking concepts for both beginners and experienced professionals.
Reach out to me with any questions you have on Computer Networking, Modems, Routers, Internet services, etc.